Last year Plixer released version 19 of Scrutinizer, and with it came the introduction of Plixer Security Intelligence, our machine learning appliance.
The ML appliance learns and establishes what is normal in network traffic behaviors across hundreds of data models. When Scott’s PC reaches out to an application that he has never touched, or exhibits out-of-the-ordinary traffic behaviors, that activity is flagged and alarmed on.
Pretty cool stuff!
You might ask, “If we are detecting anomalies and deviations from the normal traffic behaviors, isn’t that detecting possible malware variants?”
The answer is both yes and no.
Plixer is very good at detecting suspicious or anomalous traffic behaviors. We continually monitor for and detect behaviors like scans, data accumulation, data exfiltration, tunneling, and worm activity. So, behaviors related to malware are detected and alarmed on. We never put a name to the behavior, but we can now!
What is supervised machine learning?
In this system, the models must be trained. This requires human input to define labels that represent what is a normal state, or normal data. The input data, provided by humans, is manually associated with the desired output.
To put it simply, models are trained with input that results in a predicted output.
Using supervised machine learning, we can detect and alert on named variants of different malware families like banking Trojans, coin miners, and remote access Trojans.
So instead of an alarm telling you that Scott’s PC reached out to 50 assets on the network with activity that is worth looking into, we have an alarm telling us that Scott’s PC generated malicious traffic related to the banking Trojan malware family.
Time to investigate an alert
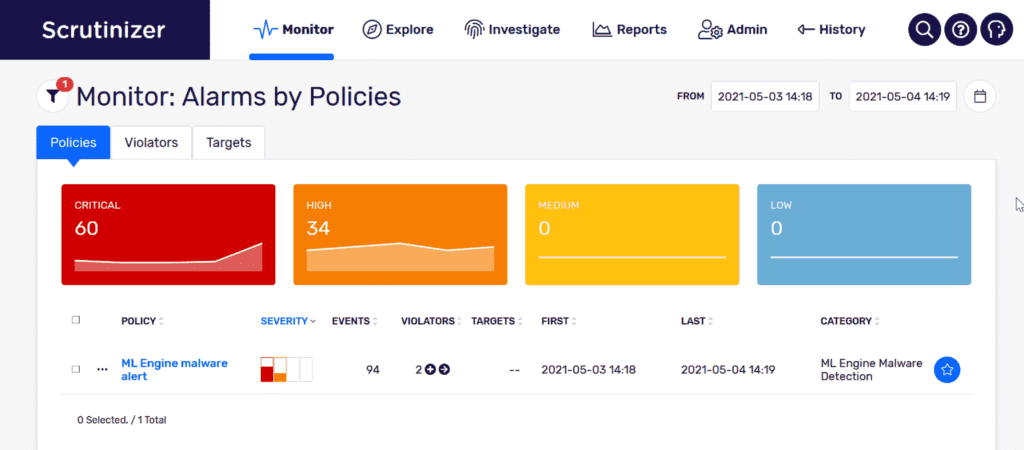
I see that my ML engine has discovered and alarmed on a malware alert. I can see first and last timestamps, so I know when the event first and last occurred.
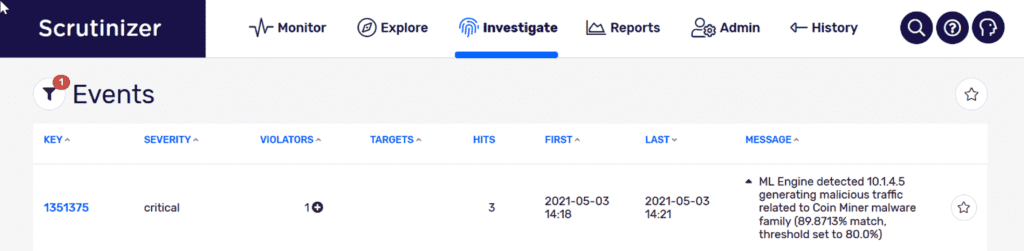
When I pivot into the alert, I can see that in a 3-minute window, IP host 10.1.4.5 generated malicious traffic related to the coal miner malware family. I can also see with about 90% certainty that this is a match.
When it comes to collecting and reporting on NetFlow and IPFIX, Plixer is world class. We provide an accurate accounting of every conversation traversing the network, stored for as long as you need it, using an option that likely already exists on the network devices that you already own. No need for taps or additional appliance infrastructure. The forensic data required for investigation is at your fingertips. When it comes to the detection of network traffic anomalies, fast and actionable data is enterprise intelligence. If you want to see Scrutinizer and Plixer Security Intelligence in action, book a demo today.