Today I want to discuss how you can use Netflow and IPFIX for network security and even threat detection. There are quite a few different ways we can achieve this either through custom made alerts for suspicious traffic patterns or through our default algorithm based network threat detection routines.
With network security becoming more and more of a concern everyday, now is a great time to start using your NetFlow monitoring solution to proactively detect and neutralize attacks. Working in support we often get calls from customers that want to know who did what and when they did it. The great thing about NetFlow, as opposed to packet sampling technologies (i.e. sFlow), is that we can “play back” 100% of the data that was sent to us and figure out exactly what happened on a very granular, and forensic, level.
“Whereas intrusion detection system (IDS) and packet sniffing software are micro-analytical tools that examine packet contents, Cisco NetFlow is a macroanalytical tool that characterizes large volumes of traffic in real time”
The image to the right shows just a few of the algorithms our NetFlow monitoring tool can report on, as well as some custom reports that we have created. As an example you can see that we have a report to detect Zero Access botnet traffic on our network. This report looks for traffic on the known port ranges of that botnet and sends out an alert when it is violated. When dealing with network threat detection, the best thing we can try, and do, is be 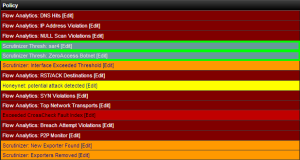 proactive, instead of reactive, to a breach of security; with NetFlow you can be alerted the second one of these algorithms detect a suspicious behavior, whether it be a port 80 DDoS attack, suspicious scans of your network, or excessive DNS requests. See my blog on network security for more information on the network monitoring algorithms we have pre-built in our NetFlow tool.
proactive, instead of reactive, to a breach of security; with NetFlow you can be alerted the second one of these algorithms detect a suspicious behavior, whether it be a port 80 DDoS attack, suspicious scans of your network, or excessive DNS requests. See my blog on network security for more information on the network monitoring algorithms we have pre-built in our NetFlow tool.
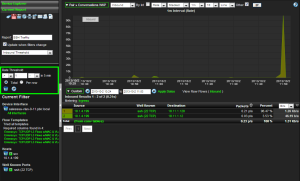
Another example of a custom built alert would look something like the image below. In this report I wanted to see SSH traffic to a certain host and when this was triggered I
wanted to get an email. Since this host shouldn’t be regularly accessed, any SSH traffic that I am unaware of is very suspicious to me. To accomplish this I simply ran a report to get the information I wanted to be notified on (SSH traffic to a certain host) and added an “Inbound Threshold” filter to alert me on any conversations over 1bit. While this report is fairly basic you can add any number of filters to accomplish what you’re trying to find.
Netflow is a great addition to your network monitoring tools and shouldn’t be overlooked when trying to track down an attack or pin-point exactly why your network security was violated. If you have any questions, need any help when setting up and configuring any of our network threat detection algorithms, or want to try and create your own feel free to let us know!