Are you aware of any data tunneling that might be occurring in your network? Do you think that your network is totally secure? If your company network connects to the internet, there is a very good chance that your business is not safe from all forms of malware.
The problem with most security solutions is that they typically need to know what they are looking for. Administrators configure firewalls and routers with access rules based on what they want to allow or block. Intrusion detection systems use signatures, and even next-gen firewalls that use deep packet inspection (DPI) need to understand some kind of rule set that determines allowed or disallowed packets. Acceptable user use policies? They are only as good as the user adhering to the rules.

There is a flood of security solutions in the IT market these days. They all claim to secure corporate and personal sensitive assets. Yet we continue to see news reports on a regular basis about companies being hacked and data stolen.
The bad actors appear to be ahead of the security solution curve. They have methods of infiltrating networks that are unknown from a signature standpoint. They use protocols and applications that disguise what they are doing and appear to be perfectly normal traffic streams.
The bottom line is: you can’t stop what you don’t know, or can you?
You can be more pro-active in recognizing and investigating suspicious behavior. Hackers these days are very good at using common ports and protocols, especially ones that generally need to be open. Over the past few years, we have seen many cases where data is exfilterated from a corporate asset by use of data tunnels. A tunnel is a mechanism used to ship a foreign protocol across a network that normally would not support it. Tunneling protocols allow you to use IP to send another protocol in the “data” portion of the IP datagram. Most tunneling protocols have an agent on the client and server side that encapsulates TCP or UDP data into an allowed, commonly used protocol. We have published many blogs in the past year that talk about the use of DNS tunneling and ways to detect application tunneling.
Just like in the case of DNS tunneling, where DNS is usually open, ICMP is generally not globally blocked either. There are legitimate reasons that a user or administrator might need to use ICMP in a network environment to check internal or external address availability, or routes. Much like the applications available to do DNS tunneling, there are many programs available to pass data from one point to another via ICMP tunneling.
The client loads ICMP packets with file/data content and passes ICMP request packets to a destination. The destination has a listener program that reads and unpacks the ICMP packets. Another method might be to have a packet capture like TCPDUMP listening for ICMP packets from the initiating client IP address.
It is actually very simple. So what can we do to be aware of this ICMP tunneling behavior?
The problem with DPI is that you don’t always know what to look for. But using NetFlow/IPFIX, flows are collected that represent all of the conversations traversing the network. This way, you gain visibility into suspicious conversations coming in and out of your network as well as moving laterally inside, without needing to see packet content. Suspicious tunneling patterns are recognized and alerted on immediately without you having to globally block the ICMP protocol.
So what are we looking for?
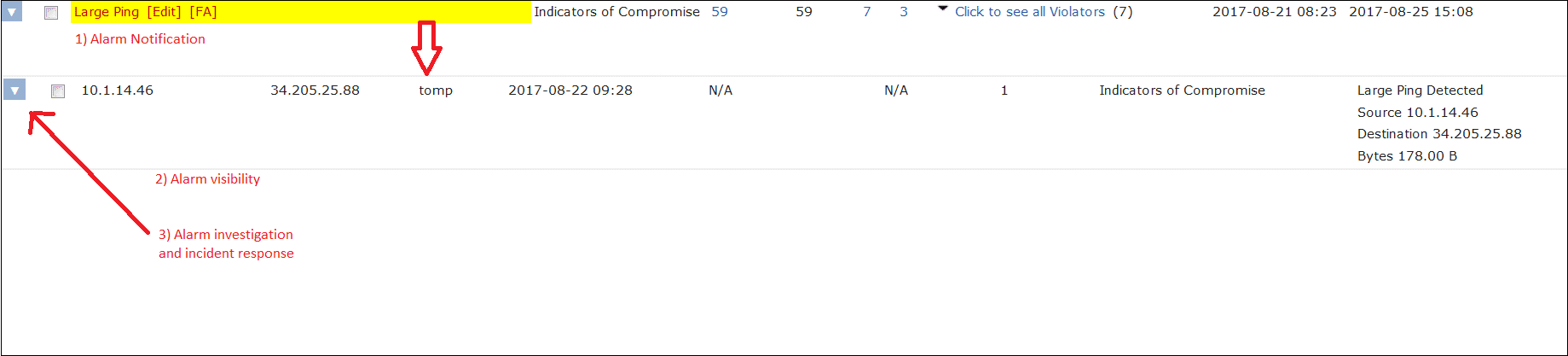
In most instances, ICMP generates a fixed number of bytes in a packet. The size may change based on the host operating system, but remains a very predictable value. So if we can alarm on cases where the total byte count compared to the packet counts result in a larger-than-normal number, we can detect that threshold breach without knowing anything about content.
The algorithm checks for suspicious ICMP traffic patterns and triggers an alarm. These traffic patterns can then be easily analyzed.
Network traffic intelligence using NetFlow or IPFIX can recognize enough odd behaviors to protect against cyber-attacks. Collecting flows from all of the firewalls, routers, and switches on your network essentially turns each device into a security probe and provides a great additional security layer to your network intrusion prevention solution.
The bottom line is that your company can be and will be hacked. When will it happen? What will they do? How will you investigate the event?
Do you have insight into the traffic moving across your network? Contact our support team if you want to learn more or need help with alarm configurations.