One of last year’s biggest threats is rearing its ugly head again in the form of a WannaCry phishing email scam. Early on June 21st, many people in the UK received an email informing them that the sender had infected their system with WannaCry. The senders threatened to encrypt all the recipient’s data if they didn’t pay a ransom of 0.1 Bitcoin ($650). The thing is, they haven’t actually infected anything at all.
The WannaCry Phishing Email and Its Variations
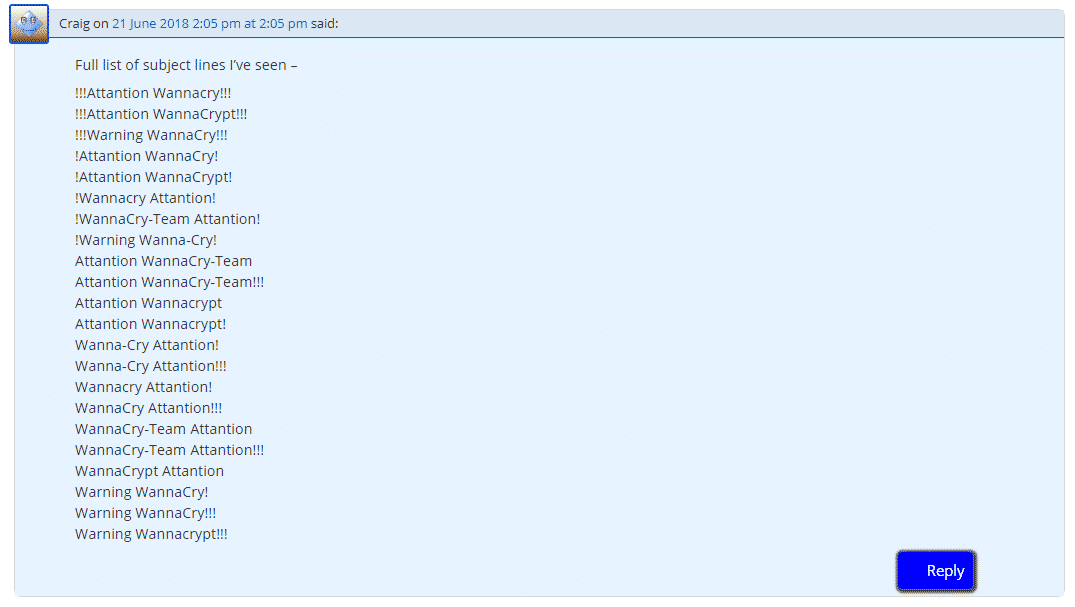
Here is what the WannaCry phishing email generally looks like:
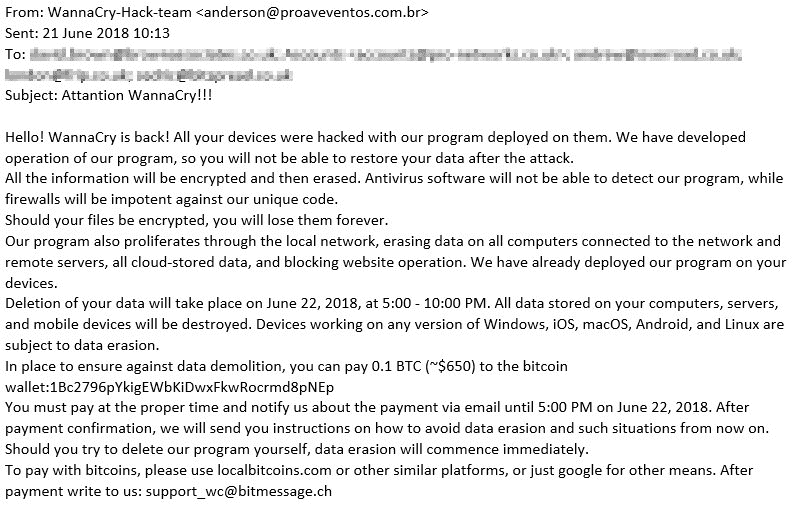
It’s like a typical ransomware threat. They say their program is on your devices and threaten to delete your files if you don’t pay the ransom. There are many variations of the body copy, the sender address, and the subject line. On the website My Online Security, one user listed 22 different subject lines he’d seen.
As Always, Stay Calm
While most scams infect you and then try to get money, or attempt to impersonate a legitimate organization, this one does neither. Instead, it purposefully looks sketchy and falsely claims to have infected you. It also says that antivirus won’t detect the infection—indeed, as there is none to detect.
Luckily, it seems that nobody’s falling for this scam. As of midnight UTC today, the Bitcoin blockchain indicated that nobody had sent any funds to the specified address.
Furthermore, Action Fraud UK received over 200 reports about the emails as of yesterday morning.
Alert: Don’t pay this fake #WannaCry ransom demand! We’ve had over 200 reports today about these extortion emails which claim to have infected people with the WannaCry virus! ???? #TakeFive and #Tell2 pic.twitter.com/aHZEh3UXTF
— Action Fraud (@actionfrauduk) June 21, 2018
My optimistic side believes that people are now more aware about phishing scams. But perhaps this particular scam just isn’t clever enough. Maybe whoever is behind it just wants and expects only one person out of a thousand to pay the “ransom.”
How to Prepare for Things to Come
The one part of the email that retains my interest, as mentioned above, is that they tell you antivirus and firewalls won’t detect the program.
While that’s just a bluff in this case, there certainly are threats that can move undetected into and through your network. In those situations, your best protection is to be able to recognize the symptoms or behavior of different threats.
In the case of WannaCry last year, we wrote on how to determine whether your devices had been exploited based on traffic patterns:
- Use Scrutinizer to run long-term historical reports identifying traffic patterns and the legitimate servers that normally send and receive network traffic using TCP port 445.
- This provides a baseline of allowed port 445 traffic.
- Armed with this data, you can quickly create ACLs on routers/switches to lock down P2P use of 445, and limit it to valid traffic without disrupting business ops.
- Generate a report identifying the list of IP addresses (servers) allowed to use port 445.
- Set an alert for any 445 traffic originating from any disallowed devices on the networks.
- Gather and monitor historical DNS traffic historically (check DNS logs) looking for devices that have reached out to the kill switch domain.
- Set alarms to alert if any new devices reach out to the kill switch domain.
- Immediately quarantine any devices that begin sending unallowed 445 traffic via ACLs and/or reach out to the kill switch domain.
With the WannaCry phishing scam, of course, there would not be any deviations from your normal traffic patterns.
But in many organizations, the security and network teams work separately. Therefore, the traffic data that’s useful for these situations may not be accessible to the security team. We strongly recommend that security and network teams work closely together, and have access to all the same information.
We find that too often, the network team is the one with the needed data, but it’s a different role that would use that data to respond to security events.
If you’re interested in a network traffic analysis platform designed for use by both the security and network teams, check out the free edition of our solution, Scrutinizer.