Are you ready for the end?
January 2020 it will come to an end.
We all knew it was coming. But what now?
Servers that you don’t want to pay expensive licensing to upgrade… Workstations that are still good but Windows 10 is just too heavy for them… What do you do?
Windows 7 end of life date
Windows 7/Server 2008R2 goes end of life January 14th, 2020. Mainstream support ended back in 2015, but we have been receiving critical patches for a few years now. Regular security updates are very important with new vectors of attack coming every day. And you can’t truly depend on anti-virus in the unpatched apocalypse. My argument is not to have the machine or software report issues to you, because those methods can be compromised. Instead, I propose monitoring the traffic going to and from these devices.
With Scrutinizer, we can set IP groups and defined applications coupled with thresholds and filters to remove normal traffic. This way, we’ll only receive emails notifications on traffic that is “unusual.”
IP groups
Traffic to and from your Windows 7 devices looks like any other Windows 8 or 10 traffic. This makes automatic monitoring a little difficult.
With IP groups, you can make groups of devices that are high risk. From Windows 7 machines and servers to your… hidden shame. Yes, I know about that one last XP computer on your network acting as a file share…
If we know the IP addresses or the subnets that these devices reside on, we can build a group for faster report building. To make an IP group, go to Admin>Definitions>IP Groups.
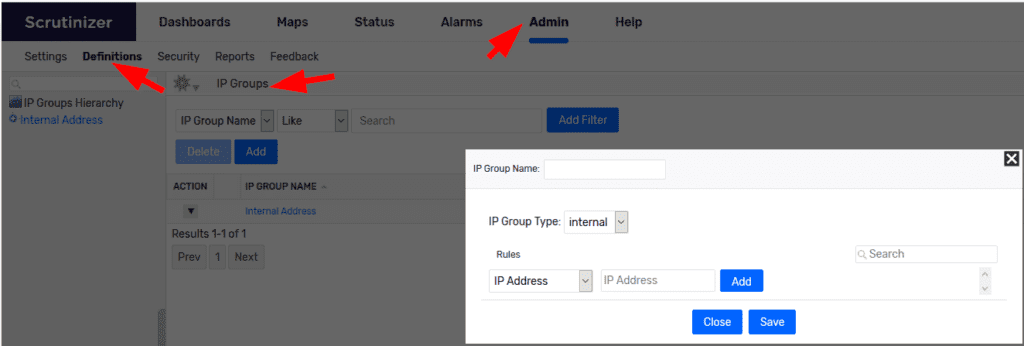
So we have some groups set up. What about use cases?
- Creating reports that filter out internal and your country’s traffic.
- RDP/SSH access from outside your network.
- A report that shows all connections to these devices from inside your network.
One thing I see a lot is Windows 7 & Server 2008 file share servers or FTP servers (sometimes Server 2003…. Sometimes not even R2…). I know that you know that these are huge security risks. So I will not shame. Not even you, Steve.
While FTP traffic from other countries may be normal, I have found SSH sessions from other countries. These sessions are usually spaced out and done during off hours. This is something you want to watch out for. Thresholds are useful here.
Thresholds
You have the report. You have the filters. You can see the traffic on demand.
Now what?
With thresholds, you can set triggers on traffic volume. If the total traffic on the report or on one connection exceeds X, you’ll be notified via email.
To set up a threshold, you need a few things:
- a saved report with a non-custom time frame
- configured mail server settings in Scrutinizer (under Admin>Settings>Email Server)
- a notification profile set in Admin>Definitions>Notification Profile
If you would like help with this, please reach out to us in support.
OK, so all of the above checks out?
Open the report that you would like to have notifications set up on.
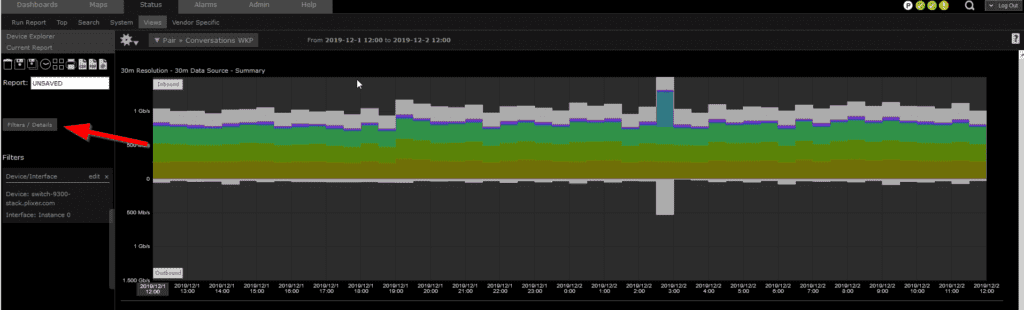
Click Filters, then select Threshold.
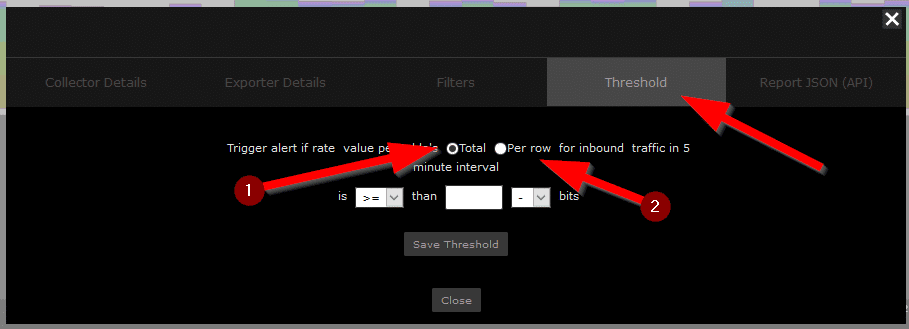
You have two options when it comes to triggers:
- The total amount of traffic for this report.
- The single line item (i.e. a conversation).
Conclusion
Change is good. All things must end. Now that the Windows 7 end of life is here, Scrutinizer can help you with monitoring these older devices and notify you of odd traffic. If you would like to set up any of these alarms, please reach out to us in support. These times can be hard, but we got your back.



