
Username Reporting – NetFlow Integration with Cisco ISE
Traditionally in networking, we track down end systems by searching on IP addresses. Although this is a great way to narrow in on an...

Traditionally in networking, we track down end systems by searching on IP addresses. Although this is a great way to narrow in on an...
According to a recent article on BleepingComputer, a backdoor Python library can steal SSH credentials. This can lead to ssh credential misuse if undetected by IT...

Whether it’s after a long day at work, a rainy weekend, or when a new season of your favorite TV show is released, we’ve...

While investigating our SD-WAN value proposition with customers, I worked with one client who has Cisco IWAN for 250 branches uses Scrutinizer to monitor...

According to a recent Ponemon Institute report, the cost of insider-related breaches has escalated to over $8.7 million. What’s even more concerning is that...

When shopping for tools to help with network forensics, you will find many vendors claiming why they are the best, but not necessarily how...
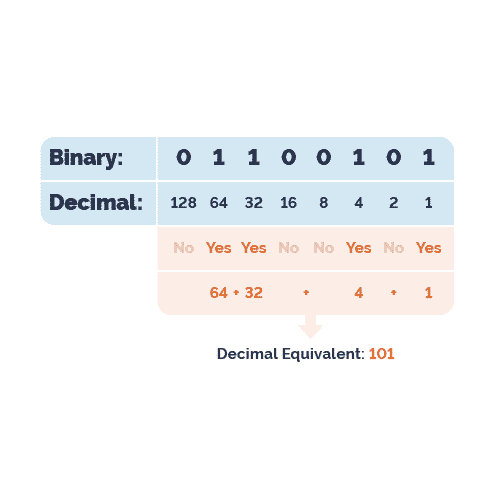
While working with users, I’ve noticed scenarios where filtering traffic based on a CIDR or an IP range just isn’t enough control. I wanted...

I bet you’ve ordered something online at work. It may have been pizza for your lunch or flowers for Mother’s Day (…the day before—hey,...
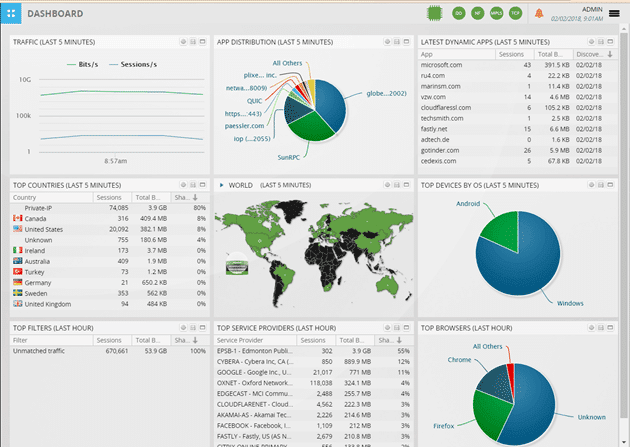
Recently, we decided to deploy an Ixia CloudLens instance in our lab to see what we could report on using Ixia’s IPFIX. Once I...
With the recent news of security vulnerabilities in the Intel Active Management Technology, now seemed to be the best time to share how security...
Looking for documentation? Visit our documentation site