To detect a phishing scam, we typically examine hyperlinks for odd domains or subtle character changes (like a “1” in place of an “I”). But suppose a bad link looked completely normal, or perfectly mimicked one you often visit? The traditional detection methods no longer apply. This is possible with Unicode domain phishing attacks.
Can you spot the difference?
If you live in a western country, most likely you visit domains made up of characters from the Latin alphabet. But it is also possible to create a domain that uses a mix of Latin and non-Latin characters. Because there are many lookalike characters between different alphabets, it’s nearly impossible to determine a fake domain on appearance alone. Hackers can take advantage of this to execute a Unicode domain phishing attack, also referred to as an internationalized domain name (IDN) homograph attack. For example, consider the following URL:
https://www.са.com/
It looks like the domain for CA Technologies’s website, but it was actually created by Alex Holden of Hold Security, Inc. using Cyrillic characters. Note that Holden was also able to register a valid SSL encryption certificate, adding to the alleged legitimacy of the domain.
The “ca” in the domain is made up of the Ukrainian letter for “s,” which is represented by the character “c” in Russian and Ukrainian, as well as the Ukrainian letter “a.” The difference is the characters’ Unicode value. There are over 136,000 Unicode characters representing 139 scripts—finding lookalikes for fake domains is an easy task.
Farsight Security selected and observed 125 top “phish-worthy” domains over a period of 3 months. Below is just a sampling of the 116,113 homographs they found:
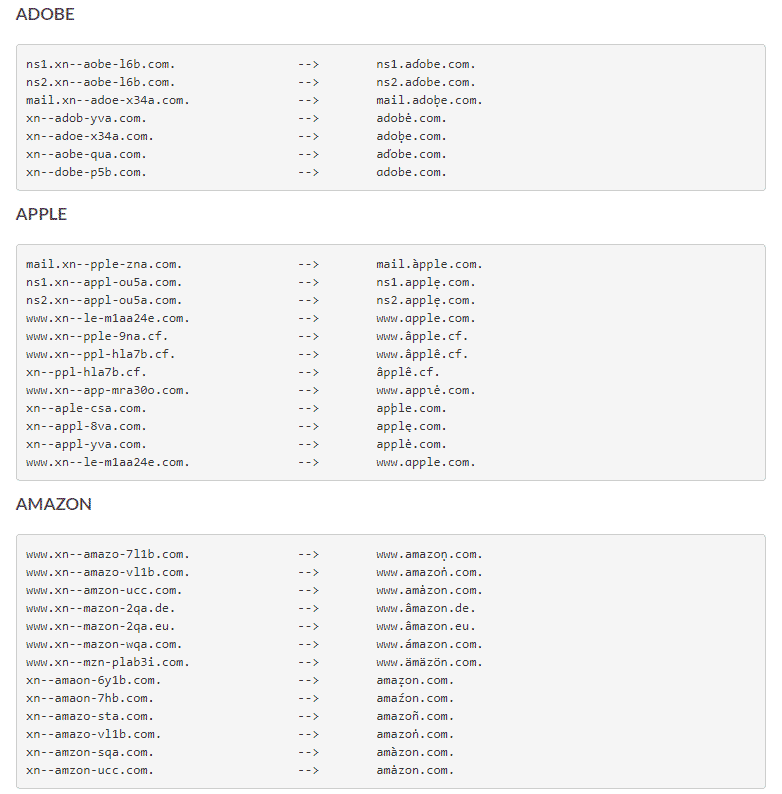
Look for Punycode to avoid Unicode domain phishing
Luckily, most browsers can warn you about these URLs and display them in Punycode. Punycode is a way of converting Unicode to the limited ASCII character subset used for internet host names. Punycode-encoded IDNs begin with the prefix “xn--“ to indicate the start of a Punycode-encoded label.
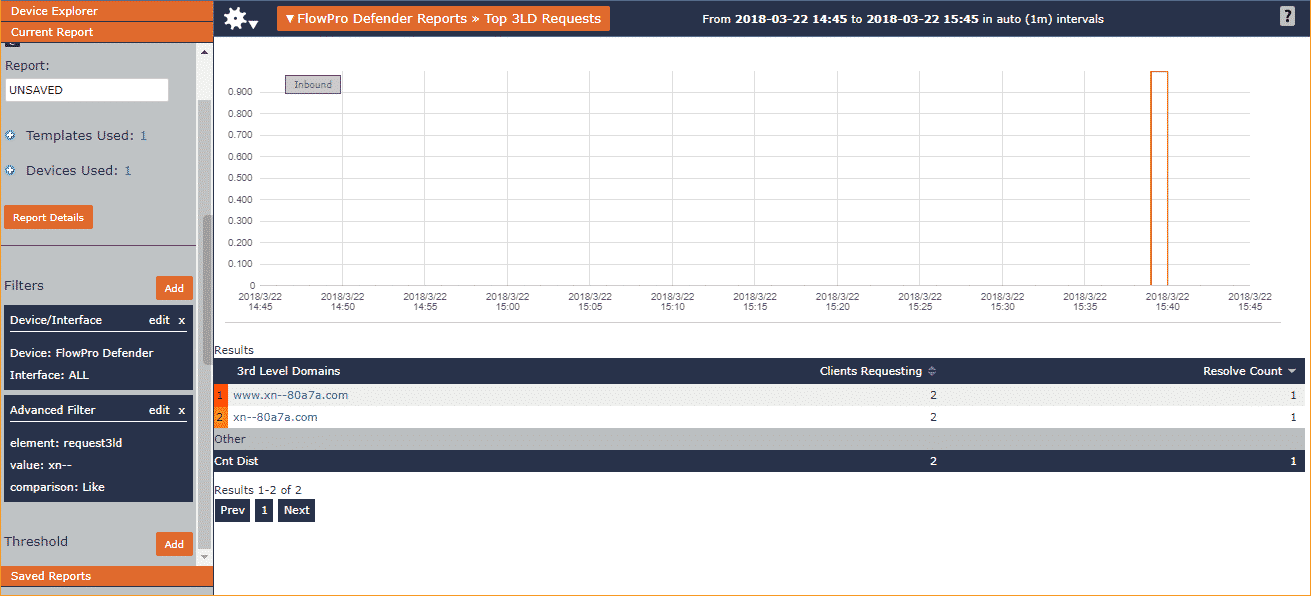
When I tested this in Chrome, for example, I could see by hovering over the above domain that it was actually going to https://www.xn--80a7a.com/. This is also displayed in the address bar on the page, although by then you’ve already visited the potentially malicious site.
Firefox, however, doesn’t always display Punycode, instead using an algorithm to decide which IDNs to display. Still, you can change the settings to always render IDNs in Punycode. Type “about:config” into the address bar, then use the search bar to look up “punycode.” Double-click the entry “network.IDN_show_punycode” to change it from “false” to “true.”
What’s great is that the actual DNS request that leaves your PC is the Punycode version of the IDN. Since Punycode always begins with “xn--,” we were able to use our FlowPro Defender to filter on domains like “xn--.” From there, we set up a threshold so that an alarm will be triggered if anyone on our network accesses an IDN in the future. This way we can stay on top of Unicode domain phishing attempts.
IDNs in other applications
Email clients and web services also handle lookalike IDNs differently. Some are more vulnerable than others; for example, Twitter will show the lookalike domain without any added context. When I tested it in Skype, though, it asked me which program I wanted to run the file—at the very least it’s a noticeable red flag. Outlook, like Chrome, displayed the Punycode.
There are also several browser extensions that can warn you when you visit a website with an IDN. Security analyst Graham Cluley recommends IDN Safe, which blocks the webpage entirely. It also has a whitelist feature if you know certain sites are legitimate.
As always, be especially wary of emails and other messages that try to provoke an urgent, immediate reaction from you.
To learn about other phishing methods you should be aware of, check out some of our other blogs: