According to a recent Ponemon Institute report, the cost of insider-related breaches has escalated to over $8.7 million. What’s even more concerning is that as the cost of insider threats has increased, the cost of non-insider threats is $3.6 million, according to IBM. This means that insider incidents cost more than double that of non-insider incidents. Furthermore, the report also indicates that insider threats take more than two months to contain on average. With this in mind, I’d like to help you understand these insider threats, and how to mitigate insider threats with network traffic analytics.
 To begin, let’s define what an insider threat is. An insider threat is “a malicious threat to an organization that comes from people within the organization, such as employees, former employees, contractors or business associates, who have inside information concerning the organization’s security practices, data and computer systems.” Essentially, an insider threat is a threat from someone who you’ve provided access to or knowledge of your network.
To begin, let’s define what an insider threat is. An insider threat is “a malicious threat to an organization that comes from people within the organization, such as employees, former employees, contractors or business associates, who have inside information concerning the organization’s security practices, data and computer systems.” Essentially, an insider threat is a threat from someone who you’ve provided access to or knowledge of your network.
Respondents of the Ponemon research indicated that 64% of incidents were from negligent employees, while 23% were from malicious insiders. So if 64% of the incidents are from negligent employees, we can safely say that stolen credentials are a primary way for malicious actors to take over servers and computers on a network.
Thanks to phishing attacks, credentials are constantly stolen and are being saved en masse by hackers. Hackers will use the credentials to gain a foothold, and ultimately try to steal data.
How to Mitigate Insider Threats with Network Traffic Analytics
With network traffic analytics, you can monitor and baseline normal credential use and alert on deviations. So, for example, when you see a user’s credentials being used to attempt to connect to a device that they don’t normally connect to, you can be alerted to the potential credential misuse. Or, if you see login attempts to multiple devices, or you see many logins being attempted on a single server at one time, you can quickly block the attack from continuing and find the device that has been infected.
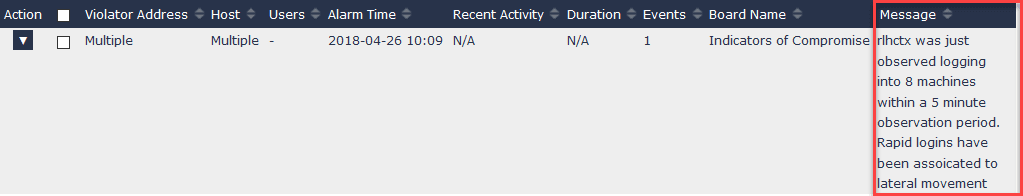
Furthermore, with network traffic analytics you can pivot from the user credentials to other network traffic data to reveal a complete picture of what a malicious actor was granted access. This allows you to understand what data may have been stolen, and from which devices. It also allows you to verify that the policies you’ve put in place are actually working. After all, you’ve put a lot of effort into protecting your network. You don’t want a rogue employee accessing financial databases that shouldn’t have access.
Overall, by baselining credential use, you can easily mitigate insider threats because you have the data context you need from network traffic analytics. If you’d like to mitigate insider threats with network traffic analytics, download a 14-day trial of Scrutinizer and start baselining your user’s network traffic patterns today.