Network forensics can be an intimidating subject. When IT personnel hear the word “forensics” they often recoil with visions of complicated software such as EnCase. Or they may think about expensive packet capture solutions such as Niksun’s NetDetector product line. While these tools can serve a specific purpose, your first line of network forensics defense should always be found in NetFlow and IPFIX…
Network forensics can be an intimidating subject. When IT personnel hear the word “forensics” they often recoil with visions of complicated software such as EnCase. Or they may think about expensive packet capture solutions such as Niksun’s NetDetector product line. While these tools can serve a specific purpose, your first line of network forensics defense should always be found in NetFlow and IPFIX…
Network Flows: An Unblinking Eye On the Network
I don’t want to spend too much time drilling down on NetFlow and IPFIX. The Plixer blog contains tons of information on what network flows are and how you can collect and store them. Check out this post on the basics of NetFlow and IPFIX or the NetFlow Wiki page for a more detailed intro.
In a nutshell, almost all modern network equipment such as routers, switches, firewalls, and even virtualization tech such VMWare support flow data export. As packets are routed across the network small UDP-based messages are created by the network devices. The flow information is then sent to a server called a flow collector. The flow collector can be located anywhere on the network. It’s primary job is to processes and stores detailed information about all the IP communications occurring across the network backbone. You can think of NetFlow and IPFIX much as you would a telephone bill. If the FBI wants to investigate a criminal, they usually start with the phone record. NetFlow provides an unblinking eye on all network activity. The flows don’t contain the actual packet data itself but rather the metadata for the communications. By “metadata” I mean information such as username, source and destination IP, URL, start and end time and much more. Check out this list of NetFlow fields to get an idea of what’s stored by the flow collector.
End to End Network Visibility
One area where traditional network forensics tools fall short is in coverage. While it might be technically possible to deploy hundreds of packet capture devices across every point in the network, the cost would be prohibitive. Packet capture products are best deployed as needed in key locations or when a problem is suspected (ie. reactionary deployment). Network flows can be enabled anywhere you have a router, switch, or firewall and the best part is that you don’t need to deploy hardware via a SPAN or tap. NetFlow and IPFIX are built in. It’s already there just waiting for you to turn it on.
The BYOD movement has brought new threats to the internal network. It’s not enough to monitor just the Internet pipe. We’ve also got to look inward toward the network core and access layers. NetFlow gives us the ability to look inward toward the network deepness. You can find NetFlow support in access layer devices such as the Catalyst 4500, Enterasys S-series, and even Cisco’s popular Catalyst 3750-X (with module). Check out this post for a run down on core switches that support flow export.
Using Flows For Incident Response and Network Forensics
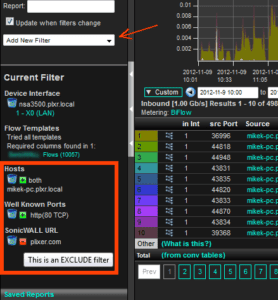
When a breach is suspected and you need answers you don’t have time to pour over terabytes of recorded packet data and you sure can’t visit and analyze every computer on the network to find the extent of the breach. You need to know where to start and drill down with packet-based tools from there. Network flows provide the starting point. Plixer’s Scrutinizer Flow Collector provides a Forensics Report designed to provide a detailed list of flows based on subnet, IP address, port number, or any number of other network traffic attributes…
The analyst simply enters the search criteria and all related flows are returned…
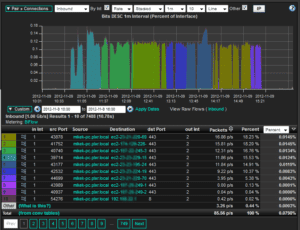
Flow results are returned very quickly with query times normally under 5 seconds. The appliance can offer near instant results. The analyst can click and pivot from one flow to another to quickly hunt down the source or the attack and all hosts that have been impacted. Flows provide an excellent answer to hunting down sophisticated APTs that have moved laterally within the internal network.
Flow Data’s Unrivaled Retention Capabilities
Flow data is incredibly efficient to transmit and store. For each TCP or UDP socket created on the network approximately 120 bytes of flow data will be created. The actual size of the flows varies depending on what fields the router or switch supports. Regardless, Plixer’s Scrutinizer Collector appliance can store months and even years of detailed network forensics flow. Packet capture systems often store only hours of network forensics information. The extended retention capabilities provided by flows can be incredibly useful for governance and compliance such as PCI. Learn more about NetFlow’s benefits to PCI here.
More Than Just a Forensics Point Product
If you haven’t worked with flows you’re selling yourself and your IT staff short. In addition to forensics and incident response capabilities flows provide a wealth of additional capabilities such as:
– Network Performance Monitoring
– Anomaly Detection (DoS, APT, Data Loss, Policy Violation Detection, etc)
– VoIP Monitoring
– Bandwidth Bill-back and Accounting
– Capacity Planning
– Network Forensics and Incident Response
Once deployed, your flow collector can provide value across the whole of IT – from network operations to the security analysts.
Learn More and Get Started
Contact Plixer to learn more about NetFlow and IPFIX. We’ll talk to you about your network infrastructure and how you can use flows to provide 24x7x365 network forensics monitoring of your entire network – from end to end. Or if you want to get started on your own, download a copy of Scrutinizer and get started today.