Why am I seeing SNMPv1 and SNMPv2 attempts when I’ve only got SNMPv3 enabled? It appears some of Extreme’s switches handle their SNMP configurations a bit differently. Here, I’ll answer the above question as well as discuss how to configure, enable, and disable Extreme Networks SNMP.
Enable and disable SNMP
Let’s start off simple. I’ve got my new Extreme switch and I would like to enable SNMP. How would I configure this?
Let’s focus on the EXOS Environment since it is the environment that often causes a situation where you’ll notice each version of SNMP attempted even though you’ve only enabled one.
If you are looking for information regarding any of the below Extreme devices please follow this guide supplied by Extreme:
- S-Series
- K-Series
- 7100-Series
- SecureStack
- B5-Series
- C5-Series
The first step is to decide which version of SNMP you would like to use. Once you’ve answered that, log in to your Extreme switch and run the below command to enable SNMP referencing the version you want to use.
# enable SNMP access {SNMP-v1v2c | SNMPv3}
Alternatively, if you want to disable SNMP use the command below:
# disable SNMP access {SNMP-v1v2c | SNMPv3}
Now we should verify that our command was accepted. Run the below command and look for ‘SNMP access.’
# show management
The output should match the below:
switch # show management CLI idle timeout : Disabled CLI max number of login attempts : 3 CLI max number of sessions : 8 CLI paging : Enabled (this session only) CLI space-completion : Disabled (this session only) CLI configuration logging : Enabled CLI password prompting only : Disabled CLI RADIUS cmd authorize tokens : 2 CLI scripting : Disabled (this session only) CLI scripting error mode : Ignore-Error (this session only) CLI persistent mode : Persistent (this session only) CLI prompting : Enabled (this session only) CLI screen size : 24 Lines 80 Columns (this session only) CLI refresh : Enabled Telnet access : Enabled (tcp port 23 vr all) : Access Profile : not set SSH Access : ssh module not loaded. SSH2 idle time : none Web access : Disabled (tcp port 80) : Access Profile : not set Total Read Only Communities : 1 Total Read Write Communities : 1 RMON : Disabled SNMP access : v1,v2c Disabled, v3 Enabled : Access Profile : not set SNMP Compatibility Options : GETBULK Reply Too Big Action : Too Big Error IP Fragmentation : Disallow SNMP Notifications : Enabled SNMP Notification Receivers : Destination Address : 192.168.10.252:162 Source Address : 192.168.10.1 Virtual Routers : VR-Default, VR-Mgmt Version : Not Configured Type : Trap Timeout : - Retries : - SNMP stats: InPkts 12487 OutPkts 12487 Errors 0 AuthErrors 0 Gets 1551 GetNexts 5162 Sets 0 Drops 0 SNMP traps: Sent 20 AuthTraps Enabled SNMP inform: Sent 5 Retries 0 Failed 0
Looking at the SNMP access, we can see that SNMPv1 and SNMPv2 are disabled and SNMPv3 is enabled.
If you have virtual routers, check out Extreme virtual routers SNMP configuration.
Configuring SNMPv3 for EXOS All
Extreme SNMPv3 can sometimes be tricky.
Extreme recommends a Python script to make this process easy. You can find that here, but I will work through the manual process for this configuration.
Extreme provides this as the sample SNMPv3 access configuration:
configure SNMPv3 add user v3admin authentication md5 v3adminauth privacy des v3adminpriv configure SNMPv3 add group v3group user v3admin sec-model usm configure SNMPv3 add access v3group sec-model usm sec-level priv read-view defaultAdminView write-view defaultAdminView notify-view defaultAdminView disable SNMP access SNMP-v1v2c disable SNMPv3 default-user disable SNMPv3 default-group
Broken down, the first line in this configuration references the user.
configure SNMPv3 add user <user> authentication md5 <authpassword> priv des <privpassword>
We need to specify the user, decide on the authentication type (Extreme uses either md5 or SHA1), and include the authentication password, encryption type (des or aes), and the encryption key (<privpassword>).
The second line of the sample refers to the group portion.
configure SNMPv3 add group <group> user <user> sec-model usm
This will tie the user from the previous line to a group.
The third line refers to access.
configure SNMPv3 add access <group> sec-model usm sec-level priv read-view defaultAdminView write-view defaultAdminView notify-view defaultAdminView
This line determines the authentication and encryption level, as well as the group’s access to MIBs for specific functions.
And finally, why am I seeing SNMPv1 and SNMPv2 being attempted when I’ve only got SNMPv3 enabled?
There doesn’t seem to be much documentation on this, but it is becoming a more frequent problem. I took a look into this manual and found it only referenced vaguely once.
It appears that Extreme switches will first attempt each version of SNMP unless certain versions are specifically disabled. Yes, even if you’ve specifically enabled only one version.
The resolution is simple. Using what we’ve learned, we simply log in to our device and disable the versions of SNMP that we are not using.
# disable SNMP access {SNMP-v1v2c | SNMPv3}
Then run :
# show management
And check your SNMP access.
Now that we’ve got our SNMP properly configured we’ll be able to see this change reflected in our NetFlow collector.
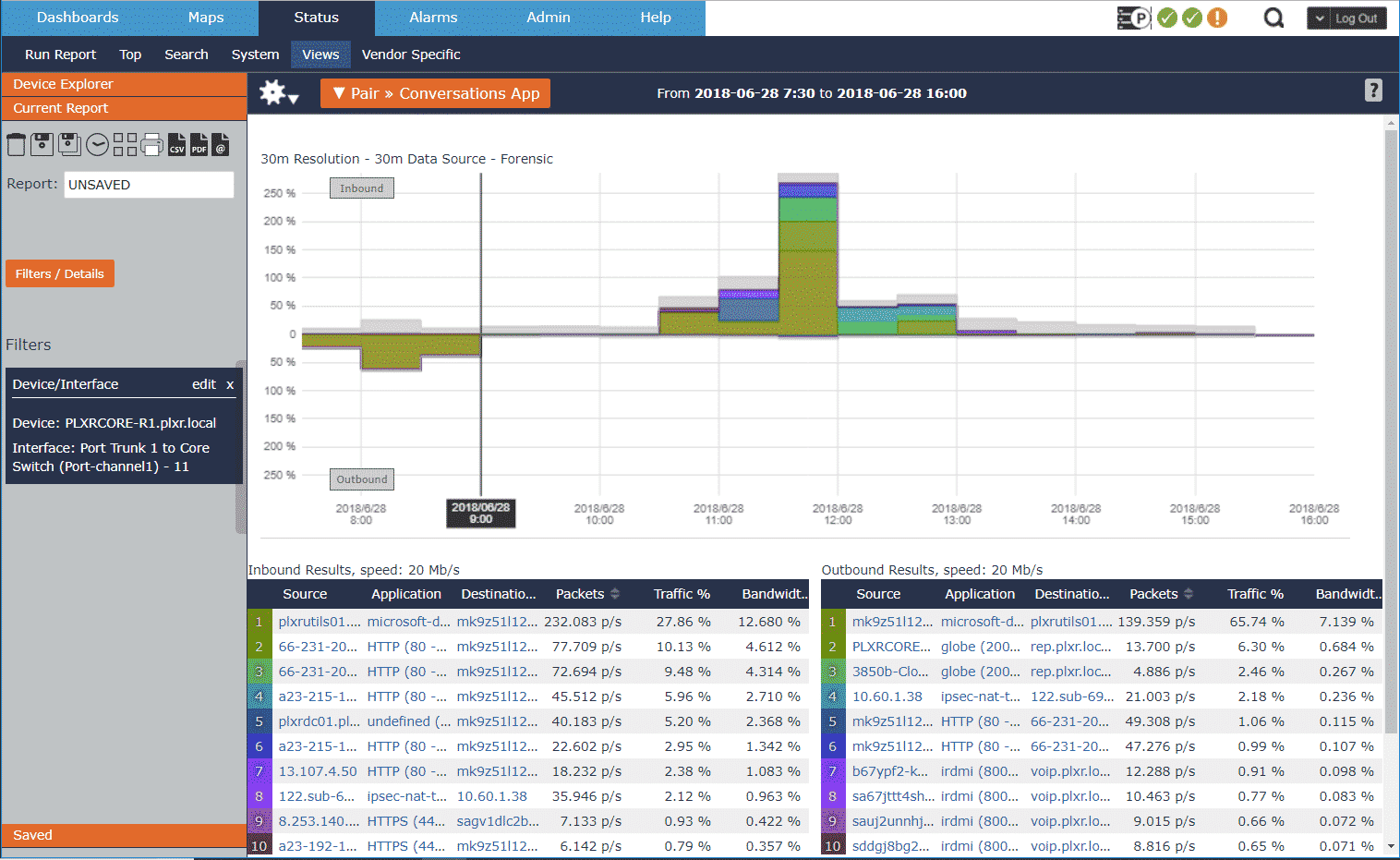
If you want to view the NetFlow data sent by your Extreme devices, try it out in Scrutinizer.