
Should you be monitoring ping?
Ping is one of those protocols that no one thinks about until it isn’t working and you’re trying to quickly troubleshoot connectivity between devices....

Ping is one of those protocols that no one thinks about until it isn’t working and you’re trying to quickly troubleshoot connectivity between devices....

I don’t know about you, but it seems like there’s news of some big data breach every other month. The hard truth is that...

I think I can safely assume that everyone knows the cautionary tale of the boy who cried wolf. If you don’t, the moral is...
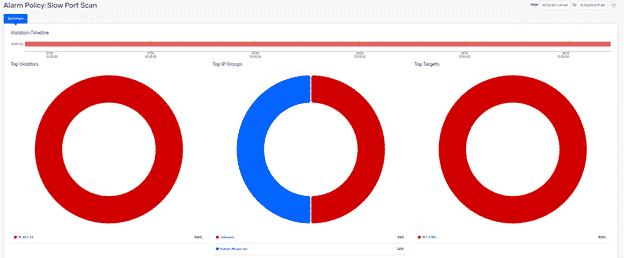
As enterprises adjust to the new normal and remote work, they are bracing for potential attacks resulting from employee carelessness. Bad habits, such as...

Even though most of us have looked at a calendar recently and thought, “I could have sworn we were in May, not October,” you...

I was recently able to explore the Splunk software development kit with a customer. This helped me to implement another way to get username...

A few years ago, we added a behavioral algorithm to Plixer Scrutinizer that looked at all the flow data that was collected and determined...
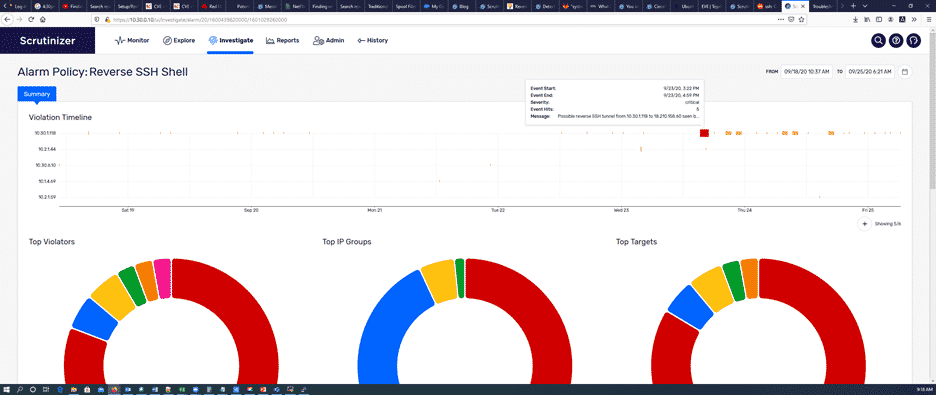
Today we are going to talk about Plixer’s new Flow Analytics algorithm, Reverse SSH Shell, which has been included in the latest Plixer Scrutinizer...

What is STIX/TAXII? STIX stands for Structured Threat Information Expression, which is an open-source language and serialization format used in sharing threat intelligence. Think...
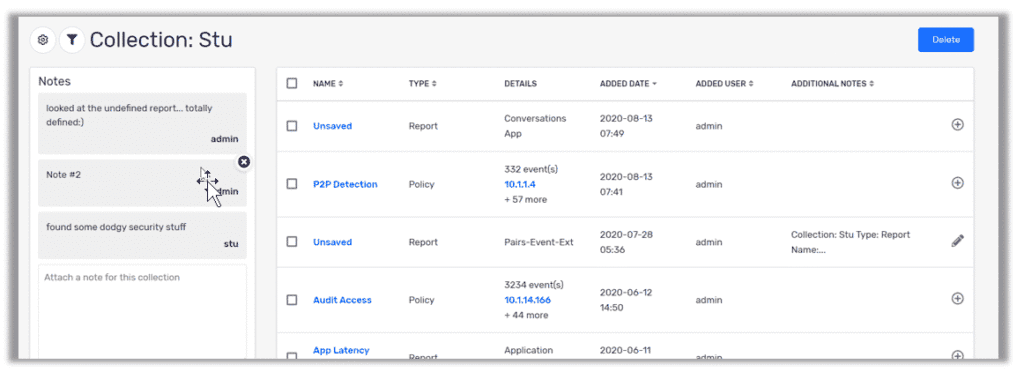
I can’t tell you how many calls I’ve been on where the NetOps and SecOps teams really don’t know what the other is doing....
Looking for documentation? Visit our documentation site