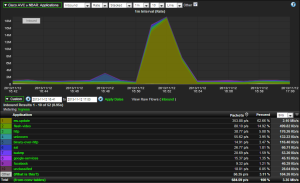
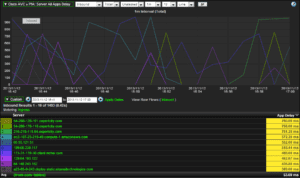
As you can probably tell from the title, Cisco AVC IPFIX support is all of the rage now. With all kinds of new elements that can be exported and measured, why wouldn’t anyone want to send this to their NetFlow monitoring tool? One thing I have noticed working in support is that the more information and visibility we have across the network the easier it is to troubleshoot issues or combat a network threat. We have already seen some of the ways that network threat detection can be mitigated using IPFIX and AVC, and this blog will cover some of the new features of Cisco AVC MACE.
Cisco AVC now supports MACE metrics (Measurement, Aggregation and Correlation Engine). MACE offers some great information about what is happening on your network. Cisco MACE reporting offers ART (Application Response Time) and tons of new collect commands for monitoring IPv6 flows. This blog will be covering the setup and configuration for exporting Cisco MACE (specifically, ART)
The ART engine saves some data from each packet and performs the necessary calculations; then aggregates the flows based on the following layer 7 information:
- Destination address
- Destination port
- Layer 4 protocol
- Segment ID
- Source address
Configuring Cisco MACE reporting on an Interface:
To configure MACE on an interface we will first need to configure a flow record to collect all of the new MACE statistics.
Router: conf t
Router(conf): flow record type mace Flow_Record
Router(Flow_Record): collect art all
Router(Flow_Record): collect application name
Router(Flow_Record): collect counter client bytes
Router(Flow_Record):collect counter server bytes
Router(Flow_Record): collect counter client packets
Router(Flow_Record): collect application http host
Router(Flow_Record): collect application http url statistics
Router(Flow_Record): collect policy qos classification hierarchy
Router(Flow_Record): collect policy qos queue drops
Router(Flow_Record): collect time inter-packet-gap histogram
Router(Flow_Record): collect time inter-packet-gap
After the flow record has been created we need to create a flow exporter:
Router(conf): flow exporter Flow_Exporter
Router(Flow_Exporter): export-protocol ipfix
Router(Flow_Exporter): option application-attributes
Router(Flow_Exporter): option sub-application-table
Router(Flow_Exporter): option class-qos-table
Router(Flow_Exporter): option policy-qos-table
Router(Flow_Exporter): destination Ip-address (Netflow Collector server)
Next we need to configure the flow monitor to use our flow record and flow exporter that we just created:
Router(Conf): flow monitor type mace Mace_Monitor
Router(Mace_Mon): record Flow_Record
Router(Mace_Mon): exporter Flow_Exporter
Configure a class map name:
Router(conf): class-map type waas Class_Map_Mace
Configure a policy map and class name:
Router(conf): policy-map type mace Policy_Mace
Router(policy): class Class_Map_Mace
Router(policy): flow monitor Mace_Monitor
Exit
Exit
Router(conf): interface type-number [name-tag]
Router(int): mace enable
End
And there you have it, you now have MACE enabled on an interface and can start doing some Cisco MACE reporting in your NetFlow analysis tool. For more information on this configuration and a complete list of all of the different Cisco AVC MACE exports, see this Cisco document on configuring Cisco AVC MACE reporting. If you need any help in configuring your device to export Cisco AVC MACE metrics or need any other support please feel free to let us know!