While working with users, I’ve noticed scenarios where filtering traffic based on a CIDR or an IP range just isn’t enough control. I wanted to explore another option—wildcard netmask filters! Let’s walk through how they work, and how they can be applied.
Understanding the Wildcard Filter
The wildcard filter is similar to variable-length subnets. To make the most of these filters, we’ll need a decent understanding of what a netmask is. I think it’s safe to assume we’ve all worked with netmasks in the past, but a quick review never hurts!
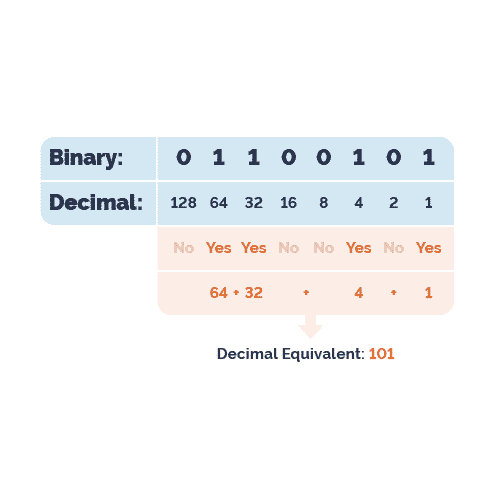
IP addresses are 32 bits long, printed as 32 binary digits each. Typically IPs are referenced in the byte format X.X.X.X. Each X contains 8 bits. For example the IP address 192.168.1.1 can also be represented as 11000000.10101000.00000001.00000001
To break that down, let’s walk through converting the above IP from decimal notation to binary.
Byte value reference chart:
128 64 32 16 8 4 2 1
When we’re going from decimal notation to binary, we’ll work from left to right through each octet. Note that the byte reference chart has 8 digits, making an octet. Working with the IP 192.168.1.1, we’ll ask;
-
- Does 128 go into 192? Yes—with a remainder of 64
- Therefore our first bit will be turned on
- Does 64 go into 64? Yes—with a remainder of 0
- So we’ll turn on our second bit
- Does 128 go into 192? Yes—with a remainder of 64
Since we’re left with no remainders, we know the following 6 bits are turned off. The first octet’s binary value is 11000000. If we continue through the remaining octets, we’ll end up with the binary value of 11000000.10101000.00000001.00000001
Using the Wildcard Filter
So now that we’ve revisited some old theory, how can we apply this to our wildcard network filters? The wildcard filters make use of the same logic, with the exception that they are ignoring the bits that are turned on.
Let’s look at a quick example:
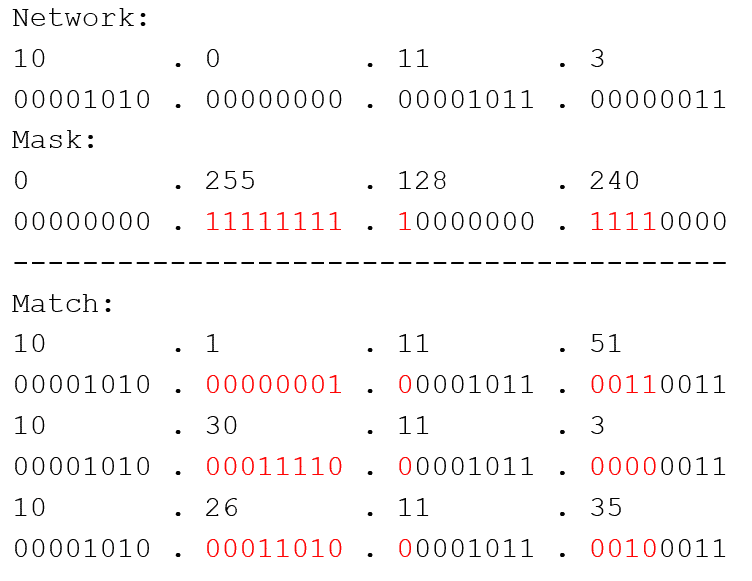
In this example, I have a network that I want to filter on, which is 10.0.11.3. The wildcard mask I apply is essentially telling Scrutinizer, “ignore the bits that are turned on—or red—and show me other networks like this one (while excluding the addresses I don’t care to see).”
A few examples of the hosts this filter would return are;
- 10.1.11.51
- 10.30.11.3
- 10.27.11.3
- 10.26.15.35
- 10.26.11.3
- 10.50.20.3
These filter types can provide a lot of granularity in narrowing our search results, outside of the traditional CIDR notation or the semi-tedious work of excluding multiple ranges.
Applying Filters
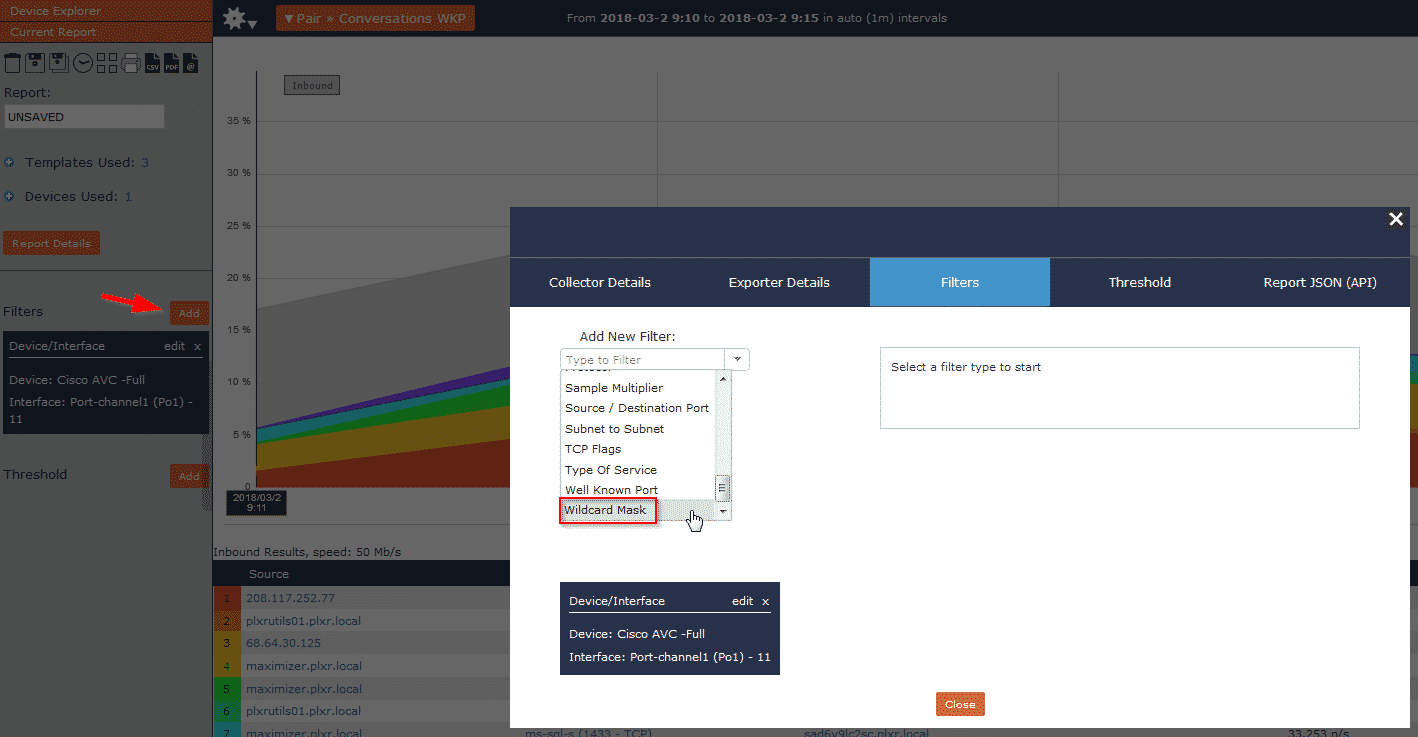
Let’s take a look at how to apply these filters in Scrutinizer.
From within the reporting interface, click the ‘Add’ button to add a filter. Then choose ‘wildcard mask’:
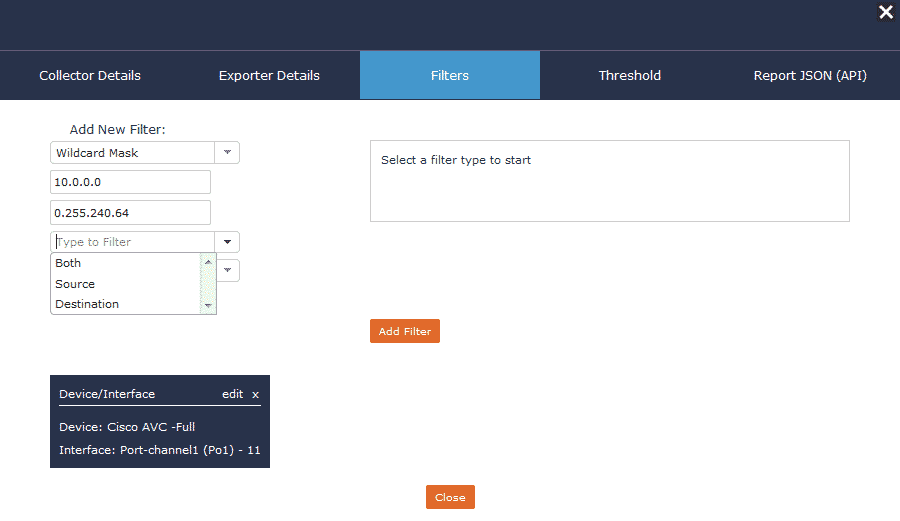
Now we can add our required fields and start isolating segments of our network quickly and easily! Note that for more control, these filters can also be applied to just the source/destination or a combination of the two.
To gain full end-to-end visibility over your network, plus a robust and powerful reporting engine, download and try Scrutinizer for free here!
If you have any questions on filtering functionality, don’t hesitate to contact our support team, or schedule a product overview here.