Microsegmention refers to the use of software to secure traffic between virtual machines (VMs) within virtualized data centers. Virtualization has increased organizations’ agility and efficiency while reducing cost. The ease and speed at which new applications can now be deployed allows companies to adjust to market conditions, attack new opportunities, compete more effectively, and delight their customers. To be truly effective, however, organizations require open communication and information sharing across their application/virtualization, NetOps, and SecOps teams.

Defining communication policy rules on switches and routers falls within the domain of NetOps. This typically occurs through the configuration of VLANs and access control lists. These hardware-based policies only come into play, however, when traffic traverses the physical network. In many cases, VM-to-VM traffic moves east/west across a virtual switch, staying local to a server.
SecOps is responsible for measuring and reducing risk to the organization. They evaluate and implement technology and processes in the name of risk reduction. SecOps must continually run vulnerability assessments and keep up with a dizzying pace of patch management efforts. They must know what applications are live, as well as understand what operating systems (and which versions) are deployed. Microsegmentation is the mechanism used by the application and virtualization teams to enforce control and reduce risk for this type of traffic. Effective communication and cross-domain collaboration is vital for organizations to properly protect data and applications.
The Rise of Phishing Attacks
Phishing attacks are on the rise, and user credentials are being stolen at an alarming rate. Once bad actors obtain employee credentials, they attempt to move laterally from server to server until they find one where the credentials work. When this happens, they have a foothold. If virtualized data centers and cloud deployments are not properly microsegmented and secured by each of the three business functions, the organization is at greater risk.
There are three main challenges that organizations should take into consideration:
1) Disparate Data Silos
NetOps, SecOps, and the virtualization team each have different tools and interfaces they use to do their jobs every day. For example, most microsegmentation-related products today fall within the domain of the application and virtualization teams. Without API integration across network monitoring platforms, security systems, and hypervisor management tools, NetOps and SecOps can only get the data they need by directly interacting with the virtualization team. This leads to critical errors, workflow gaps, and increased risk to the business.
2) Virtual Machine Sprawl
Creating new virtual machines is incredibly easy and fast. This delivers value to the business, but if left unchecked, can quickly lead to VM sprawl. VM sprawl leads to a scenario where the NetOps and SecOps teams lack knowledge of all deployed VMs. Due to the fact that each team’s daily interaction is with disparate data silos, closing that knowledge gap is a manual process, and one that rarely happens. In my experience in working with NetOps and SecOps teams, there can be up to a 10X gap between the number of VMs that are believed to be deployed versus the number that actually exist. A VM unknown to NetOps and SecOps is a VM that may not be properly secured.
3) Policy Enforcement Verification
As the virtualization team deploys new VMs, they use a management interface (e.g. vCenter) to create policies and define inter-VM communication. Microsegmentation involves logically grouping virtual machines that should be talking to one another. It’s common to only allow traffic between the virtual machines associated with the abstraction layers (web, application, and database) of a single, three-tier application.
This is a good first step for creating policy, but how does the organization know the policy is working as expected? How do they know if/when a bad actor is able to circumvent the rules applied to the hypervisor and virtual switch? How do they identify human error or small security holes that hackers can leverage as footholds?
In short, how do you verify that what you think happened… happened?
Organizations needs two things to overcome this challenge: a way to see the communication in the virtualized data center, and a way to distribute that information to NetOps and SecOps. Both teams must have a mechanism to see into that traffic from the products and platforms they use every day.
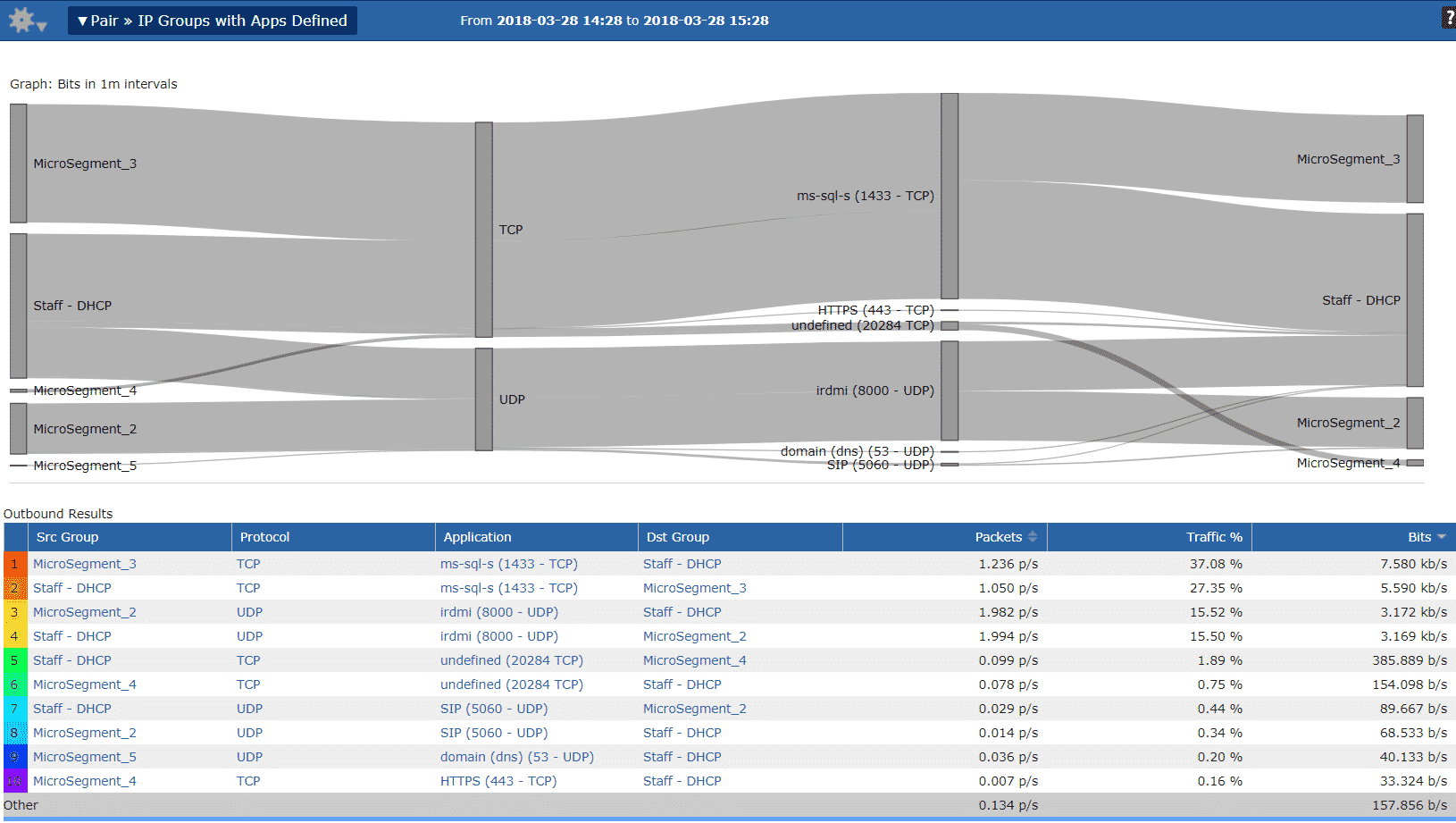
Visualize and Distribute
Network traffic analysis (NTA) platforms like Scrutinizer are an important foundational technology to solve this very real and difficult challenge. NTA collects, correlates, and reports on metadata relating to every conversation that traverses the network infrastructure, both physical and virtual. It allows NetOps and SecOps to visualize VM-to-VM traffic and verify the microsegmentation policies are in fact being enforced. Scrutinizer provides RESTful APIs, both enabling the integration and sharing of data across management platforms and allowing virtualization, application, NetOps, and SecOps teams to most effectively collaborate and reduce organizational risk.
As a related topic, to learn how collect traffic and policy-related data from NSX’s distributed firewall, check out our VMware DFW IPFIX Support blog.





