A few years ago, we added a behavioral algorithm to Plixer Scrutinizer that looked at all the flow data that was collected and determined if there was possible ICMP tunneling taking place. That algorithm alarmed if it determined that packet sizes were abnormal for ICMP traffic from a Windows or Linux platform.
Several customers found instant value in the ability to uncover this type of traffic behavior, but ultimately it was only providing a check for a single dimension related to suspicious ICMP behavior.
Welcome to Plixer Scrutinizer Version 19
Version 19 of Plixer Scrutinizer introduces a number of new checks for particular behavior metrics related to ICMP traffic.
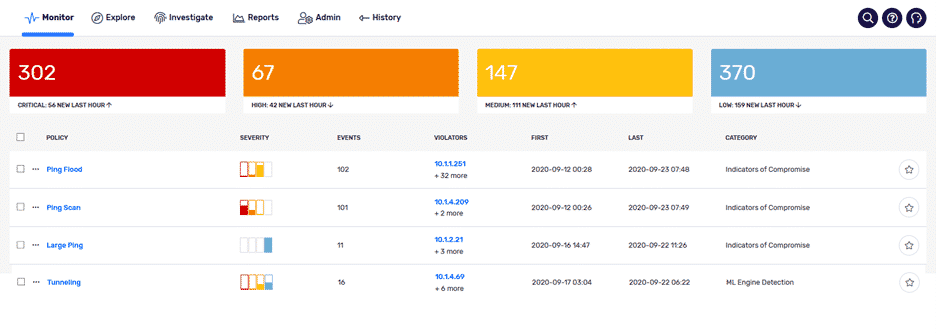
We can detect suspicious behaviors related to:
Ping scan or ping sweeps: Alerts when a host is suspected of performing a ping scan. A ping scan uses ICMP echo requests to discover what IPs are in use on a network. The behavior is commonly demonstrated by attackers attempting to find targets for compromise or lateral movement.
Ping floods: Alerts when a ping flood is detected. A ping flood is characterized as a large volume of ICMP echo requests intended to overwhelm the target’s ability to process legitimate traffic.
ICMP destination unreachable: Alerts when a large number of ICMP destination unreachable messages have been sent to the suspicious IP address.
ICMP port unreachable: Alerts generated when a large number of ICMP destination unreachable messages have been sent to the suspicious IP address.
Large ping: This was available in an earlier released version and was primarily used to detect possible tunneling. Alerts when it has been determined that based on the number of bytes and the number of packets, the packet size appears to be outside of the normal ICMP packet size.
Tunneling: With version 19 of Plixer Scrutinizer, we are introducing Plixer Security Intelligence: a dedicated machine learning appliance that ingests and analyzes data directly from Scrutinizer. By streaming flow data to our ML engine, we can analyze ICMP traffic on a number of different dimensions which allows us to understand:
- hosts trends
- number of hosts targeted
- variations in byte/packet counts
- size/duration
Collecting flows from your network devices provide valuable forensic visibility into any conversation traversing the network. We provide a solution that proactively alerts on suspicious traffic and has the traffic details needed to mitigate the incident.
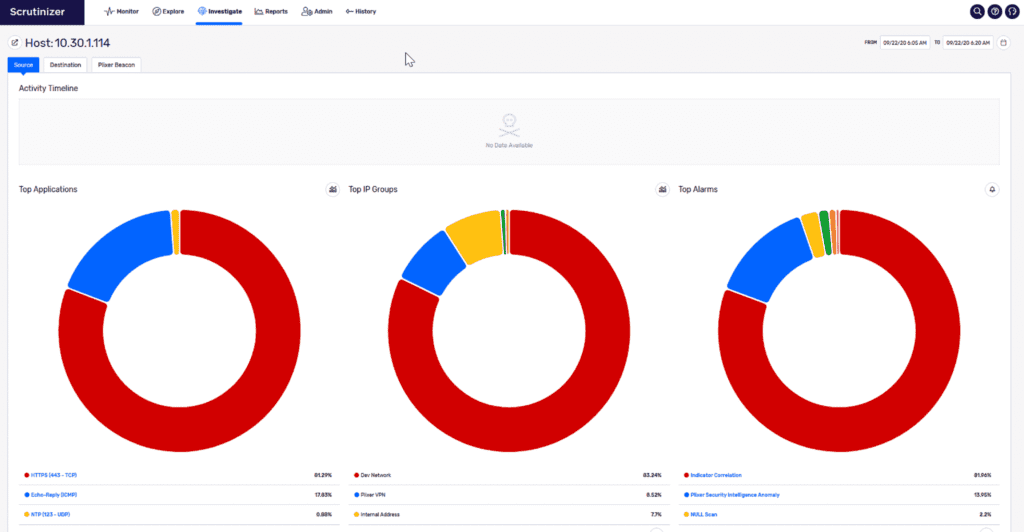
The administrator sees the alert, and a single mouse click provides overall insight regarding the alert.
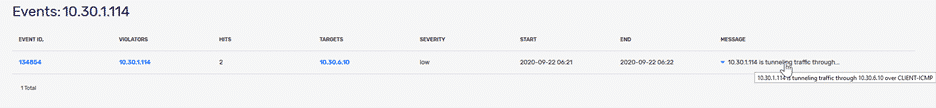
Who is the violator?
What network segment does this violator belong to?
What were the targets?
Any other correlating alarms for this host?
Do you need insight into suspicious ICMP traffic moving across your network? Contact our support team if you want to learn more or need help with alarm configurations.



