Seeing how much traffic is going over an interface is an integral part of every network professional’s daily routine. This information can be used for everything from future planning to trouble-shooting. That’s why understanding NetFlow traffic volume and knowing exactly how much bandwidth is being used at any given time is critical.
In our support room we often get calls asking the question, ”why is my SNMP tool showing a different amount of traffic than my NetFlow collector?”
To get to the bottom of this question, we have to look at how SNMP and NetFlow look at traffic coming across the wire.
SNMP looks at information traveling down a wire and across an interface; it marks each bit as it passes using a counter. This gives you a real time account of everything coming across the interface you are monitoring.
A NetFlow Collector is going to look at a cache of flows, i.e. conversations that occurred during a 60 second interval. A flow may consist of one or thousands of packets, depending on how long a conversation was. This flow data is based off a standard tuple that will give you source IP address, destination IP address, source port number, destination port number, protocol type, type of services, and the router input interface. If your device supports Flexible NetFlow or IPFIX you will be able to export non key fields such as usernames, client/network/server delay and URLS.
If the data being sent to the flow collector is missing key fields or if a protocol is being excluded, you will start seeing a difference between what your flow collector shows and what your SNMP tool shows for traffic volume.
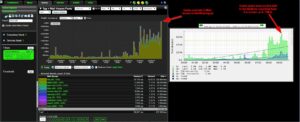
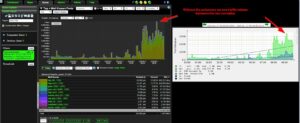
The above example shows a common difference between the two tools. When comparing the two side by side you can see that clearly the NetFlow tool is understating when compared to the SNMP tool.
Why is this? A question for the user to ask themselves is. Do I have Generic Routing Encapsulation (GRE) traffic, IPIP, ENCAP or any encrypted data going over the exporter in question? If so, there is a good chance that your NetFlow collector is purposely excluding that encrypted traffic. It does this in case the user has an encrypted tunnel whose termination point is the exporter. If the tunnel’s termination point is that exporter, then a user is going to see both the traffic within the tunnel and the traffic after it has been decrypted. This would cause the NetFlow collector to overstate traffic by duplicating the flow data.
If this is the case then the user can simply remove those exclusions on the NetFlow collector and they would see network traffic similar to what the SNMP tool is reporting.
NetFlow and SNMP are two technologies that are incredibly useful to network professionals, but with the need for Greater Security and Better Visibility increasing daily. People are demanding the ability to see more than just how much data went across a device. They want the Who, What, When and Where so that they can uncover the unwanted and proactively secure their network.
To learn more about NetFlow and how to take full control of your network with this exciting technology, sign up today for a Network Response Training class near you