Recently one of our employees experienced a DNS hijacking attack while trying to visit a company’s website to learn more about them. You have probably experienced DNS hijacking at some point; your TCP/IP configuration is subverted to point at a rogue DNS server under the control of an attacker. Essentially the website you tried to visit was somehow redirected to a domain chosen by the attacker. In the case of our employee, the site that he was redirected to served up a pop-up that warned of malware on his PC.
The Story
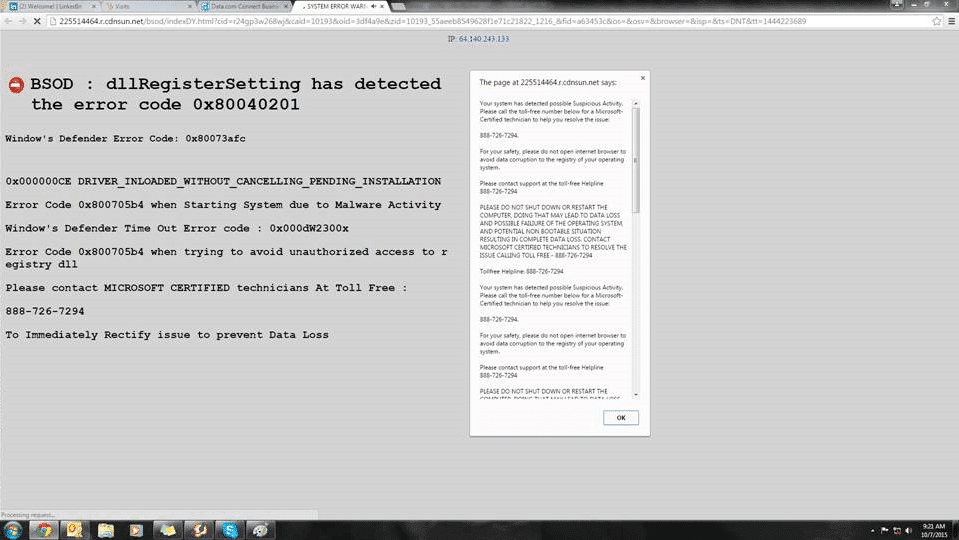
Whilst developing leads and contacts, one of our employees went to investigate a company by visiting their website, which was listed on Salesforce. Unfortunately, it had fallen victim to DNS hijacking; the site, aquafunding.com (don’t go there), redirected to a subdomain of cdnsun.net. This particular redirect tries to take control of your browser and triggers a pop-up warning that your PC has been infected. You can either click the OK button or call their toll free number to speak with Microsoft Support.
Naturally this can be alarming, but look closer: the pop-up from the cdnsun.net site says you have malware, but only lists Microsoft to seem legitimate. A quick google search on that number confirms that this is bogus.
The Resolution
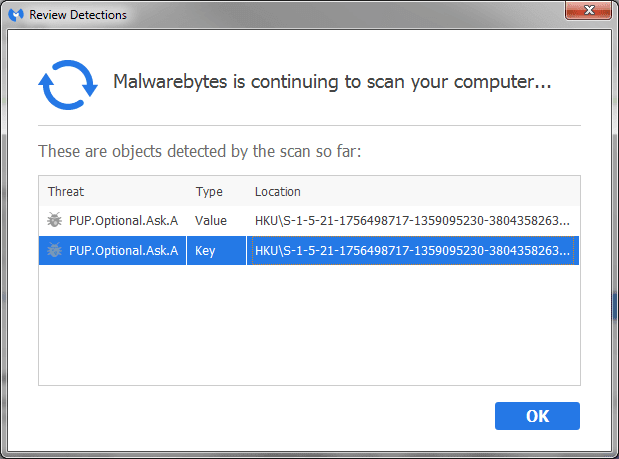
The first step to correct this was to take the infected user’s PC off the network so it couldn’t pose any further risk to the rest of our network. From another computer I downloaded a copy of Malwarebytes to detect malware on the user’s computer and installed it with a USB stick. We ran a scan on the infected machine and found something called “PUP.Optional.Ask.A.”
You can learn more about this unwanted program from this site that also discusses how to remove malware from your PC. The write-up shows how easily this is spread and how many browsers this affects with DNS hijacking:
“Once PUP.Optional.ASK.A is run on the computer, it targets mostly known browsers like Internet Explorer, Google Chrome, Mozilla Firefox, and Safari. This threat performs changes on browser settings that may result to home page hijacking and browser redirect problems. PUP.Optional.ASK.A also drops extension, add-on, and plug-in to achieve other malicious tasks.”
After removing the “PUP.Optional.Ask.A” on the machine, we reset Chrome and IE browser settings on the user’s PC and verified that no 3rd-party plugins were being used. We wanted to be sure that before we let the user back onto the network, their machine was no longer infected. The final step in the resolution was identifying the flow data in a NetFlow Analyzer like Scrutinizer in order to see the sites that the user hit to get there. You could also set up a threshold that alerts you on DNS Hijacking, so that when a user hits a subdomain of cdnsun.net on any links in the network, it reports on any connections from local users.
For a proactive means to monitor your network for suspicious activity and detecting malware, don’t hesitate to call us at Plixer or evaluate our NetFlow traffic analyzer.