As enterprises adjust to the new normal and remote work, they are bracing for potential attacks resulting from employee carelessness. Bad habits, such as leaving devices unattended while on the VPN, can pose serious risks to the business. This blog will discuss how human negligence affects network security and provide some examples of how some threat vectors impacts organizations.
Key negligent mistakes employees make when handling data
According to an article from Nevada IT Solutions, human negligence is the main cause of data breaches. One common example is employees with local administrator rights who disable security solutions on their computers and let the infection spread from their computer onto the entire corporate network. Lack of security training combined with working remotely in an unsecured environment leads to negligent mistakes. Let’s take a look at some key mistakes below:
- Employees responding to phishing emails with malicious scripts attached
- Use of company VPN while accessing 3rd-party cloud applications such as Dropbox and Google Cloud
- Sharing sensitive data with colleagues using unsecured messengers
- Using unsecured email attachments when sending sensitive data
- Using outdated software, thus exposing the company to unpatched vulnerabilities
Let’s investigate how Plixer Scrutinizer can detect threat actors
Much of human negligence is caused by insiders who are the most trusted and highly skilled. Business News Daily shares examples of network administrators who perform inappropriate behavior such as engaging on file-sharing sites or sending documents to personal emails or using USB sticks. Other security vulnerabilities include unknown malware or security bugs on computers, or accessing untrusted sites. With machine learning and artificial intelligence, Plixer Scrutinizer can detect these threat actors. Let’s take a denial-of-service attack and dive deeper into how Scrutinizer can detect file-sharing attacks on a company’s environment.
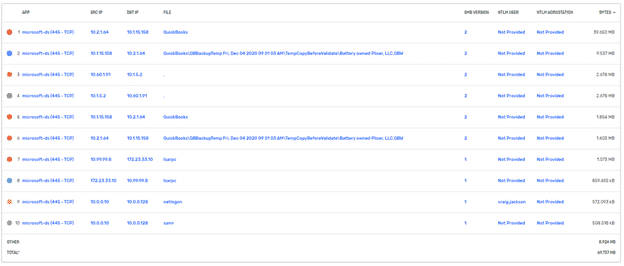
For this particular use, Scrutinizer can identify and detect vulnerabilities such as server message block (SMB) associated with a specific source and destination IP address. Scrutinizer’s fast reporting and scalability are key game changers in detecting the deviations of SMB traffic behavior within the company’s network.
Since the COVID-19 pandemic began, hacking attacks of remote employees has skyrocketed, according to Insurance Journal. Let’s look at another example of human negligence: a remote employee leaves his/her corporate laptop and an internal employee hacks his employee’s Wi-Fi router, performs a port scan onto the home wireless network, and is able to transfer and retrieve the employee’s account data from the computer. This is an example of data exfiltration.
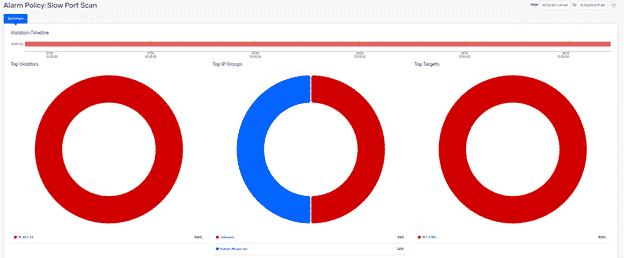
The image below shows the target device and violator performing the port scan:

Another example of human negligence affecting network security is employees with local administrator rights who disabled security solutions on their computers and let the infection spread from their computer onto the entire corporate network could potentially expose the organization to WannaCry activity.
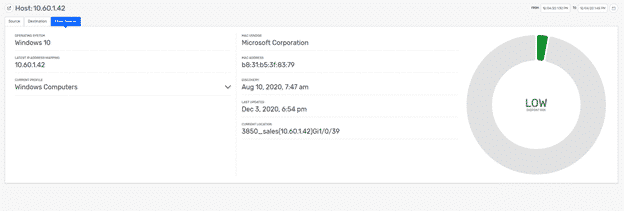
Scrutinizer will detect network traffic visibility, but the use of Plixer Beacon integration enables endpoint visibility. This allows a SOC analyst to detect the threat actor’s location, operating system, current IP address, device type, and MAC address within the company’s network. This endpoint information is important when performing threat hunting because it pinpoints the risk to the organization and enables SOC analysts to proactively respond to incidents.
Conclusion
As employees are forced to work remotely, VPN services are not scalable for organizations moving their entire workforces remotely and they lack network visibility. This opens the door for hackers to breach an organization’s network and critical resources; Plixer Scrutinizer and Plixer Beacon provide a solution to monitor human negligent activity. Plixer provides a product suite to help organizations detect malicious activity. The most reliable way to ensure accurate detection and prevention of security mistakes is by using employee monitoring software like Plixer Scrutinizer and Beacon.



