I was attending the 12th annual NC InfoSeCon conference back in October and in one of the presentations, the speaker mentioned Dark DDoS attacks. I found this part of the talk unbelievably interesting. Combine that with the recent fuel shortage here in NC and my mind started wandering with concerns over global digital terrorism and its part in the upcoming zombie apocalypse! Ok, maybe not to that degree, but I did decide to dig deeper into the methodologies behind these types of attacks.
What is a DDoS Attack?
First, I needed to review what a DDoS was. Basically, DDoS is an acronym for Distributed Denial of Service. It’s a type of Denial of Service (DoS) attack where multiple compromised systems, often infected with a Trojan, are used to target a single system, causing a Denial of Service (DoS) attack.
In the past, the most common method for a DDoS attack was to target HTTP POSTs or GETs, but in today’s world, we are starting to see a growing number of attacks targeting DNS and VoIP services. The methods attackers use may differ, but the goal remains the same: deny the use of the network asset for its intended purpose.
What is a Dark DDoS Attack?
So why is this a concern? Wouldn’t end point protection stop this?
If the motives for the attack were to simply bring down the system, then there is a good chance that the local equipment isn’t going to be as effective as one would hope. During an attack, working with your service provider is going to be the best bet, since they have the ability to apply rate limiting quickly.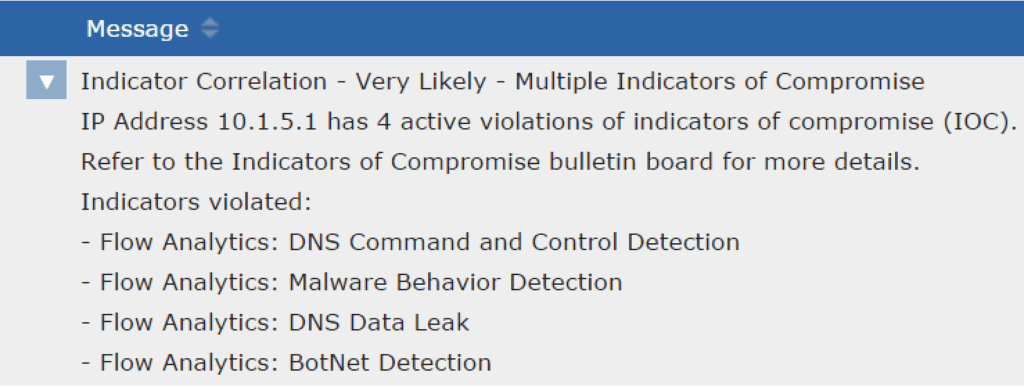
The good news is that you do have some options on the home front, like Palo Alto’s Vulnerability Protection and SonicWALL’s mitigation technology. As I started digging, I learned that detection methods like these are designed to help prevent an attack by matching various known attack profiles and signatures. This got me thinking, what about the unknown issues? What if the motive isn’t what we think it is?
As I mentioned before, it was easier to identify the purpose of larger-scale attacks, but in recent months, we’ve seen a different style of attacks with different intentions. Now hackers are applying shorter and smaller attacks in combination with other passive reconnaissance methods before launching a flood on the network.
As a matter of fact, the vast majority of DDoS attacks we see today are smaller in scale and are only 30 minutes or less in duration. In general, their motive is to search a network for vulnerabilities and find pathways to steal sensitive data. In the end, stealing that data—AKA data exfiltration—is the goal, NOT to deny the use of the targeted network asset. This is a concern because this tactic evades many of the DDoS scrubbing center legacy solutions that are deployed today.
For example, the attacker can fill logging systems with massive amounts of DDoS-related traffic and mask that one event that pertained to the breach in the first place. This obviously causes huge problems in trying to halt a breach and identifying data exfiltration, as well as making attack forensics and the post-breach cleanup all the more difficult.
In a large proportion of data breaches reported over the last few years, DDoS attacks have been occurring simultaneously, as a component of a wider strategy; meaning hackers are utilizing this technique in a significant way. – Dave Larson, COO/CTO, Corero Network Security
Is there help?
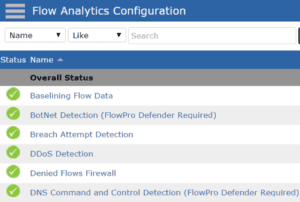 As you guessed, hackers are smart and organized. To deal with threats like this, you need to employ multiple levels of protection that allow you to monitor for the various attacks methods. Applying an internal monitoring system like Scrutinizer can help you gain the visibility and intelligence needed to see something like the two-pronged approach of a Dark DDoS attack. Here are the questions to ask when evaluating an incident response tool:
As you guessed, hackers are smart and organized. To deal with threats like this, you need to employ multiple levels of protection that allow you to monitor for the various attacks methods. Applying an internal monitoring system like Scrutinizer can help you gain the visibility and intelligence needed to see something like the two-pronged approach of a Dark DDoS attack. Here are the questions to ask when evaluating an incident response tool:
- Does your flow monitoring tool have the ability to monitor for DDoS patterns at any level?
- Can it monitor for Data Exfiltration by injecting Fully Qualified Domain Names and applying threat intelligence?
- Does it have an Indicator Correlation engine to help align multiple Indicators of Compromise and escalate them as a security event?
- Can it identify one-on-one conversations and identify the end user?
- Can it store that data for later analysis?
If you’re interested in learning more about monitoring for a Dark DDoS attack, contact us for a demo and evaluation of Scrutinizer.


