Network and Security administrators have several monitoring protocols available to help provide network insight and security awareness. Today, I’d like to talk about why flow technologies like NetFlow should be top of mind in this discussion.
What visibility do flow data offer?
Flow technologies like NetFlow and IPFIX provide network visibility at the connection level. As a host on the network reaches out to make a connection to another host the information about that connection is captured in a flow record. As the conversation continues, information about that flow is aggregated and summarized into flow records which give a full accounting of things like application and protocol, class of service, what network device/interface the conversation was seen on, and the number of packets and bytes. Every connection made from one host to another is seen at every hop as the conversations traverse the network infrastructure.
Monitoring protocols like NetFlow and IPFIX are straightforward to deploy. Most vendors today offer flow monitoring as an option. You already own the technology; all you must do is turn it on. Because we are monitoring the traffic traversing network interfaces, we can get nearly perfect visibility across the network.
As flow technologies transitioned from record-based to template-based, vendors were given the freedom to develop their own record content. This allowed vendors the ability to do deep packet inspection to populate flow elements with meaningful metadata like layer 7 application tags, such as host or application latency, packet loss, and jitter. I see firewall vendors exporting firewall event metrics, ACL references, and usernames. All are tied to the conversation data that was collected in the flows.
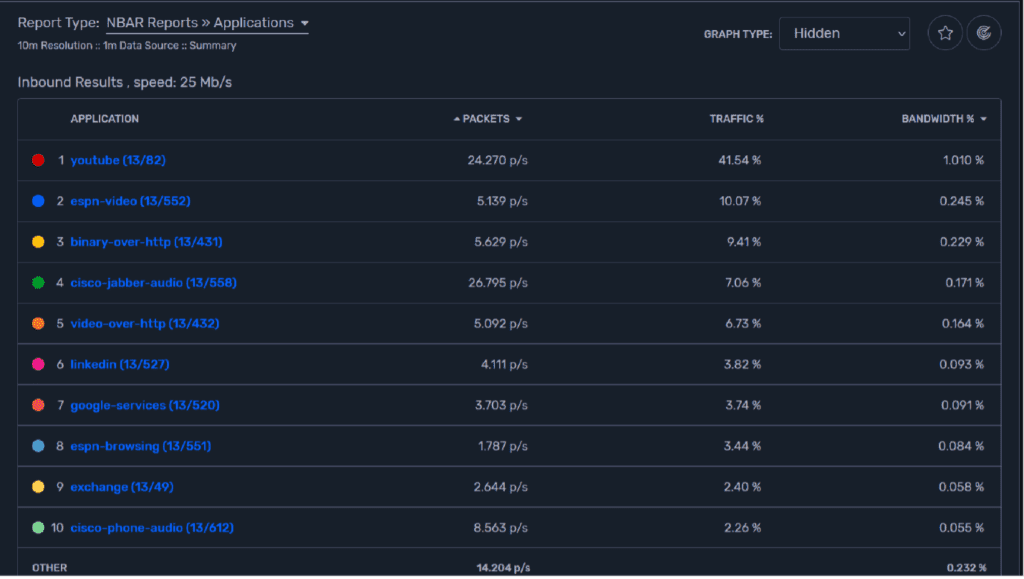
When administrative teams need to understand who and what is using bandwidth, flows provide that visibility. Rich reporting and filtering allow the admin to get right to the conversations that are causing the problems. Every interface on the network becomes an observation point. Technologies like Cisco’s NBAR add application tag metadata to the flow data, so the admins know where the users are talking.
Security teams also benefit greatly from flow data
As with any type of cybersecurity incident, you can only respond against a threat if you are able to detect it in the first place. As you can imagine, detecting potential threats or security incidents in a large and complex network, filled with a diverse lineup of end-devices, routers, and lines of communication presents a major challenge to security teams. NetFlow is one incident response tool that can allow security experts to efficiently detect possible network intrusions and threats, so that incident response can be engaged to mitigate the potential damage ASAP.
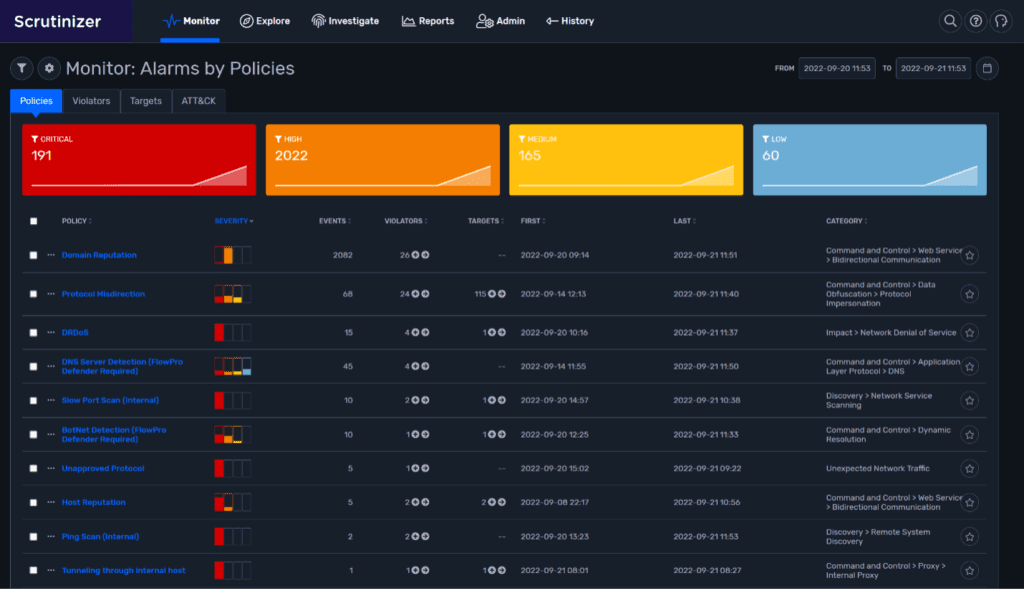
To do this correctly, you need across-the-board visibility in every segment of the network. This is easily done using flow and metadata exported from your network infrastructure.
As I stated earlier, NetFlow and IPFIX are great for knowing the who, what, and when of traffic on your network. By collecting and analyzing flows representing every conversation traversing the network, you gain visibility into suspicious conversations coming in and out of your network, as well as those moving laterally inside.
The use of flow technologies for network behavior analytics is something that Plixer has done for years. In fact, Plixer has been recognized as the Most Innovative in Network Detection & Response. This award validates our efforts to lead, innovate, and shape the NDR market space.
How do flow technologies compare to packet capture technologies?
Deploying packet capture technology in the network can be very costly from a dollar and resource perspective. You end up picking and choosing where you get visibility from. In the end you will rarely achieve anything close to the network visibility that you are looking for.
Instead flows give you top to bottom N visibility, from anywhere in the network. When flow data is collected, the fingerprints/conversations involved in the propagation and/or lateral movement within the network are available for forensic investigation. The flows provide verification and evidence of movement.
When Security administrators need visibility into the east/west lateral movement occurring on the LAN segments of the network, flows easily provide this visibility and awareness.
Is a user downloading movies stealing valuable bandwidth away from the mission-critical applications? Do you even know which applications are running on the network? Who are your top users?
If you would like to get the answers to these and many other questions, feel free to contact the Plixer team and request a POC.