I want to introduce you to a very cool, very powerful search function for investigating IP Addresses.
We talk all the time about how NetFlow and IPFIX technologies fit very well in the behavior analysis side of a layered security solution.
NetFlow is a feature that provides the ability to collect IP network traffic as it enters or exits an interface. By analyzing the data provided by NetFlow, a network administrator can determine things such as the source and destination of traffic, class of service, and causes of congestion (if any).

In today’s networks, using NetFlow for network traffic intelligence by monitoring communication behaviors is becoming more prevalent.
NetFlow records represent all of the conversations traversing the network from any observation point on the network. From a security perspective, you gain visibility into suspicious conversations coming in and out of your network as well as moving laterally inside.
Understanding top talker information or bandwidth trends is not really what the security administrator is looking for when it comes to traffic analysis solutions. Instead, their challenges revolve around the search for the needle in the haystack.
Once NetFlow is collected, administrators have a powerful way to filter on particular network traffic.
Time to Talk about the Host Index Function
The Host Index search offers a very easy jump-in filter to see what a particular IP address is doing, or if the IP address in question has ever been on the network at all.
In a recent article, John Cloonan talks about how the delay in identifying new forms of malware via signatures makes corporations vulnerable to serious damages. We have been preaching this as a reason to use NetFlow for security for years.
Host Index search offers the ability to see whether an IP address has ever existed on the network. This is powerful because you don’t have to rely on malware signatures to catch threats.
Let me walk you through one of these scenarios:
Your intrusion prevention system blocks a traffic stream that happened late last night. It points out that IP address 87.255.51.229 is the source address sending the data.
So you know that there was a particular data signature, and you know the source IP address of the traffic stream.
But what you do not know is: has this address ever been seen on the network before? And who talked to it?
Let us do the search:
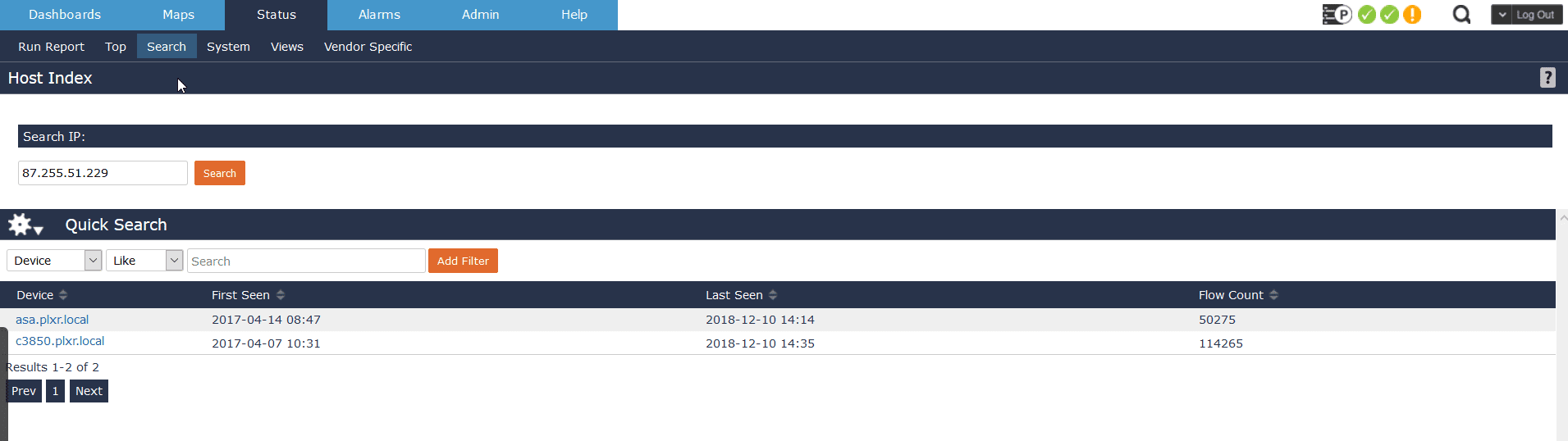
Host Index search scales very well and does not depend on stored historical data. It will –quickly determine whether this IP address ever been on the network.
It will also tell you what device or devices the IP address sent traffic through, the first and last times it was seen, and the flow count.
If there is historical data available, you can easily pivot into the reporting/filtering engine to determine who and what was going on.
Collecting flows and using the Host Index function provides an efficient means to identify inappropriate behavior, problems, and discrepancies. In addition, the ability to drill down to particular traffic specifics makes security forensics and incident response using flows an invaluable tool for charting the health of your network.
If you need to know whether an IP address has ever been on your network, configure NetFlow and download Scrutinizer, and become network aware.