With cellular networks taking over the world and nearly every person joining team Apple or Android, it’s easy to see why the evildoers of the world are taking advantage of the boom and riddling us with malware-infested phones and apps. The scary part is that these phones could be on your network as we speak.
 It’s 2017 and pretty much everyone has a cell phone at this point. This particular author is part of team Android and whilst researching a blog topic in regards to VPN applications, happened to fall into the world of mobile phone malware.
It’s 2017 and pretty much everyone has a cell phone at this point. This particular author is part of team Android and whilst researching a blog topic in regards to VPN applications, happened to fall into the world of mobile phone malware.
According to industry security leaders Kaspersky, McAfee, and Sophos, we are looking at another year of increased growth with mobile phone malware. Trojans, adware, root kits, and SMS phishing seem to be gaining strength and putting us as at risk.
Stagefright
Stagefright, so named for the libraries that many applications share, is incredibly threating malware whose remote code could be executed simply by sending a specially crafted MMS message to a victim’s phone. No need to click on a link or do anything; this can all occur during your sleep in as little as 10 seconds. Once your phone has been infected, the attacker has full access. Photos, videos, contacts, etc. are at their disposal. There’s no way to stop it other than to wait for manufactures to patch the phone.
SMiShing
SMS phishing is one of easier ways for attackers to quickly gain access to your gear. We all know about phishing, right? Well, now it’s not just your email that you need to pay attention to. Ever get an odd text with a link from a number you don’t know? Similar to an email phishing scam, after you click these links, you can be redirected to sites you may not want to visit or a payload can be downloaded directly to your device.
Why me?
Why not? IoT (Internet of Things) is the new norm. With everything from your lights, car, and microwave being connected to the internet, it is easy to see the allure to collect them all. Now think for just a second: how do you usually control IoT devices? Or better yet, what device do you use all day that continually sees your private information? If an attacker can control your phone, they can control you. Messages, emails, videos, voice, banking credentials—all of these things can be found on one single device and it’s terrifying.
But don’t take a sledgehammer to your phone just yet. I am in the same mindset; like most people that use a phone and download apps, I find what I want, download, accept the EULA, and then I’m off to the races. In this case, the fine print in the EULA did specify that information would be taken. But most apps say they will take some data, right? That’s expected, but should it be? The second I turned on the application, it started sending out a mass amount of POP3 and Telnet traffic to a variety of servers around the world. 5 minutes after this, our NetFlow collector alerted that it was seeing odd traffic.
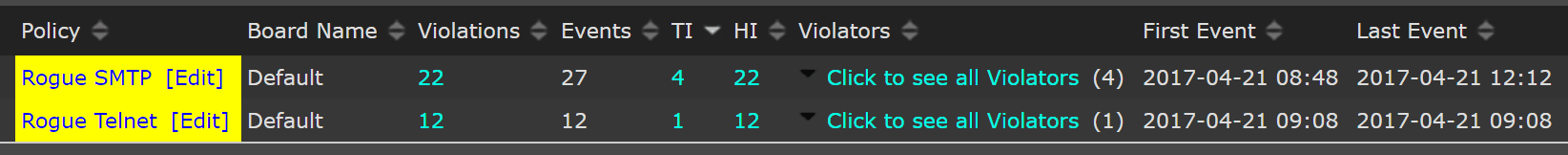
I immediately turned off my phone and started thinking of what could have been taken. Was this an outside attacker or was this part of the application, or part of the EULA I signed? Contacts, emails, pictures, and my banking credentials all could now be in the ether due to a simple click.
Luckily, my network security team found the issue within minutes using Scrutinizer and its Flow Analytics. I was able to be notified and take care of it. But that got me thinking, what about people that aren’t using NetFlow / IPFIX to monitor their network? How do they know there is potential mobile phone malware? It seems to me that with the increase in mobile malware and in Big Brother-style data exfiltration, we should all remain vigilant, especially in our work network environments.
Make sure you read EULAs, do not click on odd links, and make sure to be careful when going mobile on your network. This was a scary and embarrassing problem that without the quick alerting provided to me by my team, I would never have caught.
If you are worried about malware-infested phones on your network or just don’t know what threats are currently floating around, contact us here at Plixer and download Scrutinizer today!



