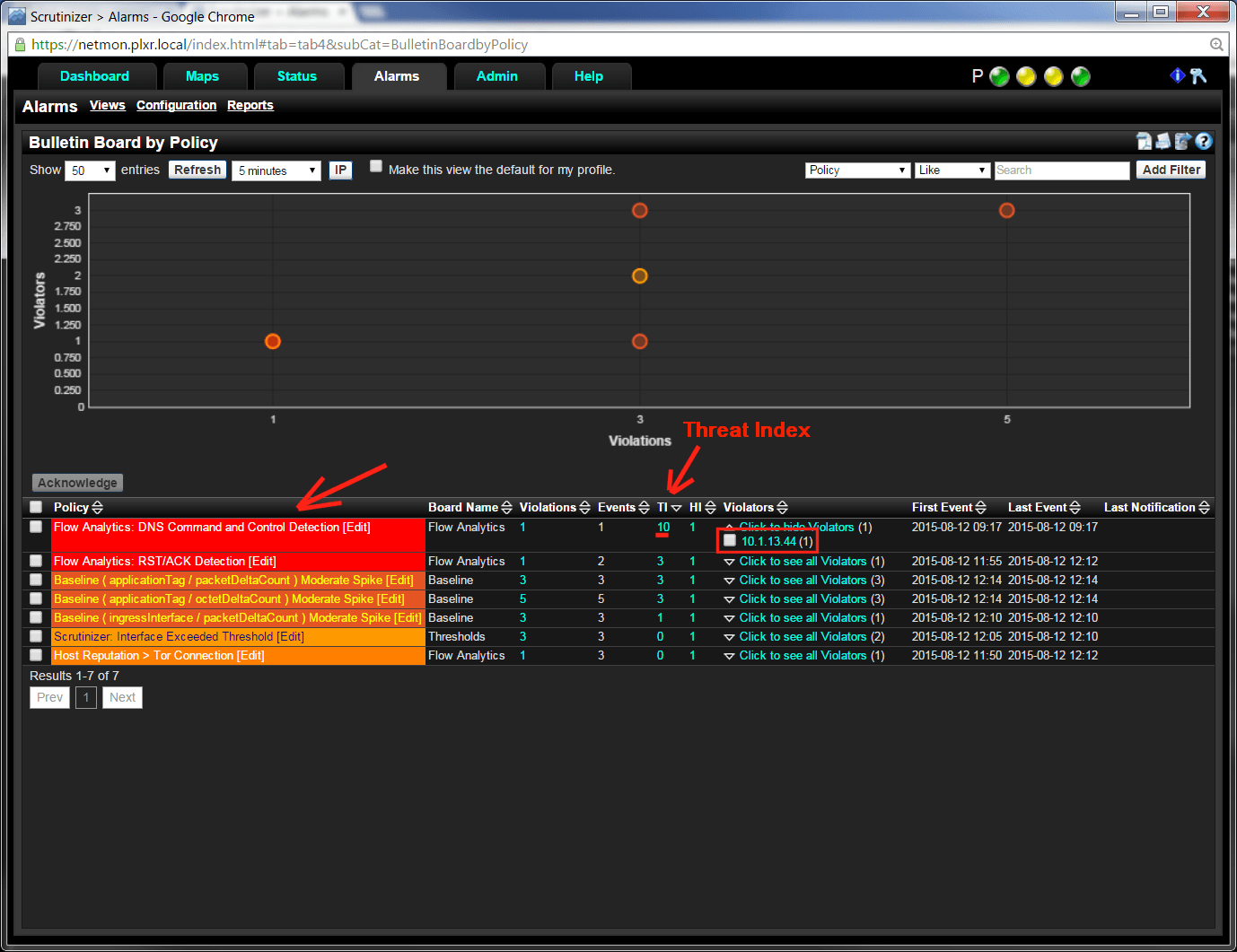
This morning our malware incident response system triggered an event for suspected DNS “Command and Control” activities. Our security team jumped on it and I thought what we learned in the process of following up on the event was blog worthy.
After they drilled in on the event it became clear why Scrutinizer triggered the event. Check out the long DNS name in the image below:
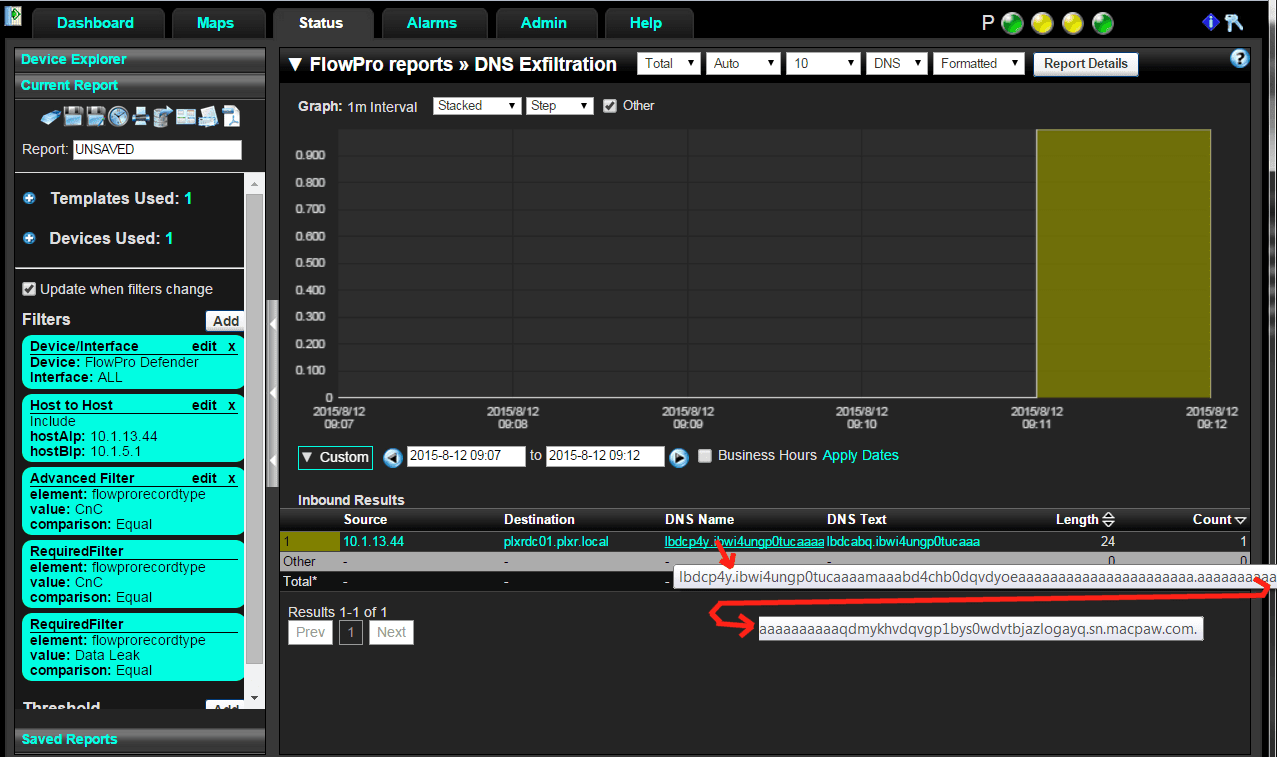
Notice above the crazy long FQDN (Fully Qualified Domain Name). It looks more like an encrypted message than it does a legitimate Internet site! And, notice the odd looking DNS TXT message “lbdcabq.ibwi4ungp0tucaaa”. Very suspicious – looks encrypted.
QUESTION: Who is behind the IP address that triggered this?
Around Plixer, it’s unwise to do anything over the network that could lift an eyebrow. Everyone is constantly looking at our network traffic. The sales people, the marketing people and of course our IT and security folks are constantly bringing up Scrutinizer to figure out what is going on with the network. And since we have our system integrated with both Microsoft Active Directory and Cisco ISE, we were able to quickly narrow in on the specific end user behind what looked like DNS Command and Control traffic.
The user that triggered the event had installed something that he thought would clean up the storage on his MAC and improve performance. How can you fault a person who is simply trying to get more done at work? After a few internet searches, the culprit quickly found plenty of applications that promise to “clean your PC” and “make it feel like new”.
NOTE
Before pulling out your credit card, you should know that malware authors are sometimes behind these applications and use them to propogate their botnets. And guess what, Macs are not safe from malware and the following general rule applies:Don’t install crapware, such as “themes,” “haxies,” “add-ons,” “toolbars,” “enhancers,” “optimizers,” “accelerators,” “boosters,” “extenders,” “cleaners,” “doctors,” “tune-ups,” “defragmenters,” “firewalls,” “barriers,” “guardians,” “defenders,” “protectors,” most “plugins,” commercial “virus scanners,” “disk tools,” or “utilities.” Source: https://discussions.apple.com/thread/5672608
Many of the above applications are useless or worse than useless.
Within a network comprised primarily of Windows based operating systems a stubborn user refused to work on anything other than a MAC and management granted his request. This practice bypasses general active directory security and to make it worse, the user had permissions to install software. Well, guess what….
The user – being a typical user, made a decision to install an application cleaner on their MACBOOK. The System Administrator was notified about the installation when the corporate Security Team passed along an alert that the user’s workstation triggered. It was a very specific DNS based flow algorithm looking for exfiltrated data.
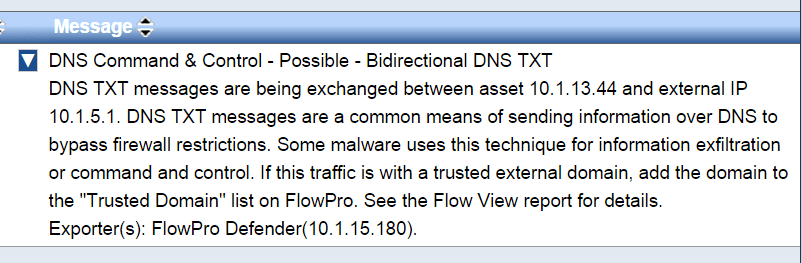
Upon further inspection as shown in the 2nd figure, the DNS request encrypted a message in the DNS name.
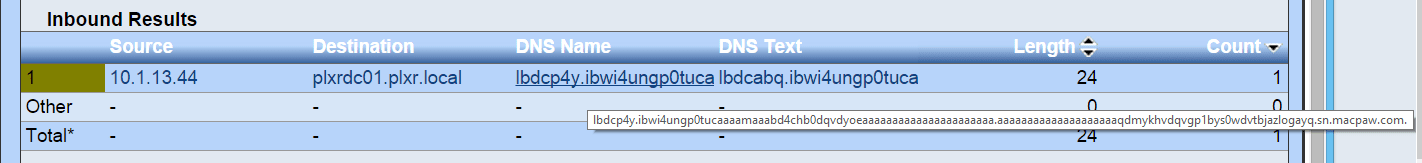
A scan of macpaw.com turned up some malicious links to dl.devmate.com
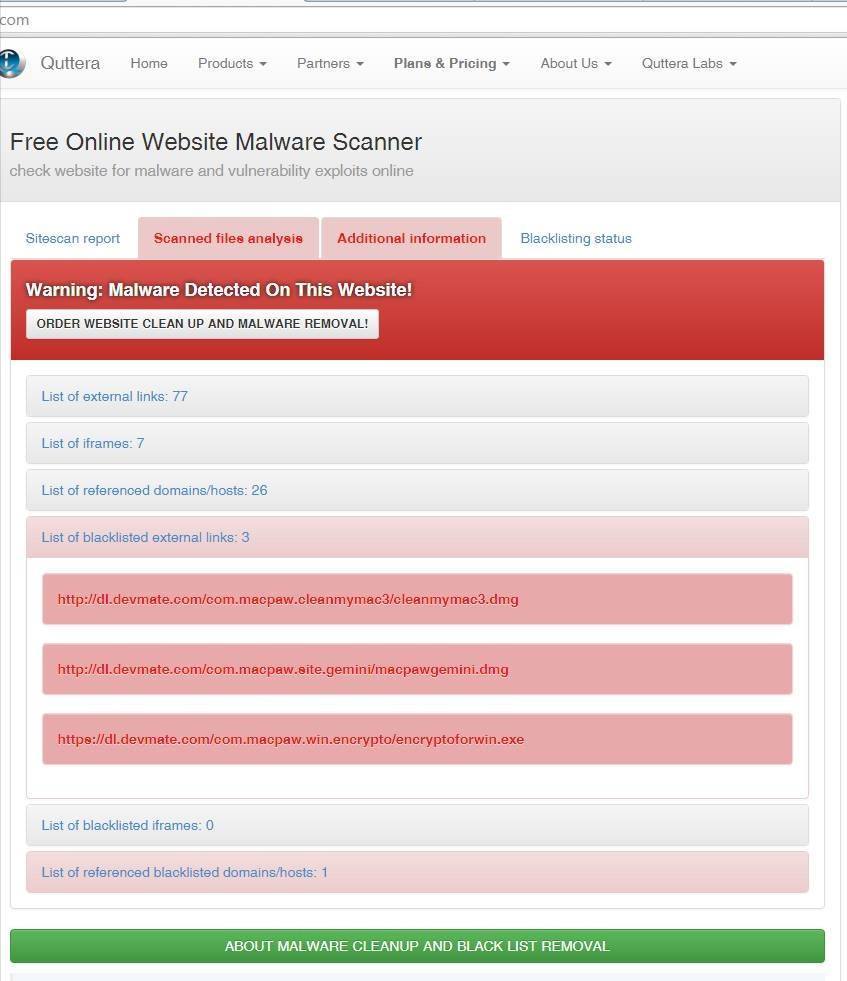
When looking at the URL data for this user, they were able to verify that the user visited on eof the blacklisted external links:
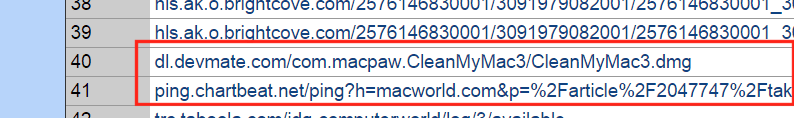
Yah, we caught this one but, who knows what else got past our Gartner proclaimed high and to the right firewalls? That’s right, you’re firewall these days isn’t protecting you from everything evil out on the web.
So, you might be asking “How did we catch this?”. We did it with the FlowPro Defender. This appliance not only exports IPFIX on the traffic it sees but, it also exports DNS communication details and sends them off as flows to Scrutinizer. For years, many forms of malware have been hiding their deeds inside DNS messages. Make sure your security team has something in place to monitor them. Contact us to evaluate FlowPro Defender.