Ryuk ransomware was discovered in August of 2018. Since then, over 100 US organizations have been affected. Knowing more about how Ryuk ransomware operates can help us to better protect our network.
What is ransomware?
In the Oxford dictionary, ransomware is defined as a “type of malicious software designed to block access to a computer system until a sum of money is paid.” Usually, this is done by encrypting files and offering a decryption key for the payment of a sum of money in the form of a cryptocurrency.
How does Ryuk ransomware infect my network?
Ryuk enters the network in common ransomware fashion by using phishing emails with malicious macro-enabled attachments. Opening the attachment allows for the malicious code to run the command line and from there, PowerShell.

When the malicious code has access to PowerShell, it will download Emotet. If you are unfamiliar with Emotet, it is a type of malware that’s usually spread through spam emails. It can be used to steal credentials and retrieve payloads. Here, Emotet is used to retrieve TrickBot. TrickBot can be used with various modules for specific tasks. In the case of Ryuk, TrickBot is used to steal the credentials of infected machines.
Bad actors will then use the credentials stolen by TrickBot and the RDP (remote desktop protocol) to move through the network. Once a session is established, they will execute Ryuk. Ryuk then begins the process of encrypting every file on the infected machines. Encrypted files will have the extension .ryk added to the file name.
Ransom notes are left in the folders containing the encrypted files. The ransom note will be titled RyukReadMe with the extension .html or .txt. Within the ransom note, there is a set of instructions and email addresses the victim can use to contact those operating the Ryuk ransomware. After the victim contacts the operator through email, a Bitcoin wallet address is supplied to the victim for payment.
How do I protect my network?
The first step is always to teach the people within your network what phishing is, what it looks like, and how it works. Next is using the tools on your network and starting with what you know.
The major hint here is that Ryuk uses RDP to move laterally through the network. Knowing this, we can use Scrutinizer’s network forensics by pulling a “Source > Host Flows” report in Scrutinizer. I would then add a “Well Known Port” filter for the RDP port 3389.
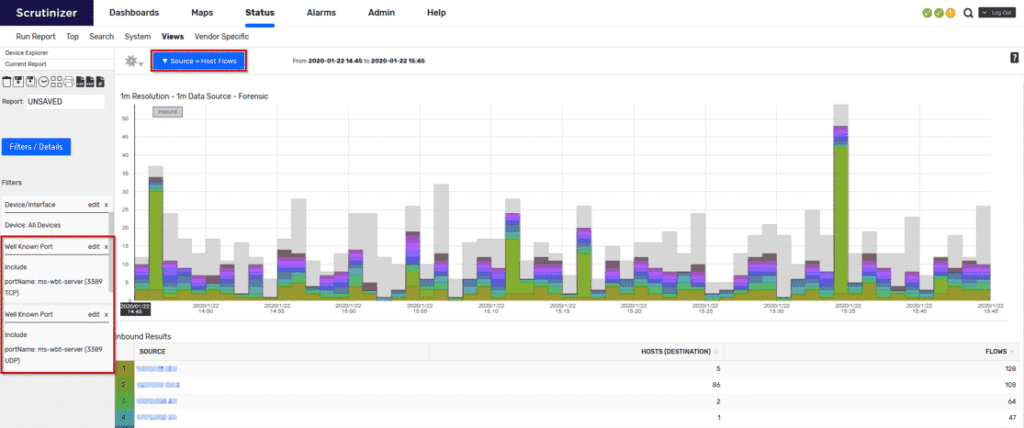
Here we’ll get a list of users as our “Source” along with a count for the different hosts they’ve communicated with. Knowing your network is key here. You can create IP groups within Scrutinizer to filter on different user groups and alert on the number of different hosts they’ve communicated with. If we see this count spike for users who do not normally have RDP sessions, we can be alerted that an attack like Ryuk may be in effect and we can take early action against it. Try out Scrutinizer to view anomalies on your network and be prepare for attacks like Ryuk and WannaCry.





