Did you know that using an advanced network reporting solution you can log NAT and firewall events from a Cisco ASR router to a flow collector, and report on this data using NetFlow v9?
Did you know that using an advanced network reporting solution you can log NAT and firewall events from a Cisco ASR router to a flow collector, and report on this data using NetFlow v9?
I’ve been working with a service provider that deploys ASR1006 routers at his ISP’s internet Edge. They use private IP addressing which is NATed at the internet edge network. This allows scaling of IP addressing such that if they ever have more subscribers than available public IP address space they are not limited. The problem that this presents is that his country has regulations where government authorities ask that ISPs identify a subscriber based on IP address and time provided by authorities to the ISP. So he needed some reporting that would provide this visibility.
He first figured that he would enable NAT translation logging via syslog. If ever a government authority asks to identify a customer by IP address, Network Operations could look up the public to private mapping on the syslog server by looking at the logs to identify a subscriber based on that private IP address.
This worked OK for a while, but being that this is an ISP environment and traffic demands increase a lot, the ASR could no longer handle subscriber traffic, and this quickly caused the ASR’s CPU utilization to go through the roof.
He consulted Cisco and found that using ‘ip nat trans syslog’ is not recommended as the speed of NAT setup/teardowns can easily overwhelm the ASR and can cause crashes.
Cisco said that the recommended way to log with an ASR1k NAT is via v9 NetFlow.
Enabling NAT Event logger is pretty easy and requires just one command. But it’s good to tune up timers such as how often the template is going to be sent to collector.
ip nat log translations flow-export v9 udp destination [collector IP address] 2055
To enable firewall event logger the following configuration is required
parameter-map type inspect global
log flow-export v9 udp destination [collector IP address] 2055
log flow-export template timeout-rate 1
My customer was familiar with the NetFlow reporting function as it related to network traffic monitoring and was excited to learn that he could take advantage of the flow technology to get the NAT Report visibility he was looking for. He had heard of event logging with NetFlow v9 on Cisco ASA platforms, they call it NetFlow NSEL “Network Security Event Logging”. So he figured, “ok no problem, I just have to find an NSEL compliant NetFlow collector”.
He quickly realized a new problem, NSEL compatible NetFlow collectors are mostly useless with ASR NAT logging. The ASR NetFlow NAT logging, which is called “NEL” (NetFlow Event Logging), has a different flow template than the ones used by NSEL on ASA.
There is a very limited number of NetFlow Collectors that support NEL. Cisco’s NetFlow Collector 6.0 supports ASR1K NEL, but even it has to be customized to support the NEL flow template.
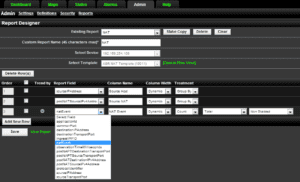
Our advanced reporting engine offers a Report Designer, which lets the user create his own reports using any field present in the flow templates exported by a device.
We were able to easily select the fields that he needed from the NEL templates to create reports that comply with the regulations the authorities were looking for.
So, what kind of reporting needs do you have? Do you need a NetFlow collector that supports NAT Logging NetFlow exports from a Cisco ASR?