Bosses can get bored at work just like everyone else and it often happens at the same time you or I are getting bored. Take Friday afternoon after lunch for example. The boss is back from a big sandwich lunch where he/she ate a bit too much, their belly is full and because of that they are fighting the urge to be lethargic. The thought of reading email or reviewing another document is a task they just can’t seem to muster up the motivation to review.
What can they work on that would be interesting and justifiably constructive to the company? They skim their email hoping to find something, they look at the phone which isn’t blinking with new voice mails, they look around their work area and they think, I’ll go talk with employees and check in on things. Second guessing this initiative reminds him/her that talking with their constituents will interrupt or possibly delay the important tasks that have been assigned to them. Besides, maybe they’ve already done this twice this week. What else can they do to avoid the grind but, still feel like they are benefiting the company?
Bosses Don’t Spy Do They?
Most bosses are decent politicians and would never call checking in on an employee unbeknownst as ‘spying’. Although, that is essentially what it is. But how do they do it and what are they looking for? A big question mark in their head is what you do during the day on your computer. You might think that they can’t see the web sites you visit, the traffic you create or the frequency of your connections but, they most certainly can and in many cases it’s easy for them to do.
Your Computer Traffic is being Saved
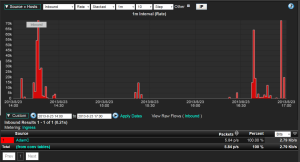
The wired or wireless connections from your computers and handheld devices often connect to the corporate network. You might think of your connections to Facebook, eHarmony, Linkedin, Skype or other social media sites as being private but, if the traffic is cruising over the corporate network, it’s most certainly the company’s legal right to investigate it. IT guys really hate bandwidth abuse because when people complain about the performance of their Internet connections, the IT team goes under fire and they’re tired of it. Big networking companies like Cisco, Dell and Extreme are aware of this and have empowered network administrators with software upgrades to the routers and firewalls your traffic travels over to export flow technologies known as NetFlow or IPFIX. These protocols allow the routers to export summarized details about EVERY connection you make albeit from your laptop or your smart phone. The flow export from the routers and firewalls is sent to a flow collector which is usually capable of archiving details about your traffic for weeks and sometimes up to a year or more.
Your traffic details aren’t captured purely for snooping purposes. First and foremost the traffic is archived for industry compliance regulations and for forensic investigations should an electronic threat or theft take place. NetFlow and IPFIX in most cases provide enough detail to be very thorough. Details can include your computers IP address, the destination address, the application and several other details such as the amount of bytes you’ve transmitted or received. As of late, many vendors like Cisco, Dell and nBox are exporting HTTP Host, URLs and even username.
IT Empowers Bosses with Snooping Tools
Since IT has a limited budget and they can’t keep asking the powers that be for more bandwidth, they need to clean up the expensive Internet connections and remove unnecessary noise. The noise is typically excessive traffic to sites like Facebook or YouTube. Like many individuals, IT doesn’t want to be the bad guys but, they have a job to do just like you and me. For this reason, in some organizations they are empowering managers to help clean up traffic on the Internet connections by granting them access to the flow data.
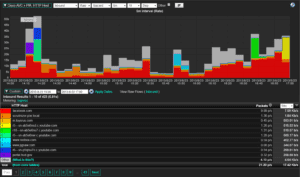
Managers can now launch a browser, select a favorite URL and voila, here’s the traffic created by their team.
Now if you are thinking that your boss is too numb to use a tool like the one shown above, don’t under estimate the foresight of your corporate IT team. They realize these tools can appear cryptic. Due to the pressure they are receiving from their management, they are often more than happy to provide one-on-one training sessions to the internal folks that are interested in seeing the network abuse that goes on every day. They can even save these reports ensuring that seemingly ignorant bosses can easily reference these reports in the future.
Bored Bosses Check Up on Employees
Within one or two clicks and perhaps a single filter, they can zoom in to find out who’s visiting Facebook or YouTube. A quick screen capture or export to PDF and off an email goes to you or even worse: HR. You’ve been BUSTED!
Don’t underestimate upper management. Often times there’s an IT guy taking heat for a poorly performing network connection who can make your boss look very much on-the-ball.
Find out for yourself. Call and ask for a demonstration or download a copy of our white paper that was co-authored by Cisco Systems: Flow Based Approaches in Network Management.