How many companies out there are monitoring DNS traffic? Are you concerned about data exfiltration over DNS? How many people even know that is possible? These are questions I get to ask customers, and the response I get is the same with everyone. Not very many companies monitor their DNS traffic.
What Is DNS:
The Domain Name System (DNS) is a system designed so we as humans don’t have to remember IP addresses when browsing the internet. DNS converts web addresses like www.google.com to an IP address like 64.233.171.103. I could tell you ten web sites, and you would probably remember a large portion of them. If I gave you 10 IP addresses, most of us would have a hard time trying to remember the first one. That’s why we have DNS.
Data Exfiltration over DNS:
DNS is a system that is in every network connected to the internet. It is rarely ever monitored and even more rarely blocked. This makes data exfiltration over DNS somewhat easier than other means of data theft. This can be done a few different ways. One of the easiest, in my opinion, is with encoding data into FQDNs (Fully Qualified Domain Names) and doing nslookups on those names. Take a credit can number and convert it to a hex. Take that hex and attach it to a domain name that you control. Below is an example of an encoded string attached to my domain. As we do a lookup on that address, we are going to get back a NXDomain (Non eXistent Domain) reply from our DNS server because that domain does not exist. On the other end, at my server, we can collect that information. Strip off the ‘.ryan.is.awesome.com’ and we have data that was not detected by any security system on the target network.
1j89w6421f.di8s42311.2481f4i2c318.8z321dami84.ryan.is.awesome.com
A fully qualified domain name can be as long as 254 characters. As long as you have a separator “.” every 63 characters. This leaves quite a bit of room for encoding data into the FQDN.
Monitoring DNS Traffic:
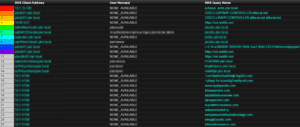
Now that we know it is possible to do data exfiltration over DNS, let’s talk about how to detect that. With a device in place like a probe that can monitor DNS traffic specifically, we can get more information about the lookups that are occurring on our network. We will want to set up a report in our NetFlow collector to show FQDNs. Below is a screen shot of a report that I have set up.
In the left hand column we will see a list of all the hosts that have received a reply of NXDomain in the time period we are looking for. It’s okay to see a few. It’s the long, complex domain names that we are concerned with. We can take this report and add a few filter to see only the hosts we care about and at a threshold that if one host has more than X amount of lookups on NXDomains to send an email to our security team for deeper analysis.
If you would like more information on monitoring your DNS traffic, feel free to reach out to us here in Plixer Support.