With the increasing awareness surrounding advanced cyber threats, many companies are taking another look at the firewall they currently have in place. Palo Alto Networks recently received favorable placement in the 2013 Gartner Magic Quadrant For Enterprise Network Firewalls study.
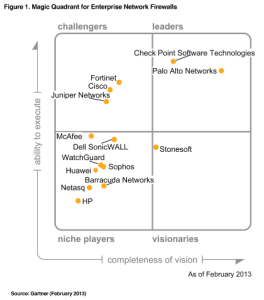
I thought it was interesting that 4 of the 5 firewall vendors listed in the top half of the Gartner Magic Quadrant support NetFlow or IPFIX (I.e. Check Point, Cisco, Juniper and Palo Alto Networks). Several of the vendors in the bottom half such as Barracuda, Dell-SonicWALL and Sophos also support these technologies. This is particularly worth noting because Gartner also recently stated that flow analysis should be done 80% of the time and that packet capture with probes should be done 20% of the time.
Since many firewalls primarily focus on protecting the network from inbound connections, flows can be used to monitor outbound connections as well as other host based indicators which according to Mandiant, is important to monitor when trying to detect advanced persistent threats (APTs). Since NetFlow and IPFIX flows represent 100% of the communications, they can also be used to compare IP addresses against IP reputation detecting-advanced-persistent-threats-with-netflow-and-ipfix.html databases to check for communications with known compromised Internet hosts. This look up process can’t be applied reliably to sFlow exports like those from Fortinet.
“The only people that ever say ‘sFlow is better than NetFlow’ are those that haven’t used both and seen the difference for themselves.” Said Adam Powers –former CTO, Lancope “The NetFlow vs. sFlow war is over.”
“Palo Alto Networks next-generation firewalls coupled with Plixer’s Scrutinizer software enables IT organizations within an enterprise to identify the applications running on their network as well as the end-users using these applications.” Source: Palo Alto Networks and Plixer International Partnership
Collecting flows from your firewalls, routers and switches also ensures that you have a stored history of all communications in and out of the corporate network. If a threat does get past your malware defenses, flow data provides the history of who the infected hosts have been communicating with as well as many important contextual details such as username, URLs, email addresses and more.

