Over the last few days, there has been a whirlwind of global activity surrounding the WannaCry ransomware attack. I wanted to share a short list of facts surrounding the attack and the way that Scrutinizer has been used by both Plixer and our customers to gain visibility, run reports based on historical data, and reduce risk.
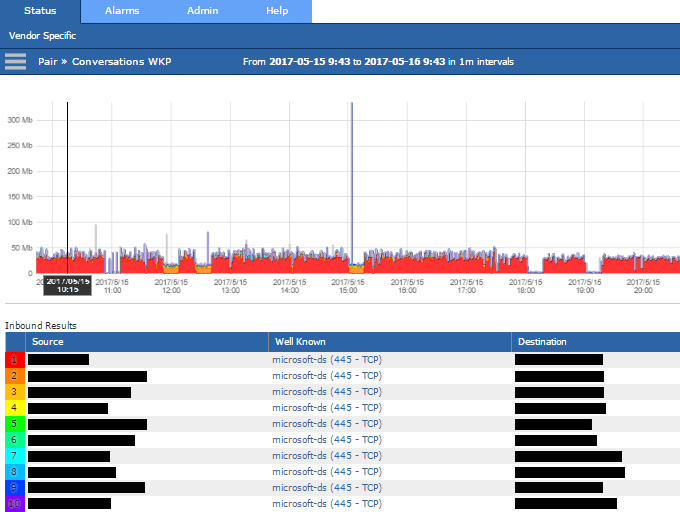
With Scrutinizer you can understand what file sharing traffic is valid on your network, as well as the servers and users associated with that traffic. It also provides the data needed to quickly create policy rules and access control lists (ACLs) for switches, routers, and firewalls to ensure that newly infected devices are not able to spread via peer-to-peer TCP port 445 communication.
Quick Fact Set:
- A hacker group named Shadow Brokers stole and leaked some previously secret tools developed by the NSA.
- One of these stolen and leaked tools was an exploit of Microsoft’s file sharing program SMB v1, which uses TCP port 445.
- Microsoft released a patch for the vulnerability (MS17-010) in March.
- On Friday, May 12th, the WannaCry ransomware crypto virus appears to have begun to spread across Europe. WannaCry gains access via the MS17-010 vulnerability and encrypts files for ransom.
- The worm uses TCP port 445 to attempt to propagate locally, as well as across the Internet.
What You Can Do:
- Use Scrutinizer to run long-term historical reports identifying traffic patterns and the legitimate servers that normally send and receive network traffic using TCP port 445.
- This provides a baseline of allowed port 445 traffic.
- Armed with this data, you can quickly create ACLs on routers/switches to lock down P2P use of 445, and limit it to valid traffic without disrupting business ops.
- Generate a report identifying the list of IP addresses (servers) allowed to use port 445.
- Set an alert for any 445 traffic originating from any disallowed devices on the networks.
- Gather and monitor historical DNS traffic historically (check DNS logs) looking for devices that have reached out to the kill switch domain.
- Set alarms to alert if any new devices reach out to the kill switch domain.
- Immediately quarantine any devices that begin sending 445 traffic that isn’t allowed via ACLs and/or reach out to the kill switch domain.
Breaches Are Inevitable:
WannaCry ransomware is the latest proof that complete prevention of breaches is impossible. Sophisticated attack vectors will find their way in, and breaches are inevitable. What organizations need is access to rich forensic data to support fast and accurate incident response. Organizations must begin to create clear data backup and recovery strategies for both servers and end systems. The volume and variety of ransomware attacks will continue to grow rapidly. Bad actors are incentivized by monetary gain. Organizations that can quickly identify breaches and offending end stations, quarantine them, wipe the machine, and recover the data are best positioned to weather the storm.
If you already own Scrutinizer and have any questions about the above information, see our support page.
If you are not a current customer of Plixer, but would like someone to contact you, click here.
If you would like to see how Scrutinizer can deliver insight into your own environment, you can download a free version here.





