Almost every organization is equipped with VPNs to support a remote workforce these days. Often, secure VPNs use a no-split secure tunnel, tunneling all remote workstation traffic through the security control the business has supplied. A less secure VPN option is a split-tunnel. With this method, non-business traffic routes normally within the remote network, but often with less security.
Businesses need to make a decision about bandwidth consumption and security as it relates to VPN. Capacity planning for remote users is often controlled, and during a crisis there isn’t a conscious decision to lower security’s priority, but sometimes providing access to remote users takes precedent.
At Plixer we push all remote VPN traffic through the business network to reduce the security risk. This allows us to identify and remote threats. For instance, we had a contractor “Shrek” who needed remote VPN access to our network. Our security team realized that he may not be taking all the steps necessary to ensure that his computer stays virus- and malware-free. So we applied a few different tactics to try and ensure VPN malware protection.
Threat detection system
The newest strategy we implemented is our own malware behavior detection solution called FlowPro Defender. This threat detection system monitors all of the traffic to and from the DNS and provides two main features:
- Uncovers DGAs, botnets, and other forms of malware that rely on the DNS to carry out their dirty deeds. Monitoring is done using various methods, such as:
- Counts NXDOMAIN
- Monitors for DNS TXT messages
- Compares requests to a constantly updated domain reputation list
- Uses proprietary logic to scrutinize the format of the Fully Qualified Domain Name (FQDN) requested
- Creates a cache of all FQDN lookups and sends the records to the NetFlow and IPFIX collector
Here’s the bad news: our contractor’s computer became infected at his office and then he VPN’d into our network. As soon as the computer entered our network, the active malware started sending strange requests to our DNS server. FlowPro Defender detected it immediately and sent a message to Scrutinizer.
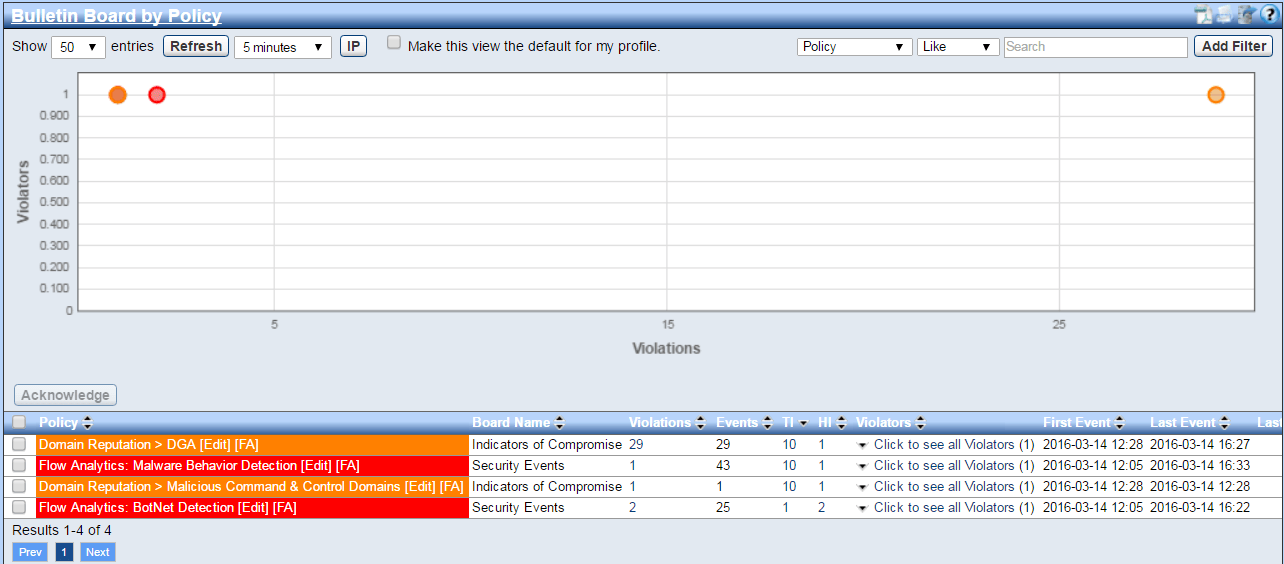
The good news is that after notification, we immediately terminated his VPN connection. We then investigated the event and learned that Shrek’s computer violated the 4 algorithms shown above. Each time Shrek’s computer created suspicious traffic, it triggered an event. As a result, his machine’s Threat Index (TI) went up. Below you can see the TI value rose to 312:
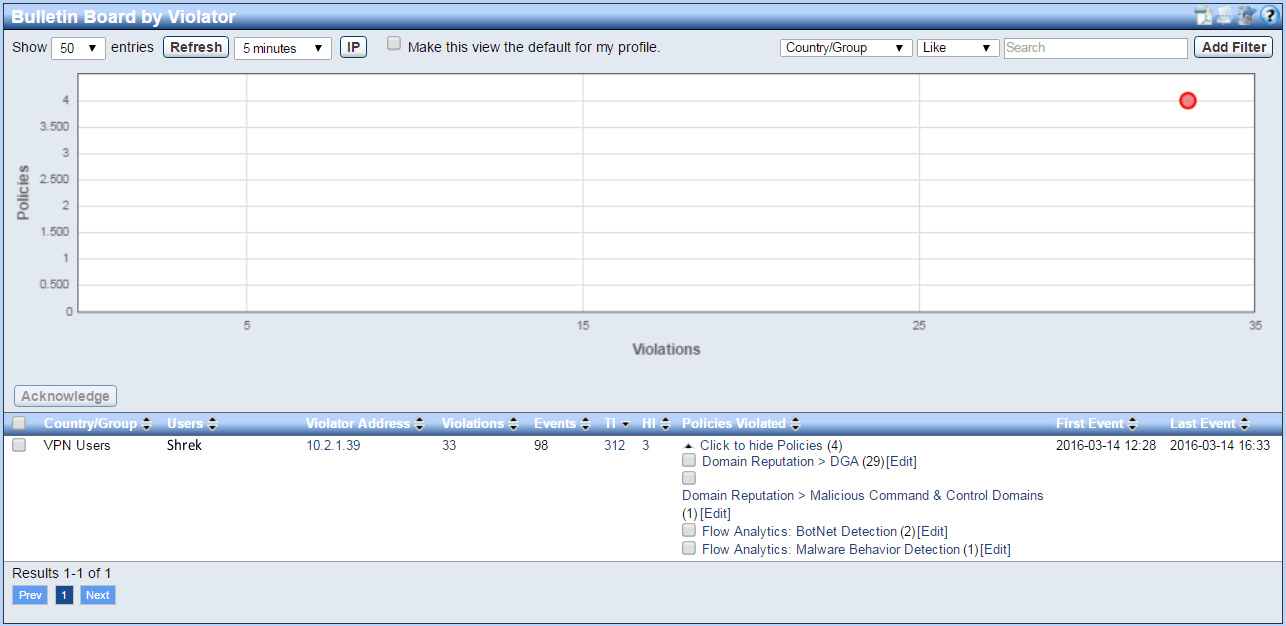
The TI is Plixer’s unique method of compiling events into a single metric for each host. If the TI hits a definable threshold before the events age out, a second notification will be triggered.
Thankfully, the firewall also picked up on the events and the flows were denied, as shown below:
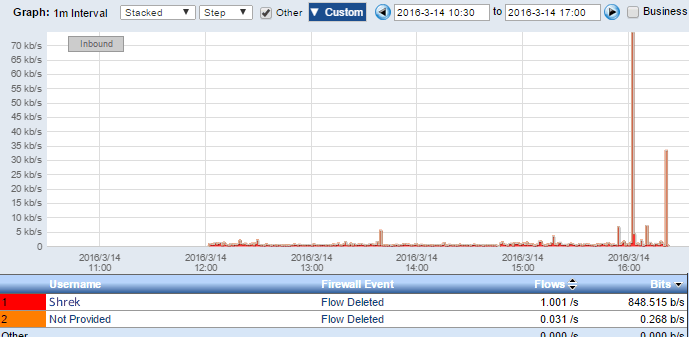
Since Scrutinizer integrates with Cisco ISE and Microsoft Active Directory, the usernames responsible for authenticating devices onto the network are displayed. A good security analytics system incorporates information from 3rd-party solutions in order to provide the best contextual details surrounding an incident. Our integration with Cisco ISE also allowed us to automatically mitigate the event by blocking Shrek’s computer.
After reviewing the time stamps on the above trend, we contacted Shrek to verify that he authenticated between 12pm and 4:30pm.
Malware behavior detection
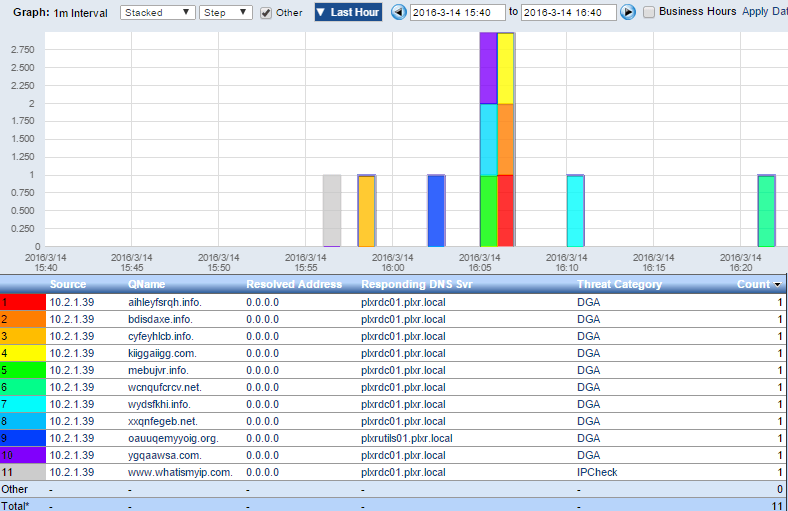
We also learned that during Shrek’s VPN session, his workstation made the following DNS requests against our DNS server, further confirming that his workstation was compromised:
- His machine performed an IP lookup to determine its internet IP address
- A Domain Generating Algorithm (DGA) was launched, which requested domains that do not exist
- One request was made to a domain that has a reputation of being malicious: miaggi[dot]com
The miaggi domain is associated with the Pykspa virus, which is a worm that spreads via Skype.
If you liked what you read about FlowPro Defender so far, you should continue reading this blog on context security awareness to learn more about FlowPro’s value to forensic investigations of not only malware but, encrypted applications as well.
Give us a call and we’ll get you started today with an evaluation.

