Face it—the information technology arena is an ever-changing monster and recent news about the increase with IoT vulnerabilities is no exception. A new technology can come around all of a sudden and change how we think and do things. Don’t get me wrong; it’s exciting and it’s what our world has been built on, but it’s also a little nerve-wracking. This becomes a bigger issue in the world of security, since newer technology tends not to be completely vetted.
The Internet of Things (IoT) is one of these newer technologies and is no exception. It will have a huge impact on many industries, but healthcare in particular is poised to reap the benefits of IoT technology. From RFID chips improving operational efficiency to connected IoT devices delivering a constant stream of patient information, this technology will help the lives of many people.
Why is the increase with IoT vulnerabilities a concern?
With this level of adoption, experts are starting to raise security concerns, and not just the normal ones related to data privacy. In a recent HealthcareITNews post, Boston Children’s CIO Daniel Nigrin, MD said that in the past, his concerns were more focused on safeguarding data, but past experience has taught him that it is more than that, specifically regarding security.
As new technology becomes adopted in the healthcare industry, the concept of life-threatening cyber-attacks becomes less science fiction and more reality. For example, the possibility of holding users hostage via Ransomware with their IoT-enabled insulin pump or pacemaker helps validate the reported increase with IoT vulnerabilities. Although there are no documented cases of this as of yet, the FDA issued a letter earlier this year warning hospitals and patients that a pump commonly used to ration out proper dosing of medicine in IVs could be vulnerable to attack.
“Medical devices and Internet of Things devices, such as smartwatches and web-enabled appliances, involve incredible security risks because in most cases manufacturers have not been sensitized to the issue of healthcare cybersecurity and have not embedded necessary safeguards,” – Daniel Nigrin of Boston Children’s Hospital
Another example are IoT-connected pacemakers, which have a similar vulnerability. In an industry brief titled “Combating the Ransomware Blitzkrieg” the authors outline a possible attack where something simple like light encryption can decrease the battery life. The report goes on to suggest that it isn’t inconceivable that the battery life of a pacemaker could be reduced to a point where the time required for an emergency operation becomes a concern.
How do you monitor for IoT vulnerabilities?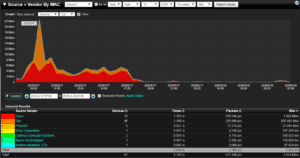
In network security there is no silver bullet and there’s definitely not one solution. Currently, organizations need to monitor all devices, virtual machines and cloud-based applications, but as you guessed, the concept of IoT and the reported increase with IoT vulnerabilities also launches a new era in network monitoring. This means that the amount of data that needs to be monitored is evolving and constantly growing.
Not only is it growing, but due to the uniqueness of “things” and applications, many of which we probably even can’t think of today, it’s difficult to have a single solution that covers every possible scenario. This is where NetFlow and IPFIX come into play.
As my buddy Jake mentioned in his blog on monitoring the Internet of Things, NetFlow is great for providing us with detailed metrics on all network traffic. Since your IoT devices will be communicating on your network the transition to monitoring their traffic should also be applicable in some form or fashion. In his post, Jake gives an example of being able to monitor these 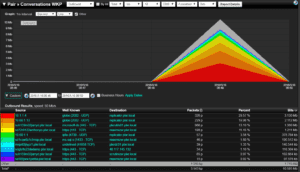 devices by using features like IP Grouping and the Vendor by MAC reports to identify traffic from IoT devices. With this technology we can also see whether you are no longer seeing data from those devices, whether those devices are communicating with mission critical applications, and can get you the detailed information you need when something nasty is happening.
devices by using features like IP Grouping and the Vendor by MAC reports to identify traffic from IoT devices. With this technology we can also see whether you are no longer seeing data from those devices, whether those devices are communicating with mission critical applications, and can get you the detailed information you need when something nasty is happening.
As I mentioned above, the world of technology is ever-changing and you need to make sure that the monitoring technology you invest in today is flexible enough to bend with what you adopt tomorrow. That is why we focus on supporting all flow technology because in itself, the industry standardization of flow technology (NetFlow, IPFIX, etc.), lends itself to this flexibility.
In the end it is all about having multiple layers of security and complete visibility into your network traffic. If you would like to learn more about how Scrutinizer can help you stay vigilant and be a valuable asset in your Cyber Incident Response System, give us a call and we will be more than happy to help you.