RSA 2020 was last week and like every year I have attended, there was a whirlwind of new technologies and methodologies being presented by the vendors I spoke with. Continue on to see what things we learned and how Plixer can help solve problems facing today’s customers.
Network traffic analysis for security
Network traffic analysis (or NTA) has been a feature set heavily used by the network operations teams, but it has only more recently been adopted by the security teams. I spoke with a lot of SOC engineers and incident response teams last week who were unfamiliar with the full capabilities of metadata exports and what information they can provide.
When you start thinking of flow metadata as a phone record of all the network traffic traversing the network, it suddenly becomes apparent how useful this data is for forensic investigations and incident response. In addition to collection, integrating this metadata with your other solutions such as PCAP and SIEMs only adds to the usefulness and helps justify their expensive costs. Feel free to reference my other blogs to see these integrations in action.
Advanced detection and automated response
It comes as no surprise that threats are becoming more advanced and call for more advanced detection mechanisms. Behavioral analysis has always been helpful for detecting zero-day attacks and still has its place, but a growing number of solutions provide DNS visibility as well as information into encrypted traffic. Using these technologies helps with the detection of these threats, but they are usually lacking on the response side.
NTA provides information into the IP communication on the network. But when you need visibility into the endpoint, it often means you will need another solution or an agent-based deployment, which is sometimes hard to scale. Plixer can provide a passive endpoint discovery and profiling solution that leverages the existing infrastructure without the risk of taking network devices offline unless needed. We also provide risk assessment based on a variety of metrics to tell you the hosts that aren’t provisioned properly or need to be patched.
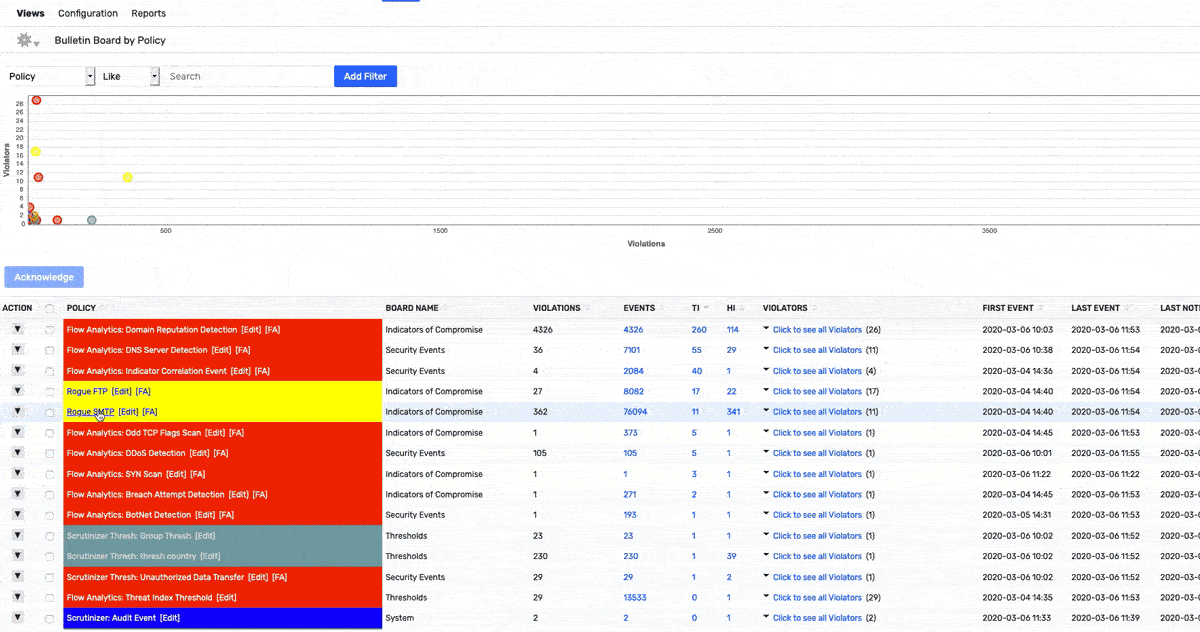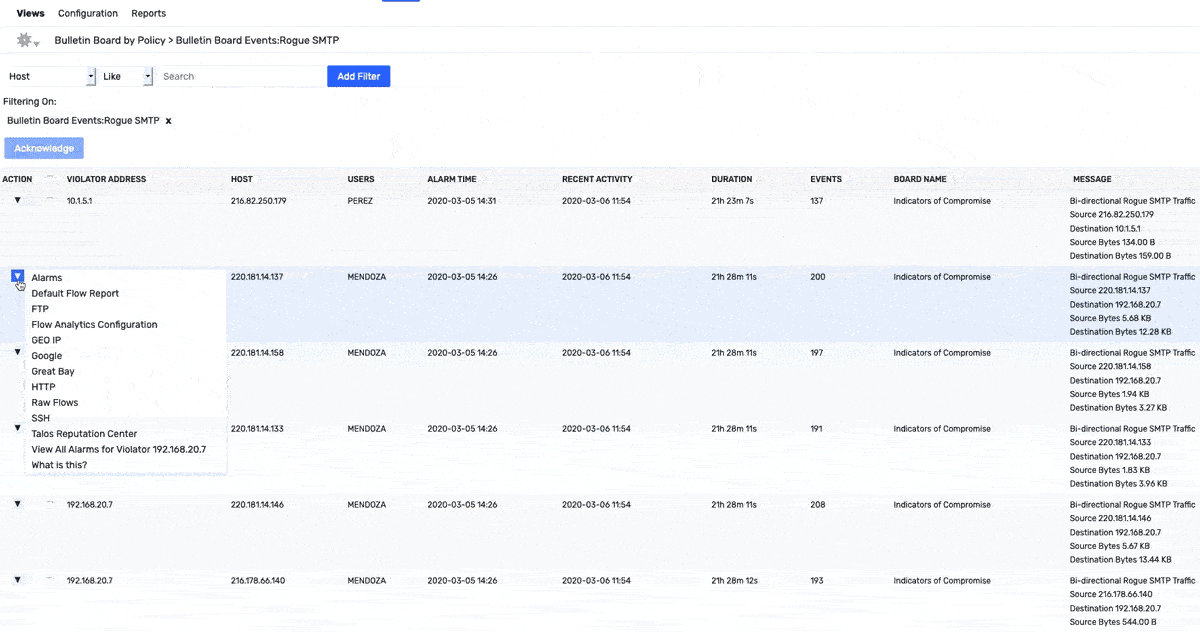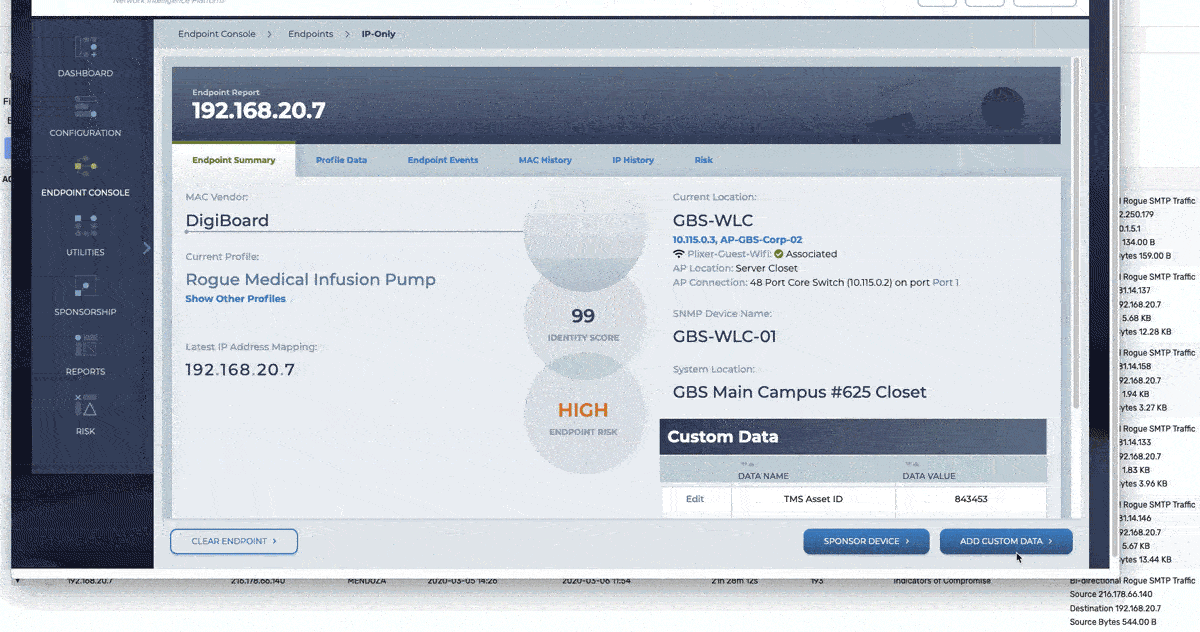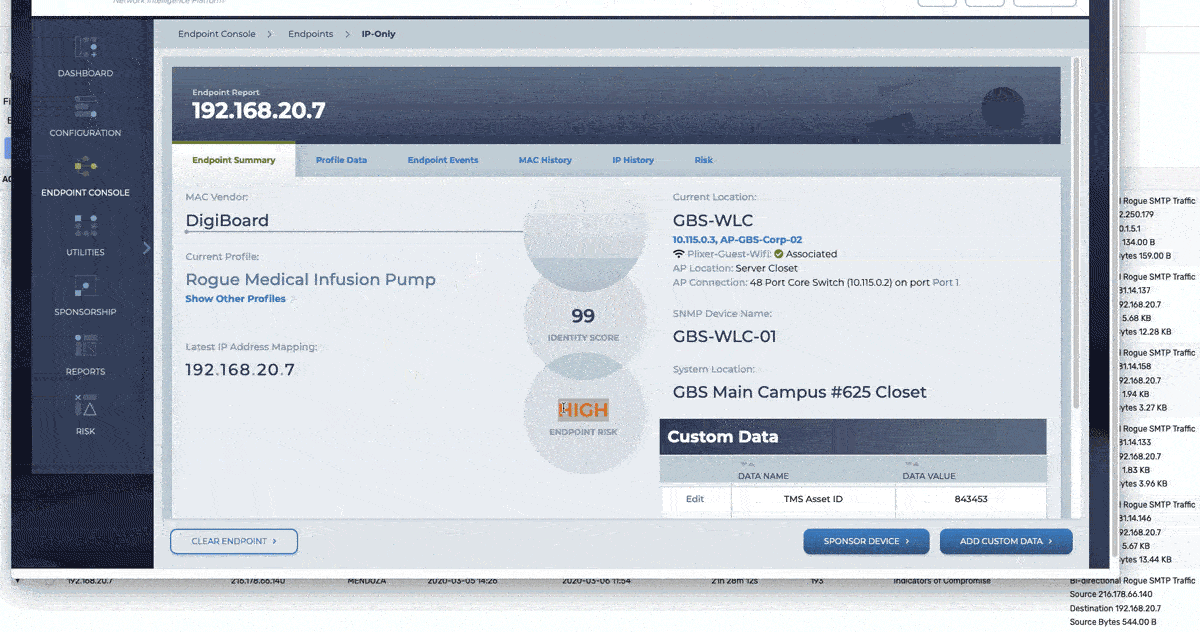
The GIF above shows how an alarm violation for Rogue SMTP traffic, using a simple API pivot we can quickly see that the end system is a medical device that is unapproved for this and take action as needed. I find this example really shows the importance of coupling your NTA and Endpoint profiling products.
Point solutions don’t scale
I’ve always enjoyed going to RSA since I get to see a lot of my customers and talk to them about emerging technologies they’re looking at and new developments. If you follow my blogs, one common thread you might hear is that point solutions (i.e. buying a tool for one specific purpose) don’t scale. I often hear that teams just don’t have the time or the workforce for training and distributing a new tool to the organization.
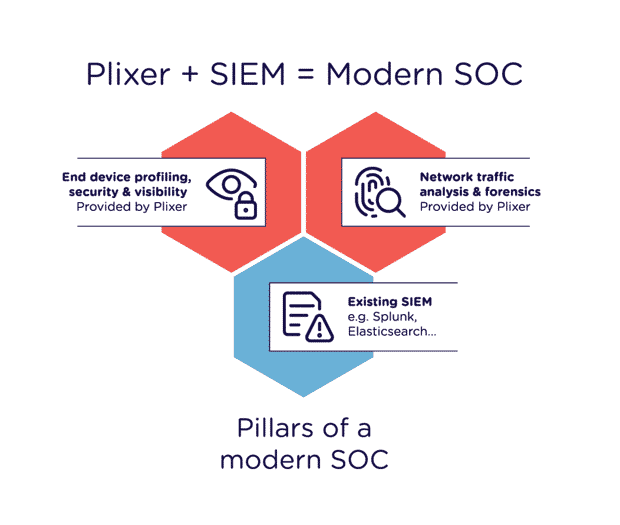
You may have heard of the SOC Triad, which defines the three pillars of the modern SOC (network traffic analysis, endpoint discovery, and SIEMs) as part of their workflows. Plixer covers two of these pillars and offers integrations with a variety of SIEMs to provide enhanced workflows and cost savings on your SIEM licensing.
RSA 2021 and beyond
I think this year’s RSA provided a lot of insight into how the market is recommending modern SOCs be deployed and what tools are required to keep up with the advancement of threats. My guess for 2021 and beyond is more automation around detection and remediation of threats, as well as a lot more use of metadata (for both detection and incident response). If you attended RSA 2020 or have some thoughts on the trends, I would love to hear your feedback! Thanks for reading and make sure to check out Plixer’s Scrutinizer platform to see how we can modernize your SOC.





