When shopping for tools to help with network forensics, you will find many vendors claiming why they are the best, but not necessarily how they fit into your existing security ecosystem. Here, I’ll cover how our customers use our IPFIX and metadata solutions as part of a layered security approach that uses all facets of the existing network infrastructure.
Ransomware and User Behavior Analysis
Some of the biggest news in recent years covered how companies’ data has been held at ransom until they either restore from backups (usually with a lot of downtime) or pay off the ransom (usually with a lot of money). Even worse, there is no guarantee that this will not happen again—looking at recent breaches, it is actually more likely to. All it takes is a security or network forensics team missing a single infected host for it spread through the network again.
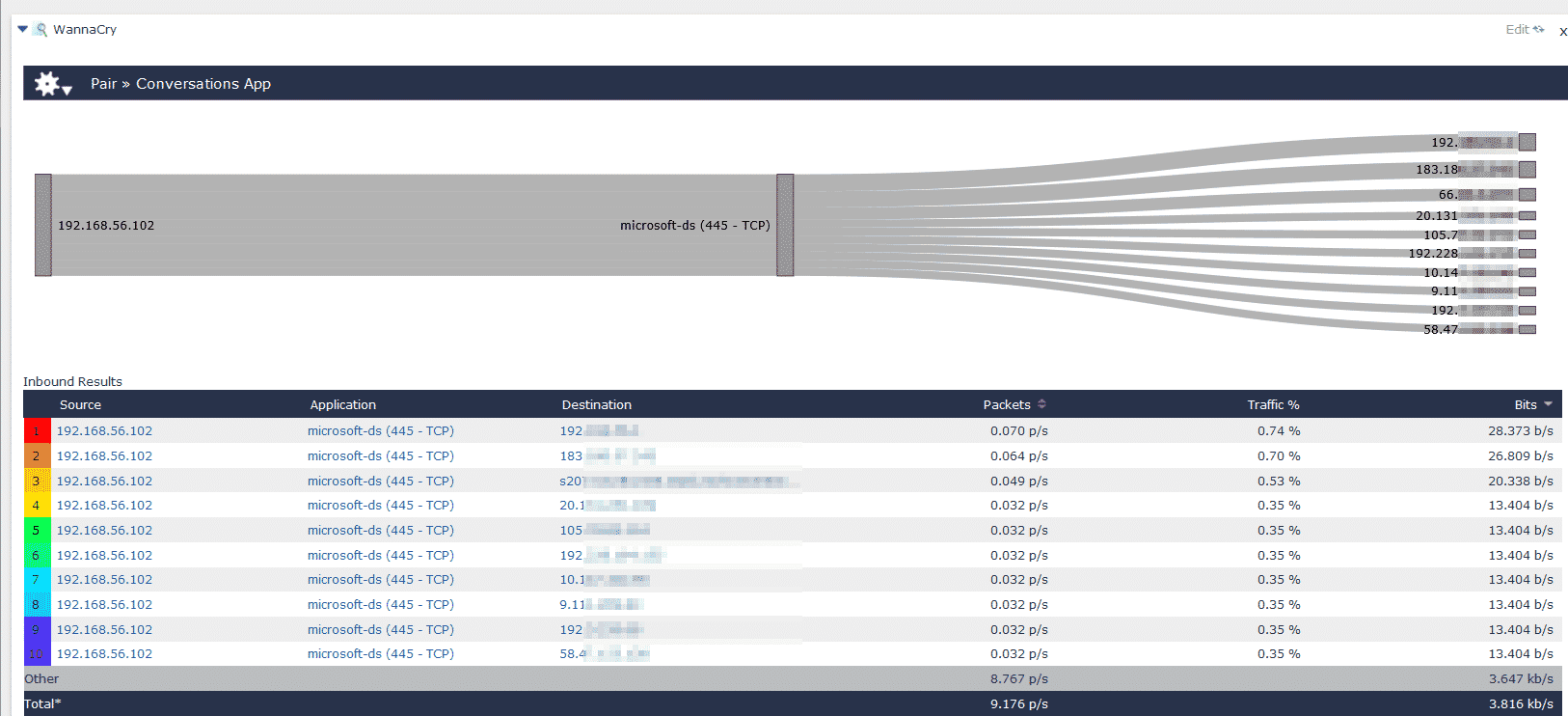
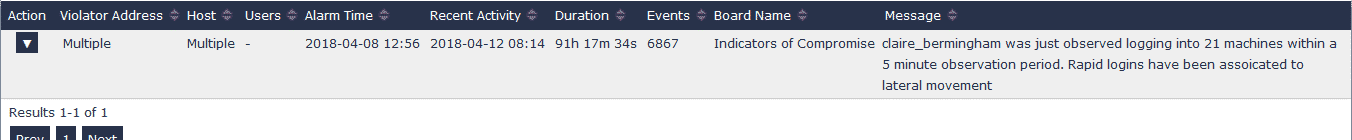
By running a series of behavioral analysis (machine learning) algorithms against the NetFlow/IPFIX data, we can set an alarm to go off when we see any suspicious traffic or lateral movements. Using this together with metadata, we can analyze information from Active Directory, Cisco ISE, CounterACT, and other NAC solutions. Then we can tie any of the events we have found back to a particular user/asset on the network and even show what else they’ve touched, making clean-up easier and more effective.
As you can see from this image, an infected host moving laterally on the network will trigger an actionable alarm. From there, you can pivot to your company’s SIEM or packet analysis solution.
Cloud Monitoring and Microsegmentation
With more and more companies establishing a cloud–first initiative, more traffic is starting to be sent into a cloud that you don’t manage. Security teams are left in the dark since they are often times not the team managing these resources
Integrating AWS VPC (Virtual Private Cloud) Flow Logs with our solution and deploying our collector into your VPC gives you the insight your team has been looking for. By combining this with a combination of on-premise and cloud packet brokers, you’ll have full visibility into the environment you previously had no control over.
Even if your company has decided to hold off on moving critical resources to the cloud, you will still have a robust virtual infrastructure. Collecting from VMWare distributed switches as well as NSX can provide visibility into VXLAN traffic (pre/post encapsulation), letting you see exactly how VMs are communicating on the network. Now you have the information needed to make sure the hosts you expect are only accessing these resources. If hosts are talking to it, you have alarms to tell you who, what, when, and where.
Data Exfiltration and a Layered Approach
We find that customers already have solutions that are integral to their NetOps/SecOps workflows. This is where our robust API and agile web interface come in. Since teams already have experts on packet capture, SIEMs, IPAM, and DLP software, we use our API to connect our solution’s interface with their existing workflows. This enhances the data you were already receiving without having to completely retrain the team.
This is especially important when it comes to tracking data exfiltration and data breaches. The longer you wait, the more difficult it is for the network forensics team to track. We can provide insight into which countries, operating systems, URLs, and DNS requests are on the network. Tying this with any long-lived flows makes it much easier to kill the connections as soon as this behavior is spotted. If you are of the mindset that breaches are inevitable, then clean-up is just as important. You can use historical and granular data along with any packet capture/event logs you have collected to track any suspicious connections.
Revamping your Network Security
If you and your team have questions on where we can fit in your environment, please feel free to reach out to our team! If you want more information on any of the metadata analysis I’ve spoken about take a look at our FlowPro IPFIX Probe.



