With all of the new movies and TV shows right around the corner, I figured it would be a good time to talk about everybody’s favorite file sharing system, BitTorrent. The ability to detect BitTorrent Traffic is extremely useful, especially concerning matters of copyright.
Before we track down the guilty party, let’s discuss BitTorrent. As of the last few years, anything torrent-related has brought about talks of infringement, lawsuits, thefts, and even downloading cars.
But BitTorrent is more than just a tool for pirates; it is a powerful peer-to-peer communication protocol that allows large files to be transferred with ease. Instead of downloading a whole file from one source, bits of data or “pieces” of the desired file are collected from many other users, or “seeders”. These pieces are then protected by a cryptographic hash, which ensures that it is not modified and then off they go to the intended user. Since the file is being built piece by piece, a user is able to pause / halt the download and take it back up during a later time. During the download process, your system then becomes part of the seed file, allowing for redundancy and speed. It’s a great big share fest and kindergarten teachers worldwide should be proud. Well, aside for the whole copyright, legal issue thing.
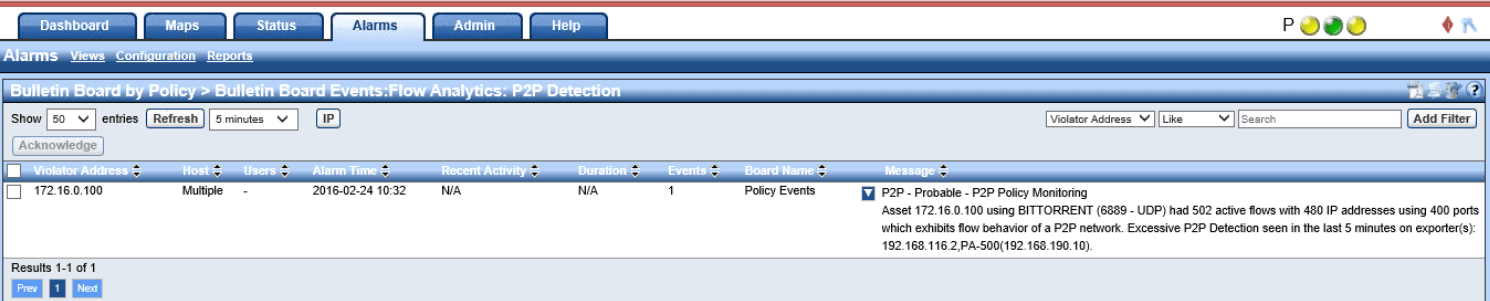
Having the ability to alert quickly and track down BitTorrent traffic is an essential part of network visibility. Universities especially have long struggled to catch BitTorrent users, since it is popular with strapped-for-cash students, and often schools and students must pay hefty fines. With NetFlow we can get to the source of the traffic and set alerts, allowing admins to respond faster.
Setting up reports and alerts to look for the various telltale signs of torrent traffic is made easy with current NetFlow tools and devices.
One method would be to build reports looking for the common well-known ports associated with BitTorrent; common ones are TCP ports “6881 – 6889 and 6969 for the tracker” – https://wiki.wireshark.org/BitTorrent.
We could also utilize built-in algorithms within our Flow Collector to look not only at the port but also the amount of connections made. P2P traffic will commonly reach out to over 100 external hosts during a session thus quickly allowing us to alert on such incidents.
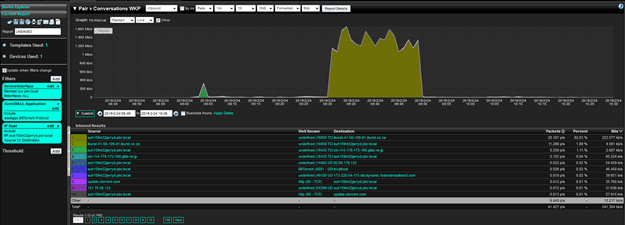
With advances in Flow Technology, Devices can now send us application IDs. We can filter out these IDs within NetFlow reports to show us the time frame and the traffic to and fro. The report below, for instance, was filtered on my IP and the BitTorrent application.
Not All networks are going to be created equal, and this is the same with users. Some users, especially in more of a bring your own device architecture, will be logged into multiple devices. Some users are still in the mindset that because they are on their phones or laps on wifi, that they are in the clear and cannot be seen. This is simply no longer the case as our technology grows.
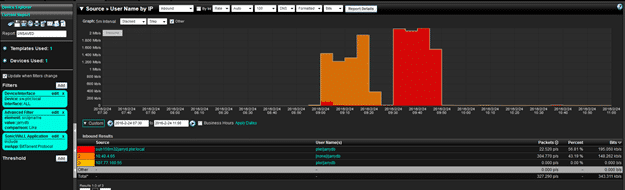
You can use Active Directory or Cisco ISE to pull a report looking for a username that is torrenting. Now you are able to not only see the user, but also the devices that they used to torrent with.