Ping is one of those protocols that no one thinks about until it isn’t working and you’re trying to quickly troubleshoot connectivity between devices. Officially known as ICMP, ping is one of the older RFCs and is most used for its echo requests and replies for troubleshooting networks. Some administrators simply block all ICMP everywhere on their network. Is this for everyone? Is this necessary? With everyone’s network having its own constraints and security policies, hopefully this post can provide some insight into the thought process behind monitoring for ping.
Ping of Death
The “Ping of Death” was once a scary reality that networks needed to deal with. Due to either a misconfiguration or a bad actor, ICMP packets crafted to be larger than 65,535 bytes have the potential to overflow devices when they attempt to process the packet. Devices that simply follow the IP protocol guidelines could be vulnerable to memory crashes upon reassembly of these large packets . This isn’t really a problem anymore since devices can mitigate or filter ping size before processing these fragmented packets. Unless you are running very old or vulnerable devices on your network, the “Ping of Death” should be low on your scale of worries.
Flow analytics algorithms for ping
Plixer Scrutinizer provides many ways to monitor ICMP traffic, including five different flow analytics algorithms:
- ICMP Destination Unreachable
- ICMP Port Unreachable
- Ping Flood
- Ping Scan
- Large Ping
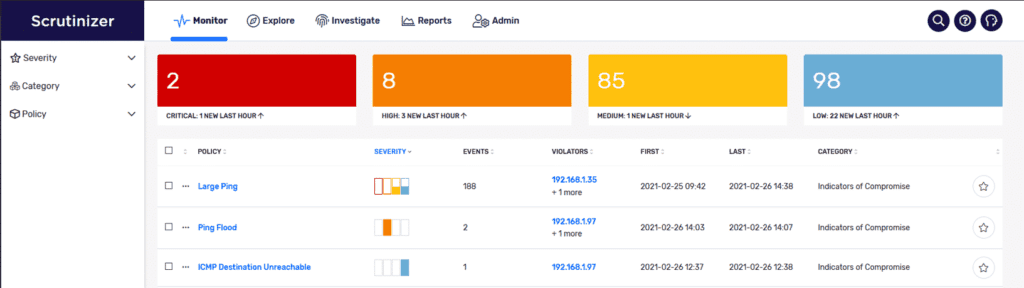
These algorithms can help detect suspicious behavior on your network or misconfigurations surrounding the ICMP protocol. ICMP Destination Unreachable and ICMP Port Unreachable both can help identify network issues within your network or attempts to reach services that may be down or non-existent.
The Large Ping algorithm can identify those “Ping of Death” attacks but can also identify a bad actor learning about your network. Sending larger-than-normal pings can help someone learn the MTU size or capabilities of a specific network path.
Ping Scan can help identify potentially infected systems or devices that are misconfigured and going over a specified threshold of pinging unique devices.
Ping flooding is a symmetrical ICMP attack where the attacker performs echo requests to a target in an effort to overwhelm the device. This attack is symmetrical in nature and usually requires the attacker to have more bandwidth than the targeted device. The flow analytics algorithm can be tuned to alert on devices prior to this event occurring with enough bandwidth to overwhelm the targeted device and allow a network engineer or administrator to mitigate the attack.
Other ICMP attacks
There are many other ways to abuse the ICMP protocol in an environment; two of the more interesting ones are data exfiltration and firewall filter evasion. It is possible to tunnel traffic through ICMP, which can be a potential vector for data exfiltration. Depending on the methods a bad actor can use, this might be difficult to detect. Bad actors sending out pings over time that encapsulate confidential data could be hidden for a long time. One way to alert on this behavior would be to tune the Large Ping flow analytics algorithm to the minimal byte size for successful echo requests. You could also run reports from Plixer Scrutinizer to determine total unique flow pairings and their associated bandwidth usage. If there is steady pinging between devices, then those conversations might need to be investigated further. Other mitigation practices such as blocking ICMP on either side of your firewalls or edge devices could help, but at the cost of limiting troubleshooting or other network functions involving ICMP.
Trace route is one of the commonly used tools to figure out the routing paths of your network for troubleshooting, but this also reveals your network topology to potential bad actors.
OS fingerprinting can be achieved using ICMP as well. The TTL response can indicate whether the replying device is a Windows host or a Linux host. By default, Windows devices reply with a TTL of 128, while Linux hosts reply with a TTL of 64. There are other fingerprinting techniques that can also be used to gather even more information about devices based on their ICMP, but that’s a post for another day.
ICMP Router Discovery Protocol provides a way to discover neighboring routers within a network via ICMP. This can indicate to bad actors the presence of alternative gateways outside of their routing path. Some routers are configured to periodically announce their presence via multicast. These messages can even be spoofed to potentially alter the routes of other devices on the network. Plixer Scrutinizer can help identify these conversations on your network by running reports on ICMP traffic filtered for multicast addresses.
Conclusion
What does this all mean? Should you be monitoring ping in your environment? Ultimately, it is a good idea to have knowledge of the ICMP traffic in your environment as it can lead to some insight into the health and security of your network. If you are interested in gaining visibility into the ping activity on your network, Scrutinizer is a useful tool.