Earlier this year I worked on a document that addressed some of the common misconceptions about Scrutinizer. One of the subjects that caught my attention was Scrutinizer’s ability to mitigate insider threats. Honestly, I really wanted to dig deeper on all the subjects on my list, but the marketing team frowned on me passing along a hundred-page report when they were really looking or two-page fact sheet with links. As time passed, the idea of Scrutinizer’s ability to monitor, detect, and mitigate these types of threats kept on tugging at me. So when I got the opportunity to talk more about it, I jumped on it.
What is an insider threat?
I’m sure that most of you are familiar with what an insider threat is, but I wanted to make sure that everyone reading was on the same page.
“Insider threat is a generic term for a threat to an organization’s security or data that comes from within. Such threats are usually attributed to employees or former employees, but may also arise from third parties, including contractors, temporary workers or customers.” – TechTarget
Scary, isn’t it? A lot of companies are facing the issue where people with varied degrees of technology skills can be a huge security threat. In addition, just the sheer size of some of today’s networks can hinder the ability to understand what a current or former employees is or was doing from day to day. This limits companies when trying to stop insider threats.
Strategy 1: Use metadata to gain complete visibility and stop insider threats
As I mentioned, the sheer size and scope of today’s networks can hinder the security team’s visibility that is needed to detect things like insider threats. That’s where metadata like NetFlow/IPFIX come in.
NetFlow/IPFIX delivers a record of every conversation, along with other important conversation elements, to a reporting/monitoring tool via a UDP stream. Many of today’s networking devices support this type of flow. Using this metadata resource with a reporting/monitoring platform that fully leverages the data allows you to gain visibility across your entire network with far less overhead.
Strategy 2: Have a data retention policy that exceeds that requirements of your compliance or departmental policies
Having a record of every conversation, even the little ones that hang out at the bottom, is no longer a luxury in today’s digital world. With attacks and other nefarious activities running rampant, and with the numerous compliance laws and regulations, the ability to retain conversation data for an extended amount of time is a now a requirement and is vital for stopping insider threats.
Clearly a strong data foundation is important for seeing and stopping insider threats. I have worked with people on both sides of this story. On one side I have worked with companies that didn’t have this historical data and when a threat was detected, they had little information for investigation. I have also worked with people who leveraged their historical flow data to investigate the incident and used that same data to report or monitor other related hosts/conversations.
Strategy 3: Leverage DNS monitoring tools and other threat detection algorithms to identify abnormal traffic
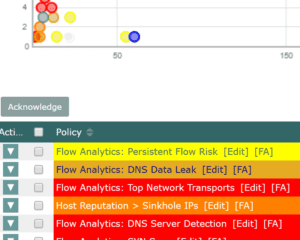 So far, we have talked about the best way to gain the visibility needed to monitor and detect security concerns like insider threats. This data by itself is valuable, but as I have mentioned a couple of times, the size and scope of some of today’s networks can produce an overwhelming amount of information. That is why it is important to use tools that scan flow data for various traffic patterns and detect patterns that look suspicious. This not only cuts down on the amount of time needed to detect a security incident, but also lessens the time to resolution considerably.
So far, we have talked about the best way to gain the visibility needed to monitor and detect security concerns like insider threats. This data by itself is valuable, but as I have mentioned a couple of times, the size and scope of some of today’s networks can produce an overwhelming amount of information. That is why it is important to use tools that scan flow data for various traffic patterns and detect patterns that look suspicious. This not only cuts down on the amount of time needed to detect a security incident, but also lessens the time to resolution considerably.
These algorithms not only help detect attacks, but more importantly, can detect traffic patterns that are related to surveillance and reconnaissance on your network. On that note, I would also recommend that you use intelligence solutions like FlowPro Defender to monitor for things like DNS data links, malware, DNS Command and Control, botnet detection, and Domain Reputation. FlowPro Defender takes DNS traffic and extracts the fully qualified domain name associated with a conversation. This adds a whole new layer of visibility.
Many of the companies that I have worked with have enhanced their security posture by employing these three strategies. If one of your requirements is improving your security posture and gaining deeper visibility but you don’t know where to start? Why not evaluate Scrutinizer?





