Security is a top concern for most network administrators and engineers today. Those that want to detect suspicious network activity within their environment can use a NetFlow solution to gain insight into network traffic and cyber threats. I often hear, however, that they don’t have time to just stare at a screen until something goes wrong; there are too many user issues and fires that need attention. By using Scrutinizer, you can automatically receive email alerts on specific threshold breaches to help detect suspicious network activity. In this post, I’d like to explain how to detect suspicious network activity.
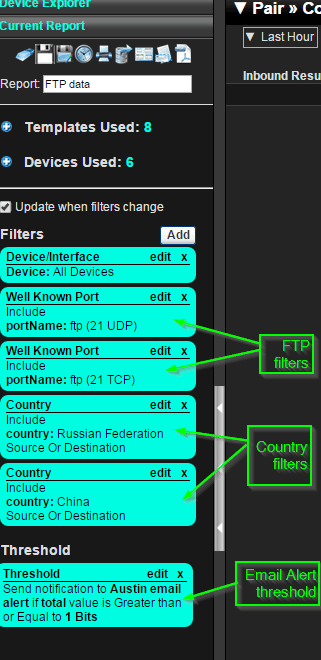
Let’s look at a scenario where we may want to have a threshold set to alert when a particular type of traffic is detected. For example, I may want to monitor connections to one of my servers that houses sensitive customer data. Ideally I would like to see if there is ever FTP traffic seen going out to a host from another country. So let’s create a report that is filtered on FTP traffic by selecting some well-known ports. Afterwards, we will add a country filter for the countries we wish to monitor.
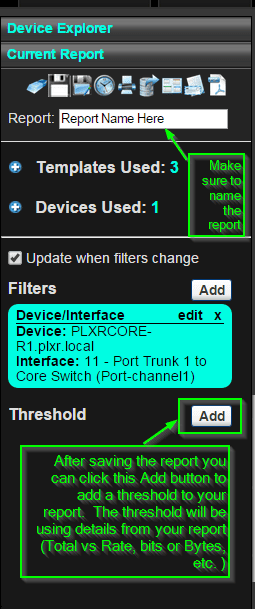
Now that we have a report in place, let’s give it a name and add a threshold with an email alert policy so that we can be proactively notified if this type of traffic is occurring.
1) Creating the Notification Profile to use
Navigate to Admin-> Definitions-> Notification Manager
Select New and type in the name of the profile this email will be used for and press Add Alert.
You will need to specify the email address to send the report to and Save Alert when you are done.
2) Adding a threshold that sends a notification
Click the Add button next to Threshold.
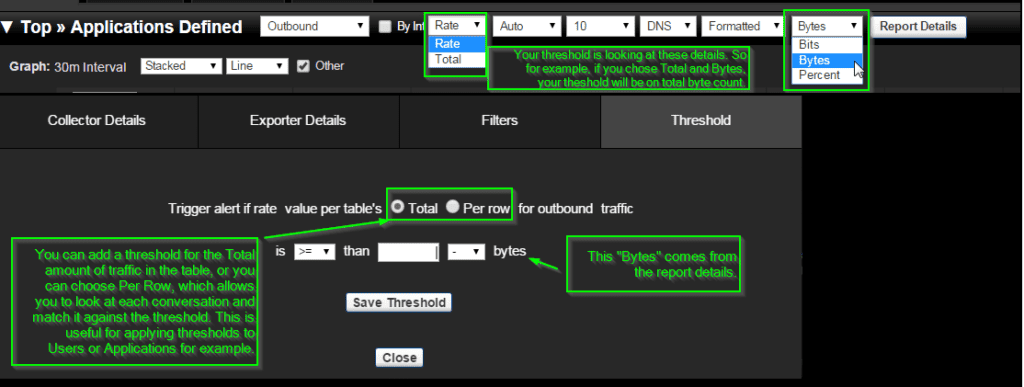
You will have a module pop up that asks you to define your threshold, again keep in mind this is using details from your report. The picture below shows the correlation between what you select and what the threshold will be using. For our scenario we will be selecting Total and Bits as well as applying the trigger alert as Per Row. This will show us any conversation that is greater than 1 bit, essentially, any traffic being generated.
Once you save the threshold it will bring up a window asking you to select a Notification Profile.
You will see NONE displayed in a drop down box, but you can select the profile we created already in Step 1; and then click Save. If you need to make a new profile, click the Manage Notifications button.
You will see the Profile was added to the Threshold and the report needs to be saved on more time
With the threshold above, anytime FTP traffic is seen you will get email alerts notifying you of the suspicious network activity.
Hopefully, for the most part, this report is blank and displays no data. If there is data in the report you will have received an email alert and can view the report in Scrutinizer for more details. Whether its detecting suspicious network activity or a targeted attack, a NetFlow solution can provide you the details needed.
If you need assistance getting this set up, call our technical support team. They will be glad to help you with your report.