
Using your network as a sensor
I spent a lot of time talking to customers at RSA 2019 and a message that resonated with a lot of them was using...

I spent a lot of time talking to customers at RSA 2019 and a message that resonated with a lot of them was using...

Things move fast in cybersecurity, and it’s always worth investing time to stay up-to-date on the state of the field. I’ve gathered 15 articles...

In my last post, titled Network Visibility: Using Dashboards to Tell a Deeper Story, we discussed how the dashboard feature of Scrutinizer can be...

Enterprises are seeking a secure monitoring solution that performs encapsulation. Encapsulated Remote SPAN (ERSPAN) identifies visibility gaps and vulnerabilities, but using it enables flow...
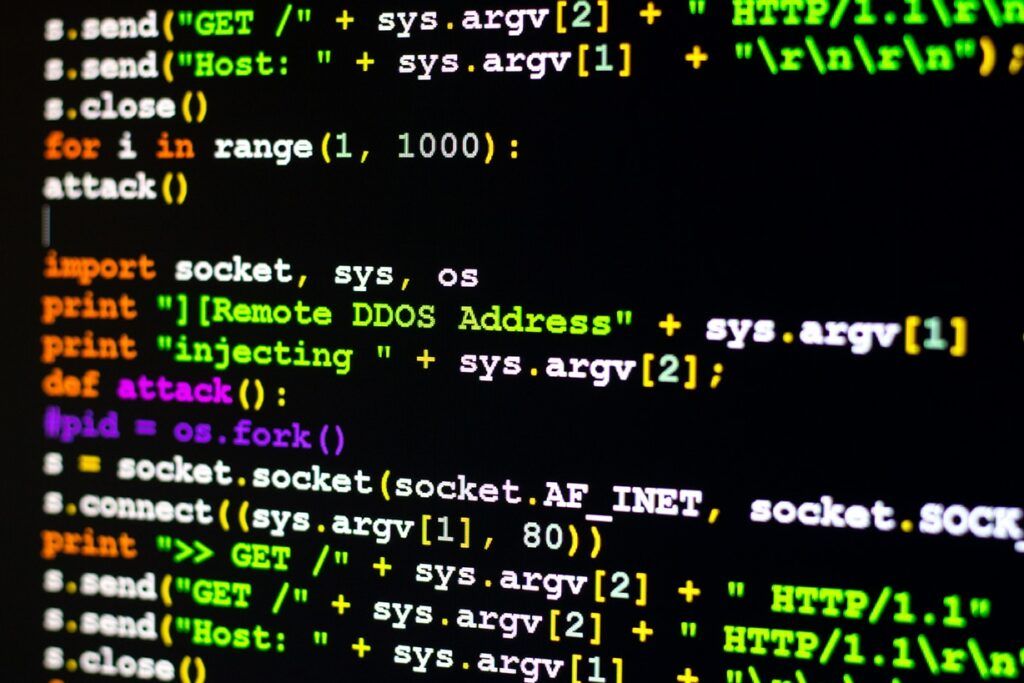
DDoS attacks have plagued the network security space for almost 20 years. In that time, we have seen a lot of changes. In just...

If you are ever out to dinner with friends talking about which network devices have the strangest exports, the Cisco ASA will certainly be...

After you celebrate New Year’s Eve, it is time to get to work on those New Year’s resolutions! It is also a good time...

I want to introduce you to a very cool, very powerful search function for investigating IP Addresses. We talk all the time about how...

It’s that time of year again. Employees have gone away from the office to spend time with friends and family. They will, of course,...

NetFlow can give us all kinds of rich information about our network infrastructure. You’ll find standard fields with information like source and destination and...
Looking for documentation? Visit our documentation site