With the increasing awareness surrounding advanced cyber threats, many companies are taking another look at the firewalls they currently have in place to see if they support flow technologies like NetFlow and IPFIX.
While effective network security targets a variety of threats and stops them from entering or spreading on your network, it helps to understand that no single solution protects you from the massive variety of threats. You need multiple layers of security. If one fails, others still stand. Ideally, all components work together, which minimizes maintenance and improves security.
Enter NetFlow and IPFIX
NetFlow and IPFIX are great for knowing the who, whats, and whens that make up your network traffic. Today using flow technologies to monitor communication behaviors and even maintaining baselines is becoming more relevant. By collecting flows representing all of the conversations traversing the network, you gain visibility into suspect conversations coming in and out of your network as well as moving laterally inside. When the signatures in the IDS/IPS fail to catch malware, NetFlow and IPFIX can sometimes recognize enough odd behaviors to identify an infection. Collecting flows from all of the firewalls, routers, and switches on your network essentially turns each device into a security probe and provides a great security add.
You can think of NetFlow and IPFIX like security cameras. Everywhere you have access to NetFlow you have a security camera and flow collectors that can detect suspicious behaviors.
Let’s take a look at some of the players and what kind of NetFlow and IPFIX reporting is available.
Palo Alto Networks
Exports NetFlow v9 which offers all of the typical TopN (applications, talkers, and conversations) type of reporting. But the Palo Alto firewall does more.
- Using deep packet inspection (DPI), the Palo Alto Networks firewall identifies applications by name (eg. YouTube). Don’t be surprised if it doesn’t identify Facebook and NetFlix as this websites default to HTTPS.
- Integrates with user authentication methods to provide the usernames of the IP addresses passing through the firewall.
- Passes NAT (Network Address Translation) information so you can see who is translated to what?
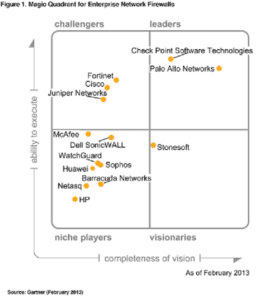
Palo Alto Networks recently received favorable placement in the 2013 Gartner Magic Quadrant For Enterprise Network Firewalls study.
Cisco ASA
Exports NetFlow version 9 records called NSEL (Network Security Event Logging). The flow templates represent the create, denied, and teardown events occurring on the firewall. Reporting from all or each individual template gives reporting visibility into:
- General TopN reporting (Applications, Talkers, and Conversations)
- Top usernames or applications (based on port only) being denied network connections
- The events and access rules (ACL) being violated the most and by whom
- The usernames of the IP addresses passing through the firewall
- NAT (Network Address Translations) who is translated to what?
Dell SonicWALL
Export options include V5 and v9 NetFlow, or IPFIX with extensions. Each offers all of the traditional TopN type of reporting. Like Palo Alto Networks, SonicWALL also does deep packet inspection to identify applications.
If you use the IPFIX with extensions export option you can get:
- Identified Applications (e.g. facebook, netflix, etc.) through DPI. Even if the connection is using SSL.
- Conversations with identified Applications
- Reports on Intrusions, Spyware, and Viruses
- Usernames of the IP addresses passing through the firewall
- URLs
- VPN reporting
- VoIP reporting including Jitter and Packet loss
The SonicWALL also performs SSL deep packet inspection which allows it to extract URLs and other details on HTTPS connections. With more and more cloud applications defaulting to HTTPS, traditional monitoring tactics like packet analyzers cannot see inside the datagrams to extract the HTTP host and URL.
Check Point Firewall
Exports a standard version 9 NetFlow, and offers all of the traditional TopN type of reporting
Blue Coat Crossbeam
Available on the X-Series platform. Exports version 5 and 9 of NetFlow as well as IPFIX, and offers all of the traditional TopN type of reporting.
Solera Networks – DeepSee
Exports IPFIX, and offers all of the traditional TopN type of reporting.
Juniper SRX Firewall
Exports what Juniper labels as IPFIX, but is actually more like a standard version of NetFlow v9. Juniper’s export offers all of the traditional TopN type of reporting.
** Caution: you maybe forced to sample
Astaro Firewall
Exports IPFIX, and offers some of the traditional TopN type of reporting
- There is no export of the ingress or egress interface which is needed in many reporting packages except of course our NetFlow Solution.
- octetTotalCount as well as OctetDeltaCount
- IPv6 Support
- There is an afcProtocol element which links the flow to the afcProtocolName in an options template.
PfSense
One of the packages available on PfSense Firewall is pfflowd, which converts OpenBSD PF status messages into Cisco NetFlow datagrams. This allows you export it to an external collector and gives all of the traditional TopN type of reporting.
Fortinet
Fortinet exports sFlow
sFlow offers all of the traditional TopN type of reports.
If you are looking to rely on the exports from Fortinet from a security perspective,
Here is a little heads up!
sFlow is more of a marketing hoax than it is a true flow technology. In fact, it isn’t a flow technology at all because it only captures sampled packets. When security professionals need to go back in time and view a communication pattern, they find that sFlow seldom samples what you want to investigate. Most vendors supporting proprietary sFlow are starting to abandon the technology in favor of the IETF standard called IPFIX which incorporates all of the NetFlow and sFlow deliverables. When NetFlow and IPFIX aren’t available, consider inserting a NetFlow probe.
Barracuda – NG Series Firewall
Offers an IPFIX export that gets you traditional TopN type of reporting.
As you can see, a majority of Next Gen Firewall vendors are now incorporating NetFlow analysis in their solution. Not only do they provide a means to gather and report on general network trends, but in many cases offer value insight into the events occurring as conversations enter the network.
Can we show you how you can leverage NetFlow and IPFIX to detect advanced persistent threats and provide a total security solution?