Let’s talk about UDP scans and how they can be an internet threat. In today’s world, having multiple layers of Internet Threat Defense is a requirement. With Scrutinizer and the intelligence behind Flow Analytics it is easy to detect reconnaissance-style traffic patterns like UDP scans. UDP scanning is common both on the Internet and internally. A common use on the Internet is to ID servers that can be used for DrDoS (distributed reflection denial of service) attacks, as DoS works much better on UDP. Internally, it can be used to ID open ports on machines.
What is a UDP Scan?
As we all know, TCP is a connection-oriented protocol that establishes a connection to the remote host via a 3-way handshake, kinda like a formal introduction. UDP, on the other hand, is a connection-less protocol and less formal.
In this sense, a UDP connection is a meaningless term since a client can send packets to a UDP service without first establishing a connection. This means UDP is more difficult to probe than TCP. Basically, you can throw out a bunch of packets and hope something sticks or in this case, what is returned.
However, if a UDP packet is sent to a port that is not open, the system will respond with an ICMP port unreachable message. Most UDP port scanners use this scanning method, and use the absence of a response to infer that a port is open. – Wikipedia
The down and dirty of a UDP Scan
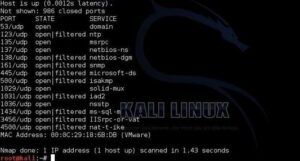 The first step is for the tool to initiate UDP scanning, where it sends a generic UDP packet and waits for a response. Here it does ones of two things: if there is no response, the port is assumed to be open. If an ICMP error packet is returned, the port is considered closed.
The first step is for the tool to initiate UDP scanning, where it sends a generic UDP packet and waits for a response. Here it does ones of two things: if there is no response, the port is assumed to be open. If an ICMP error packet is returned, the port is considered closed.
The second step comes when the scan determines that port to be open. At that point, it sends a UDP packet specific to the service on that port with the goal of detecting the service. In general, this is a packet that associated with the services normally run on that port. This is another point where UDP and TCP differ; UDP services are rarely configured for a non-standard port. An example would be services like DNS (53) and SNMP (161). If one of these ports returns a response, there is a good chance that service is running.
So how can I use Scrutinizer to detect UDP Scans?
By using the current flow data, we can use Scrutinizers Flow Analytics intelligence to monitor for UDP Scans. This algorithm monitors the traffic and alerts when a possible UDP scan is detected. The default threshold is 100 unique scan flows in five minutes. Internal IP addresses that are allowed to scan your internal network, such as security team members and vulnerability scanners, should be entered into the IP exclusions list. Either the source or destination IP address can be excluded from triggering this alarm.
So the next question you need to ask is how can you test Flow Analytics for this type of scan and how would you know what it looks like when you see it? Overall the process is simple. Here are the steps.
First, turn on the Scrutinizer UDP scan intelligence by clicking on ADMIN > SETTINGS > FA CONFIGURATION.
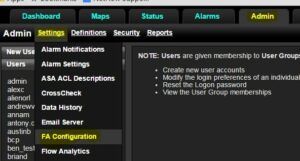
Second, find “UDP Scan” and click on it. The exporters screen should pop up. Add the exporters that you want to monitor.
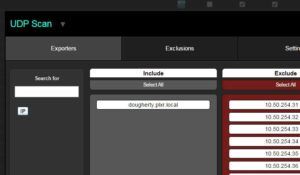
(Note: I also clicked on the setting tab on this screen and reduced my threshold for testing purposes)
Now we need to get some UDP Scan data. I suggest using NMAP to initiate your UDP scan. I used something simple like nmap -sU 192.168.1.0/24
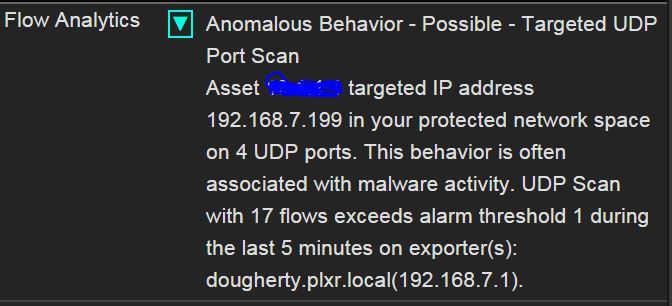 Within a few minutes, I received an alarm! Remember, you can attach multiple notification profiles to each alarm allowing you to be alerted of the event in multiple ways.
Within a few minutes, I received an alarm! Remember, you can attach multiple notification profiles to each alarm allowing you to be alerted of the event in multiple ways.
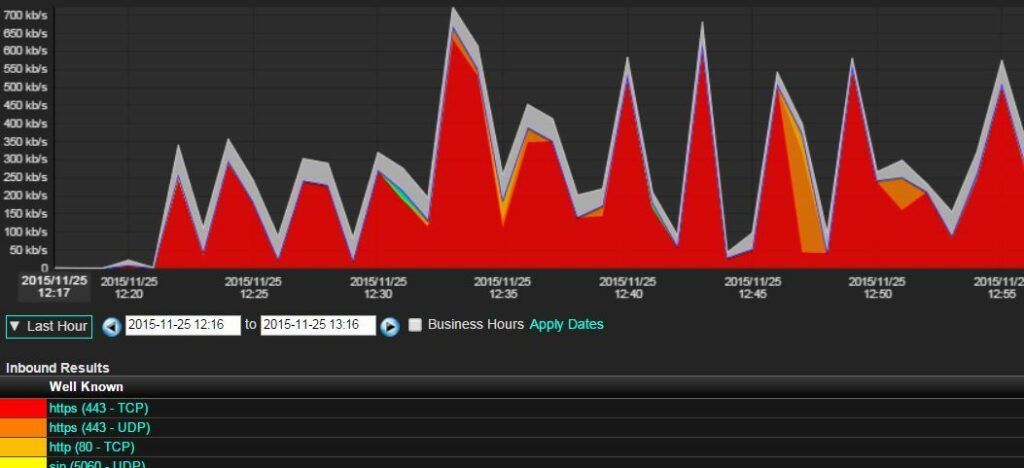 I could also see the UDP data spike on my traffic! So in conclusion, Scrutinizer was not only able to monitor for network abnormalities, but also specific threat patterns – traffic patterns you need to be aware of! I have to be honest with you, setting up tests like this is a lot of fun. Be careful not go overboard with your attacks. I apparently have a few emails from our Security Office related to abnormal traffic from my PC to answer. Sorry Tom Pore!
I could also see the UDP data spike on my traffic! So in conclusion, Scrutinizer was not only able to monitor for network abnormalities, but also specific threat patterns – traffic patterns you need to be aware of! I have to be honest with you, setting up tests like this is a lot of fun. Be careful not go overboard with your attacks. I apparently have a few emails from our Security Office related to abnormal traffic from my PC to answer. Sorry Tom Pore!
To learn more about how Scrutinizer can help you stay vigilant and assist in detecting incidents like this, give us a call and we will be more than happy to help.