DDoS attacks have plagued the network security space for almost 20 years. In that time, we have seen a lot of changes. In just 2018 alone, we saw the first multi-terabyte/s DDoS attacks, which have been bringing large organizations to their knees. If you aren’t prepared to quickly and effectively analyze DDoS attacks in real time, are you even prepared at all?
Monitoring DDoS in Real Time
Dictionary.com defines a DDoS attack as “being an incident in which a network of computers floods an online resource with high levels of unwanted traffic so that it is inaccessible to legitimate service requests.” I think this is a pretty accurate definition. These floods of data can be done a variety of ways, but recently botnets-for-hire seem to be the most common way. This allows anyone with some cryptocurrency and a laptop to issue very large DDoS attacks against anyone they please.
Let’s take the GitHub DDoS attack of 2018 as an example. This was a 1.3TB/s attack against the cloud-based code hosting platform and set a new record for the largest attack seen in the wild. The previous record had been a 602GB/s DDoS attack against the BBC just two years prior. While most DDoS attacks are still against financial services, we have also seen an uptick in attacks against the IT services and media & entertainment spaces.
Setting up Real-Time DDoS Detection
Included in Scrutinizer’s suite of behavioral algorithms are two newly revamped DDoS and DrDoS (Reflective DDoS) algorithms. These algorithms come enabled by default, but need some simple configuration before alarms will trigger.
- Once flows have been exported into Scrutinizer, navigate to Admin -> Settings -> Flow Analytics Configuration
- From this page, click into DDoS Detection or DRDoS Detection
3. Next, navigate to the Exporters tab and add in any internet-facing exporters you want to monitor. Once the devices are added, the algorithms will start running automatically.
4. If you haven’t already, we also recommend that you create an IP Group for your external protected address space. This can be done under Admin -> Definitions -> IP Groups.
I typically recommend enabling the algorithms with our default settings to see what alarms pop up. If you find some false positives, we can easily adjust the algorithms to finely tune them.
Real-Time DDoS Analysis
When a DDoS attack is happening against your organization, it is important to appropriately escalate the attack to get the right people involved. Since our DDoS algorithms can be configured to send alarms formatted as email, syslog and SNMP traps, you should already have a notification with the event details.
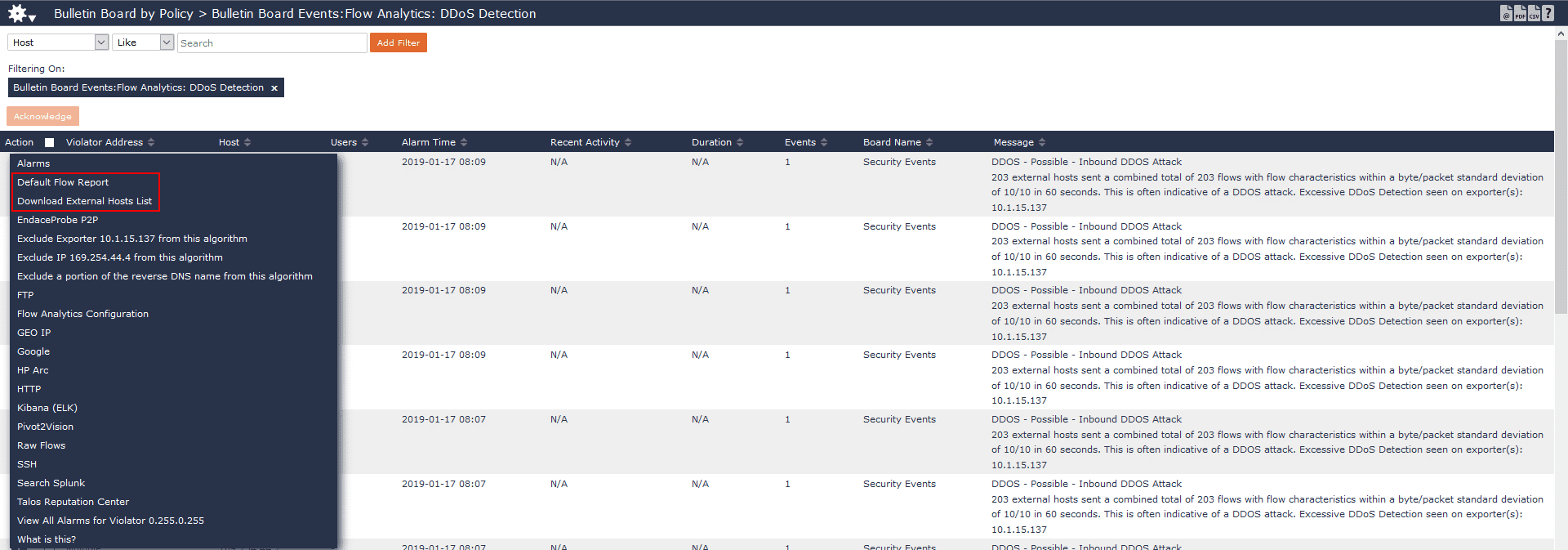
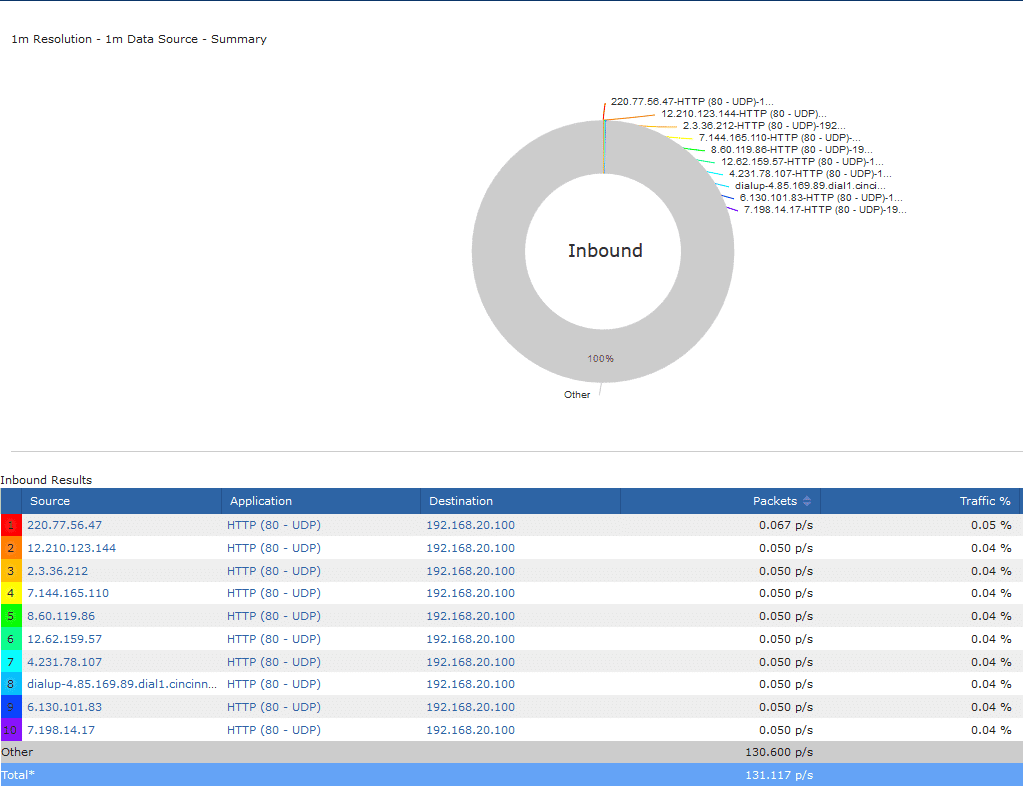
You can also log in to Scrutinizer and navigate to the Alarms tab, which will have more information about the event. Some details you can easily grab are destination of the attack, ports and protocols used, how many hosts are involved, and what exporter we saw this on. If needed, you can also export the list of attackers to a CSV to be used in black holing the traffic.
Future of DDoS Detection and Analysis
If past trends are any indication, 2019 will be a busy year for DDoS defense. An alarm suite that can notify you within seconds of an attack happening will be great tool to have in your arsenal. If DDoS attacks keep you up at night and you want to see how Scrutinizer can help please take a look at our download page here.