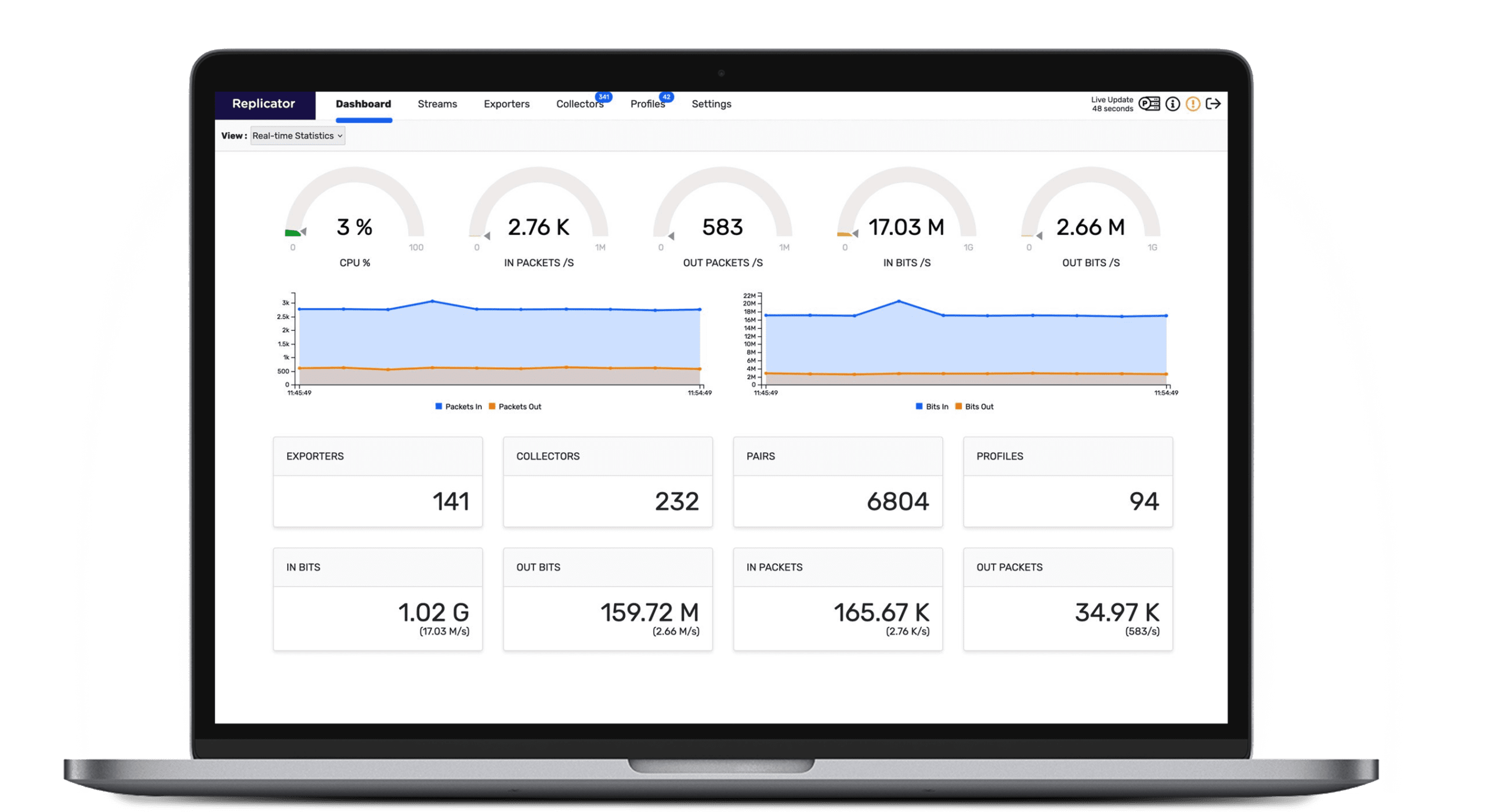
Plixer Replicator
Simple, Fast Network Data Replication
ANOTHER SUCCESS
FOR REPLICATOR
First National Bank of Pennsylvania Experiences 50% Faster Time-To- Resolution & Significant Cost Savings with Plixer Replicator.
SEE REPLICATOR
IN ACTION
Buying technology is often complicated and exhausting. We like to make it easy and straightforward with scheduling requests, discovery calls, Q&A with a sales engineer and much more.
What We Offer
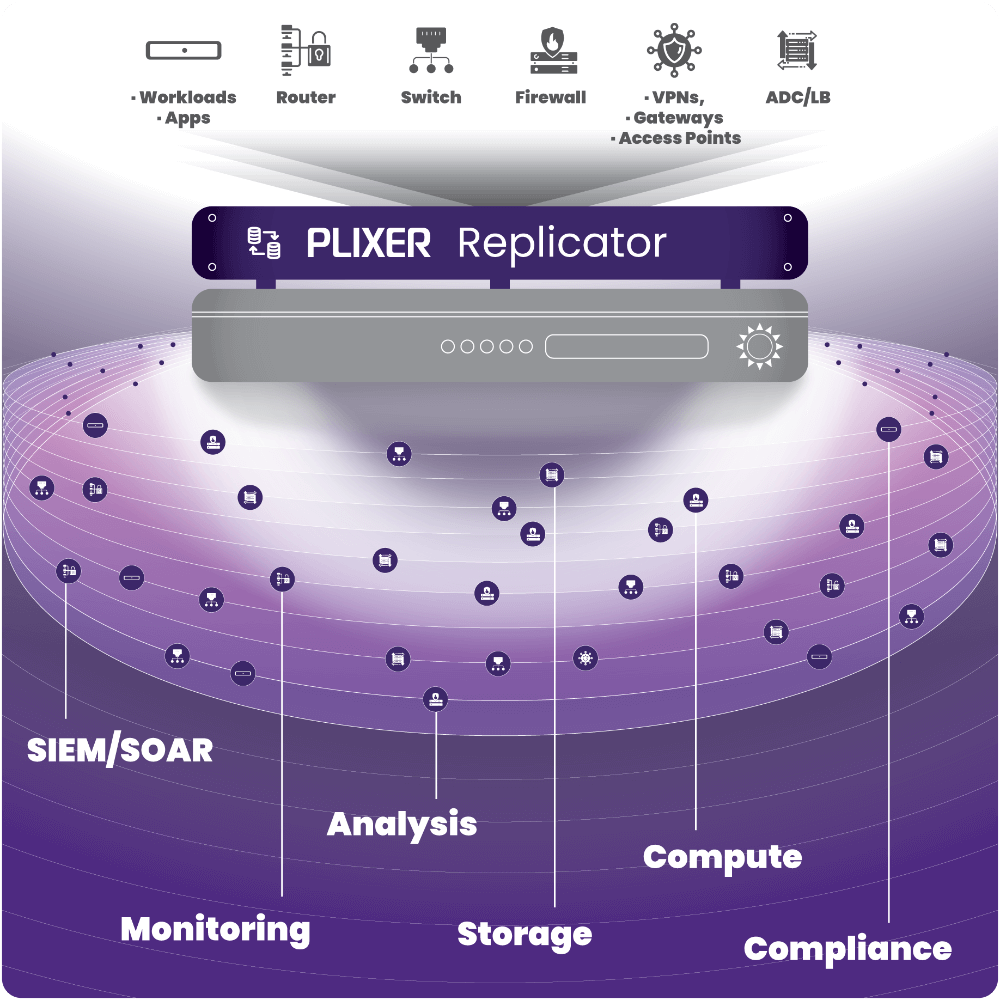
Seamlessly Replicate Data with ease
- A single distribution point for all exporting devices
- Replicate Syslog and UDP data without shaping, filtering, or storing the data.
- Automatically enable NetFlow/IPFIX data transfer for monitoring, analysis, and risk mitigation
Plixer Replicator delivers a better approach to Replication
Initiates data transfers to destinations that are verified operational and acts as proxy load balancer to handle replication of packets through routes optimized for efficiency.
Listens for exporter signals of NetFlow/IPFIX/Other UDP packet data and replicates it to any number destinations
Efficiently sends data copies to and from multiple recipients simultaneously, using a specific ports and IP address ranges or groups, rather than sending separate copies to each receiver
Automatically assigns exporters to collectors based on their capacities and current workloads.
Available when implemented with Plixer One
Continuous, uninterrupted service for single network and multi-network environments
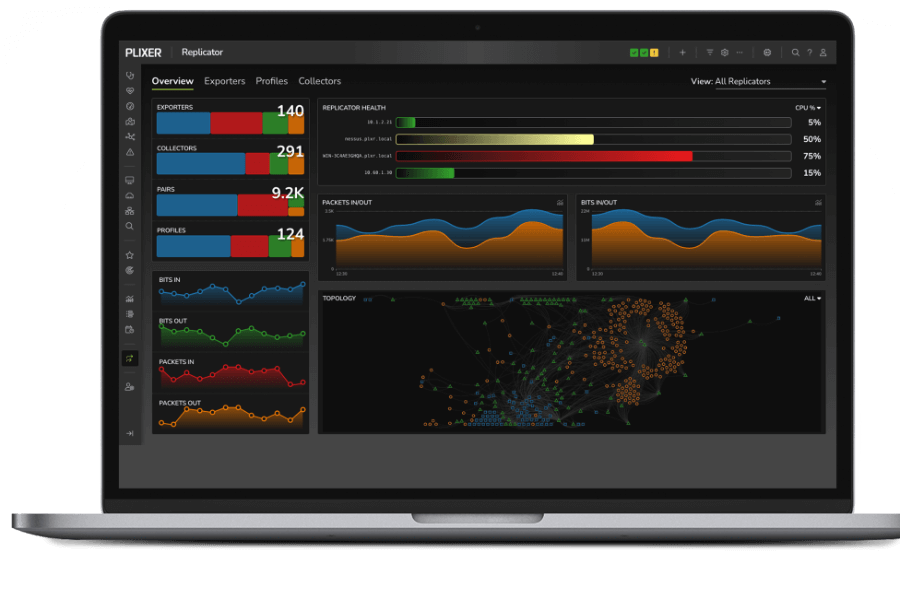

Experience the value of Plixer Replicator
- Activates quickly and replicates data immediately
- Gathers host data without host-based software or agents
- Easily mix & match source and targets
- Manages hundreds of jobs simultaneously
- Integrate collecting devices in seconds
- Eliminates timely repetitive human efforts
PLIXER REPLICATOR
Designed to Deploy
Quickly deploy to:
01
Distributed
Datacenters
02
(OT) Industrial
Environments
03
Campus/Branch
Offices
Hardware appliance 1u Rack Mountable
- Chassis configuration: 1U Chassis
- Processor: Intel® Xeon® Gold 5315Y 3.2G, 8C/16T
- Memory: 2x 16GB RDIMM, 3200MT/s
- Storage: 2x 480GB SSD (RAID 1)
Virtual Appliance – ESX, Hyper-V or KVM
- Processor: 2 CPU, 2 cores, 2 GHz+
- Memory: 4 GB RAM
- Storage: 100 GB
- OS: ESX/ESXi5+


