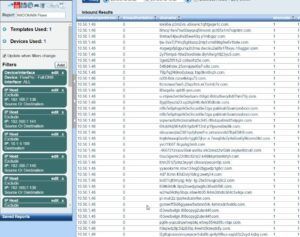
It seems as if monitoring DNS traffic has become pretty popular lately. Our security team just utilized DNS traffic records shown in NetFlow in order to catch an infected Macbook on our Network and just yesterday, we discovered an iPhone reaching out to a plethora of Non Existent Domains.
The most likely scenario is that this user’s system was infected and is now reaching out, trying to find its command and control server to pull down instructions on what to do next.
Say it did connect, and it did pull down instructions from the mothership. At this point, reading this blog, you may be thinking spambot, ransomware, or some other kind of blatant attack. How about simple text message? Maybe the mothership wants the infected system to simply send it a text once in a while.
That’s right—the infected system on your network might be texting the wrong people. By ‘texting,’ I simply mean a TXT Record sent from the DNS system to, in this case, a command and control server.
The TXT record is defined as “a type of resource record in the Domain Name System (DNS) used to provide the ability to associate some arbitrary and unformatted text with a host or other name, such as human readable information about a server, network, data center, and other accounting information.”
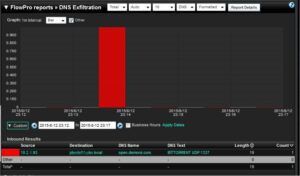
These records will either come off as a string of encrypted text or a simple message as seen below.
This method allows both the good and the bad to bypass firewalls and security systems and gather information. This information could be as simple as an anti-virus program sending home vitals, an operating system checking for updates, or a bad actor finding out that your system is missing the newest security patch and has port XXXX open.
What can you do in this case? Stop DNS? That’s out of the question. With the use of Deep Packet Inspection, you are able to see these potential risks and get some peace of mind when dealing with network issues. Quickly having the ability to see whether a known good actor is simply phoning home or whether a troublesome bot is trying to exfiltrate your data is important and couldn’t be easier.
If you would like some more information about monitoring DNS traffic and getting a better view into your network, give us a call or check out the FlowPro Defender.
For a free 14-day trial of Scrutinizer, Download Now!