The Zero Trust model is a relatively new network security design model that requires network segmentation and segregation of employees from critical internal resources. The basic idea is that the internal network is no longer explicitly “trusted.” BYOD policies and the mobile workforce have brought new threats to the internal network that just weren’t there five years ago. It’s no longer practical to assume “bad guys outside, good guys inside.” Let’s take a look at exactly what this means…
The Zero Trust model is a relatively new network security design model that requires network segmentation and segregation of employees from critical internal resources. The basic idea is that the internal network is no longer explicitly “trusted.” BYOD policies and the mobile workforce have brought new threats to the internal network that just weren’t there five years ago. It’s no longer practical to assume “bad guys outside, good guys inside.” Let’s take a look at exactly what this means…
The Old Model – Implicit Trust of the Internal Network
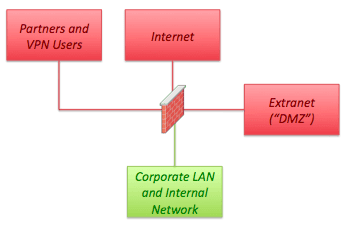
The diagram below illustrates a traditional network segmentation model employed for years by network designers the world over…
In this “inside/outside” model the network designer assumes the “Corporate LAN and Internal Network” is clean. Back in the day smartphones and tablets didn’t exist and most employees used fixed workstations. Also, wireless networks were few and far between. This model worked. Threats originated from the “outside” of the network – the Internet. Security architects would deploy defenses at the perimeter of the network making use of a “DMZ” to house servers and applications that were exposed to the Internet. NATing was enabled for all internal hosts so untrusted Internet sourced packets simply had no way to reach the internal workstations and servers.
I actually remember designing this kind of network many times and thinking “this is good, everything is safe.” For the most part I was right (discounting the fact that even then internal threats were real). But that was the 2003 timeframe. Times have changed. The internal network can no longer be “trusted.” The old model is not good and everything is not safe.
The New Model – Internal Network Segmentation
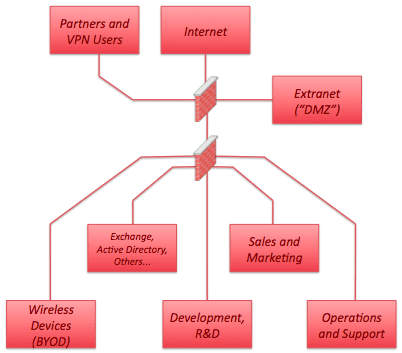
A new design model that’s gained traction recently is the notion of Zero Trust. Introduced in 2010 by Forrestor Research Inc.‘s John Kindervagg, the Zero Trust Model requires that you trust no one, not even your users. When considering network segmentation strategies, you assume that your internal users are just as high risk as packets originating from the Internet. We also have to assume that there are different classes of users. Some will have confidential information on their devices (Execs and development and R&D). These users must be segmented from other users that might seek to steal or extort critical assets. The new model looks something like:
Note we’ve deployed a second port-dense firewall to isolate traffic flows between the various departments. The firewall provides access control between the various user segments and the Exchange/Active Directory/Others critical resources. This model is far more secure but comes at a high cost in terms of firewall rule-base management. Other mechanisms such as Cisco’s Trust Sec promise to allow segmentation without the need for a firewall. Unfortunately TrustSec and similar switching infrastructure-based access control have yet to go main stream.
Network Flow Analysis to Verify Network Segmentation
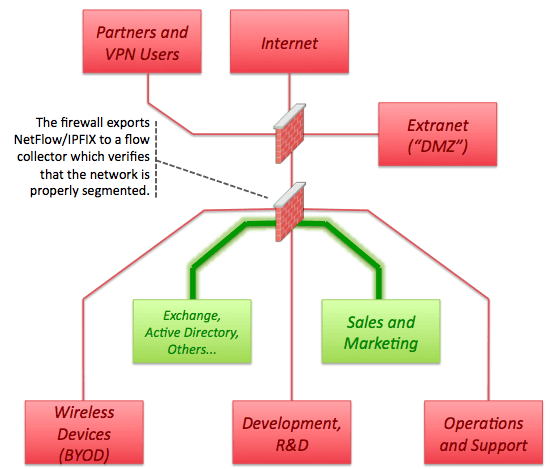
Given the increased complexity involved in managing network segmentation errors in rules often become quite common. One approach to verifying proper network segmentation is through the use of NetFlow and IPFIX. Flows are used to verify that the firewall is doing what it’s supposed to. You can learn more about NetFlow here or just browse the Plixer blog to gain a deeper understanding of devices that support NetFlow and the various problems it can solve. In the example below we assume the firewall shown is NetFlow or IPFIX capable. Many firewalls support flow export. Some include SonicWall, Palo Alto, and Cisco’s ASA. Once NetFlow has been enabled the firewall administrator can run a simple report using a product such as Plixer’s Scrutinizer NetFlow Analysis Platform.
In the example below we first define an “IP Group” in the Scrutinizer NetFlow Analyzer UI for “Exchange, Active Directory” and “Sales and Marketing.” The group will contain the IP ranges from each network segment…
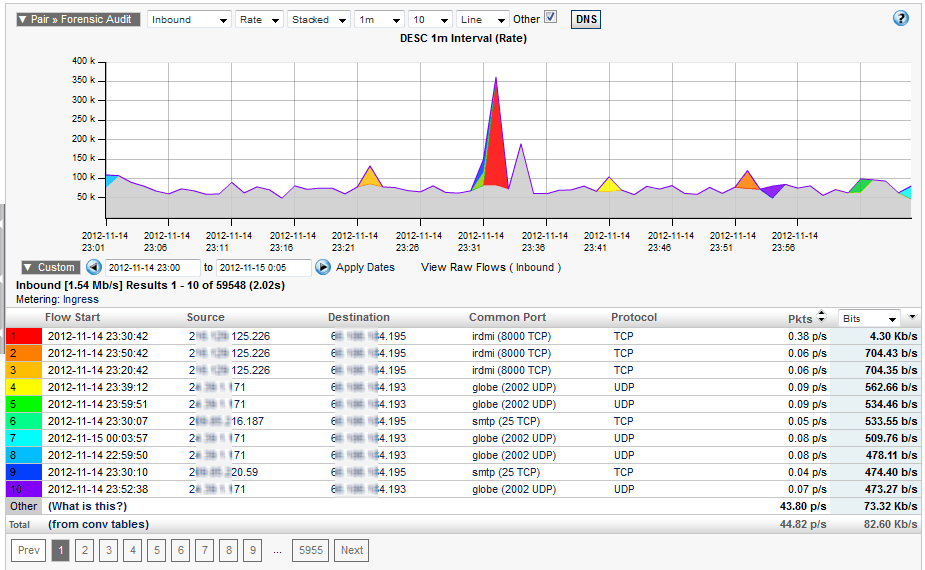
We then run a report for all flows between these two IP Groups and verify the results meet the access criteria we believe to be in place…
The end result is a network in which a single compromise is isolated to a specific segment of the network. This design facilitates strong access control and allows for BYOD and other policies which might otherwise represent a threat to the internal network.
For more information on Zero Trust design and how you can use NetFlow to validate proper network segmentation contact us. Or to get started now download a free copy of Plixer’s Scrutinizer NetFlow Analyzer here.