DNS tunneling, is the ability to encode the data of other programs or protocols in DNS queries and responses.
The concept of DNS tunneling was originally designed as a simple way to bypass the captive portals at the network edge. But as with many things on the Web, it is often used for nefarious purposes. Data payload can be added to an organization’s DNS and used as a method of command and control and/or data exfiltration.
While the methods of delivery typically require the compromised client to have external connectivity, interestingly, the compromised machine doesn’t need actual external connectivity. The machine simply requires access to an internal DNS server with external access, which will enable the machine to send and receive DNS responses.
In addition to compromising the target organization, the attacker must also control a domain and a server that can act as an authoritative server for that domain in order to run the server-side tunneling and decoding programs.
Hackers use a variety of DNS tunneling utilities as well as several known malwares that use DNS as their communication channel. While each utility varies on the specifics of how they work, they all transmit the data encoded in the payload. Hackers also use a wide variety of DNS record types, all of which can be combined with EDNS (Extension Mechanisms for DNS) to increase the payload. TXT records are the most common because they offer the largest and most diverse payload structure.
For many organizations, DNS tunneling isn’t even a known suspect and therefore a significant security risk. When they think of DNS security, there is a tendency to overlook the security of critical data or systems being compromised by covert outbound DNS inside their networks. But over the past several years there have been a number of large-scale security breaches using DNS tunneling, affecting millions of accounts.
How can it be used in a network breach?
Because DNS is rarely monitored and analyzed, hackers are able to use DNS tunneling to slip under the radar until something else draws attention to the breach.
Here is the usual sequence of activities:
- A client sends a request for a particular host name in a domain, with the data/response to the server encoded in the hostname being requested.
- The server responds with its data in the RDATA field of the response. Because DNS allows hostnames of up to 255 characters, with each label (subdomain) limited to 63 characters, DNS allows the client to use lengthy individual labels as well as multiple levels of subdomains to encode their data.
For example:
The client sends a query for an A record where the data is encoded in the host name:
MRZGS3TLEBWW64TFEBXXMYLMORUW4ZI.t.example.com
Then the server could respond with an answer as a CNAME response:
WW2IDPOZQWY5DJNZSQ.t.example.com
- The client now has two-way transactional communications to a compromised network. The attacker can transfer files out of the network or have complete remote access to the compromised system.
How do you gain visibility into the DNS traffic?
The answer is simple – NetFlow. In particular our FlowPro Defender NetFlow probe.
I work with customers everyday who are looking to gain insight into what kind of traffic moves across, and in and out of their networks. NetFlow lets you use assets that you already have to see who, what, when, how much, and how often traffic traverses the network. We talk all of the time about how this visibility allows security administrators to see and analyze all of the conversations traversing the network.
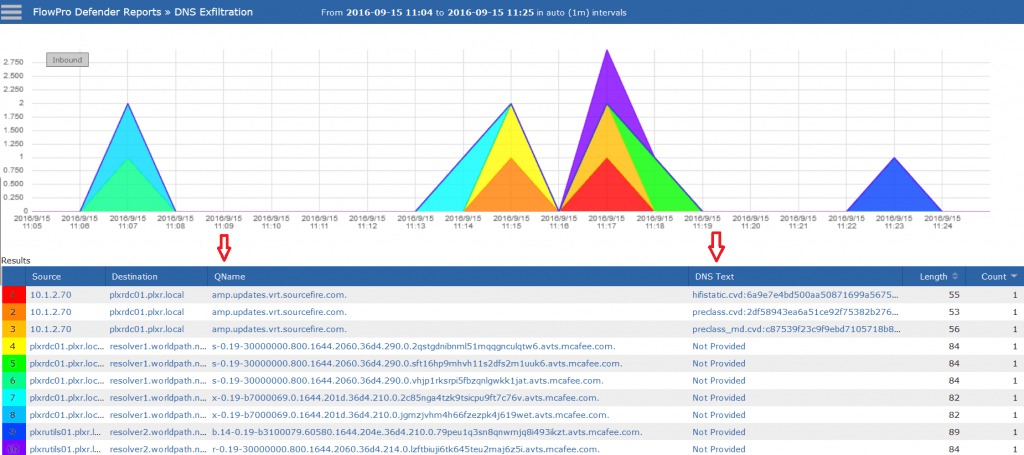
Now apply that same monitoring process to DNS. The probe ingests traffic streams and can be set to focus and export detailed DNS information via NetFlow. Detecting data exfiltration using NetFlow gives you direct insight, and immediate alarming when irregular DNS requests and responses are seen moving in and out of the network.
Notice in this report we are able to see inside the contents of the DNS records and alarm on strange content or text seen in the FQDN’s. We can also alarm on existence of this type of traffic.
We can also alert on many types of domain reputation and high numbers of requests for non-existent domains.
Are you aware of what kind of traffic might be moving in and out of your network using DNS?
Using NetFlow and our FlowPro Defender we can help you reinforce your defenses against bots that are trying to exfiltrate your corporate assets using DNS tunnels.