I was recently speaking with a customer about network security when he brought up a nasty botnet called the DressCode Trojan. Having never heard of this, he explained to me that it was a trojan that had made it’s way on to the Google Play app store. After doing some research of my own, I found that over 400 different apps had been affected causing thousands of Android phone users to become infected. While some companies do offer malware detection apps for Android phones not everyone knows these exist plus, botnets tend to remain dormant for some time causing the end user to not even be aware that their mobile device is infected. In a world where BYOD (Bring your own device) has become popular it is important to not only monitor for botnets and other forms of malware on your network but being able to monitor mobile devices is a must. With Scrutinizer, we can combine both security needs in one tool.
So What Is The DressCode Trojan?
Back in August of this year, researchers became aware of a botnet that had made it’s way in to a number of dress up games that are usually popular with young girls earning it the name of the DressCode Trojan. Shortly after, this trojan made it’s way in to over 400 apps and almost had been downloaded over 100,000 times! That’s a lot of infected phones. You can read more about that here at Kapersky’s blog. https://blog.kaspersky.com/dresscode-android-trojan/13219/
How Does Scrutinizer Fit In?
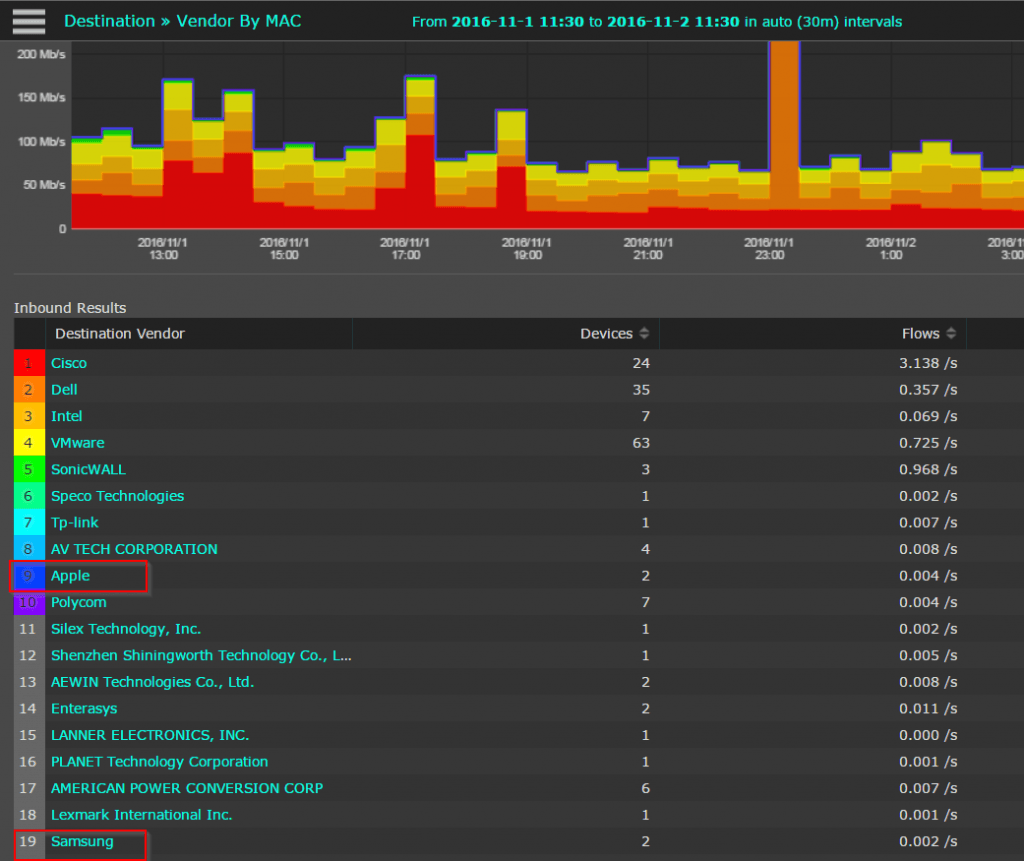
With Scrutinizer, not only can we monitor mobile devices but we can track down botnets as well using our flow analytics algorithms and our advanced reporting license. First, we can track down types of mobile devices on the network by running a destination > vendor by MAC address report. By running this report not only can we see that we have a number of Apple users on the network but we can also see Samsung.
From there, we can drill in on the users who use Andriod devices (as well as Apple), look at the traffic, and begin to find the source of the botnet so we can act to take the device offline.
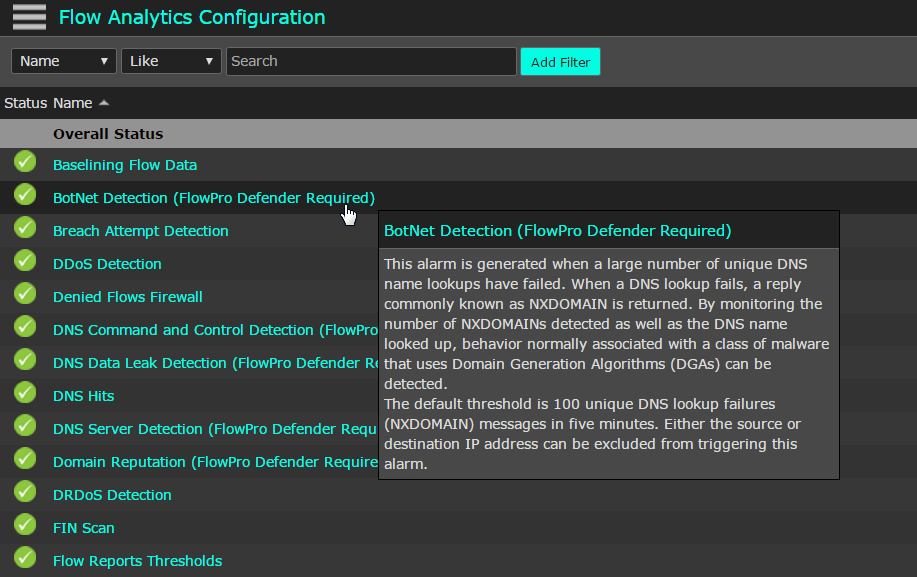
With the Flowpro Defender we can also configure out botnet detection algorithm to send alerts to the end users when the alarm is triggered. The picture below explains how our BotNet detection works.
Pretty amazing stuff!
How Can I Avoid Getting Infected?
When it comes to apps, finding out if one is legitimate or not can be tricky. The app may have thousands of downloads and hundreds of stellar reviews but it could still be bad news. Be sure to only download official apps and carefully read each review. If any app looks suspicious, do not download it. The good news is, Google has become aware of the situation and is working on removing apps that could be compromised. For more info about what apps may be comprised, take a peek at this link from zdnet http://www.zdnet.com/article/over-400-instances-of-dresscode-malware-found-on-google-play-store-say-researchers/
As always if you’d like to give Scrutinizer, advanced reporting, or the FlowPro Defender a test drive don’t hesitate to reach out to us here at Plixer. We’re always happy to help our customers keep their network safe.
Peace, love, and netflow!