In 2011, computer scientists at Lockheed Martin established a framework that defined the steps taken by bad actors as they target and attempt to breach an organization. They called the framework the intrusion kill chain (now commonly called the cyber kill chain) and it consisted of seven stages, which I will discuss below.
Looking at things through a lens focused on the seven stages, organizations can establish controls and deploy technologies to reduce risk. There are many technologies commonly deployed in the name of risk reduction, like firewalls, anti-virus, intrusion prevention systems (IPS), and security information and event management (SIEM) platforms. One system that is often overlooked, however, is metadata and NetFlow analysis, which provides a highly valuable source of information to catch cybercriminals in the act. For Plixer customers, Scrutinizer is a critically important component of this model. It effectively identifies malicious activity across many steps of the kill chain and maintains forensic data of every conversation that traverses the network. When considering the seven stages, an ecosystem approach is an appropriate security strategy. This is not a “one product fits all” scenario. Within this blog, I will review each stage and discuss how metadata and NetFlow analysis delivers additional value.
1. Reconnaissance
The first step bad actors take is to identify a specific target organization or network and poke around, looking for vulnerable attack surfaces. Some of these efforts are based on social engineering or other mechanisms that are not technology-related; others include phishing and probing the network. Scrutinizer sees every conversation on the network and is therefore great at identifying scanning, lateral probing, etc.
2. Weaponization
After a cybercriminal uncovers a vulnerability during their reconnaissance, they create a malware weapon. This weapon can either be a customized zero day attack, or a well-known exploit. The weapon is created, or chosen, to exploit the target’s specific vulnerabilities.
3. Delivery
At some point, the cybercriminal has to unleash their chosen malware weapon on the target; here there is an opportunity for the target to discover them. There can be many mechanisms of delivery, but if the weapon is delivered via IP packets across either the wired or wireless network, Scrutinizer will have captured this traffic. Thousands of traffic-related data elements for every conversation, from layer two through layer seven, are accessible at any time within the historical forensic database. In addition, Scrutinizer runs security algorithms against all of the data it collects to monitor for anomalous behavior. This provides an alerting mechanism for catching zero day attacks.
4. Exploitation
Once the weapon has been delivered to the vulnerable device, the code is executed. If successful, the cybercriminal compromises the device.
5. Installation
At this point, the malware infects the device. Scrutinizer uses security algorithms to monitor for any changes in end-user and network behavior resulting from a day zero or well-known attack. In addition, if the malware is transferred across the wired or wireless network, Scrutinizer will have recorded that conversation and stored it in its forensic database.
6. Command and Control
Once the cybercriminal has gained access, they can control the device and execute commands remotely. Scrutinizer monitors all conversations and can filter, report, and alarm based on any of the thousands of traffic-related data elements it gathers. In addition, Scrutinizer has several mechanisms like IP and domain reputation, reverse DNS lookup, ToR connections, etc. to monitor for command-and-control communication. Scrutinizer can also alarm on traffic based on country of origin.
7. Actions on Objective
Now the intruder takes action to achieve their goals, which may be data exfiltration, data destruction, ransomware deployment, etc. Scrutinizer gathers data from all corners of the network, visualizing and reporting on every flow traversing the network, including data elements that extend all the way to layer seven.
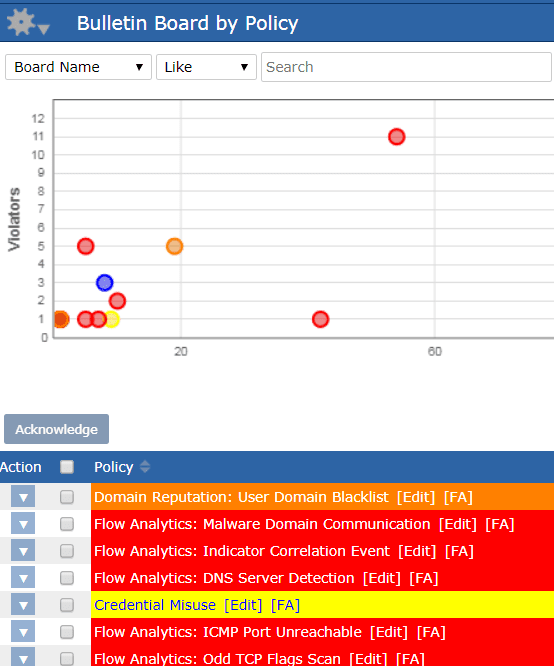
Summary
The sophistication and complexity of today’s cybersecurity landscape is driving IT professionals to rethink their approach to security. It is not a question of whether a security breach will happen; it is now a question of when it will happen. Organizations must have an ecosystem of solutions in place capable of monitoring for, alerting on, and enabling action aligned to the kill chain stages. Scrutinizer gathers thousands of data elements correlated to every conversation on the network, providing forensic data essential for effective incident response. It uses behavior analysis to alert on security events and integrates with third-party SIEMs like Splunk and Elasticsearch, as well as deep packet inspection platforms like Endace. Metadata and NetFlow analysis provides critically important forensic data and should be included as part of every organization’s security ecosystem.
For more information on how to use NetFlow and metadata to identify breaches and reduce risk, check out this blog I recently wrote: WannaCry Ransomware – How Scrutinizer Customers Can Reduce Risk.