The requirements of GDPR can be vague sometimes. I have had quite a few of my customers ask how we help companies with questions about GDPR compliance. Here are the three Scrutinizer abilities that they found to be the most valuable.
Limiting Users’ Views and Abilities
In Bob Noel’s post, “Three GDPR Requirements That Will Have a Big Impact on Your Organization,” the section on role definitions appears the be the most relevant to Scrutinizer.
Limiting what a user can see in Scrutinizer is relatively easy. Just click on Admin (1) > Security (2) > Users. Here, you can create users and define what group permissions (3) they have. You can also determine which authentication engine is used.
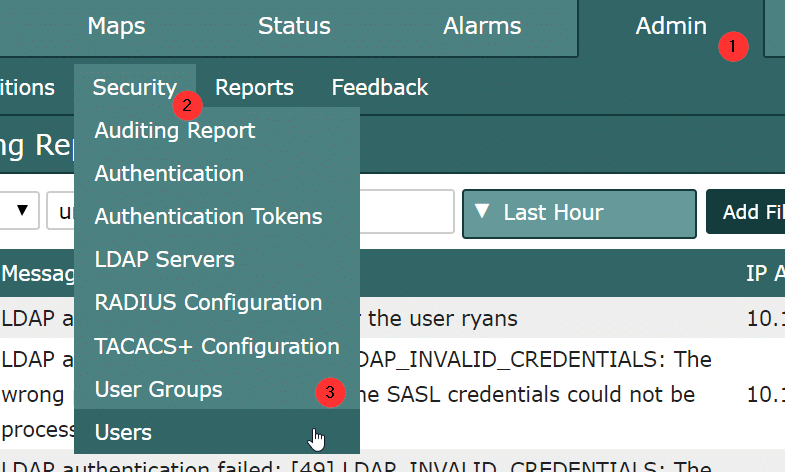
Under the User Group option, you can limit what members of that group can see.
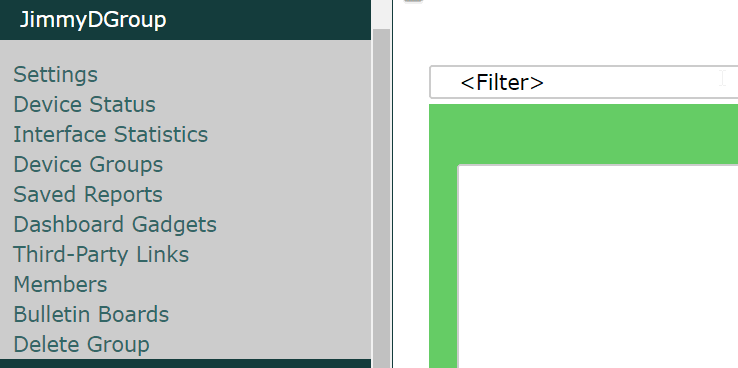
The ability to limit what that user can see
Data Protection Officers can use Scrutinizer’s filtering engine, report designer, or IP groups to hide non-local host information from the user (or vice versa). This prevents network administrators from being able to visualize the remote hosts a local host is talking with. This hides sensitive information such as the site being contacted, but it allows you to keep an eye on the local network activities (i.e. those that are under your administrative domain).
Audit logging
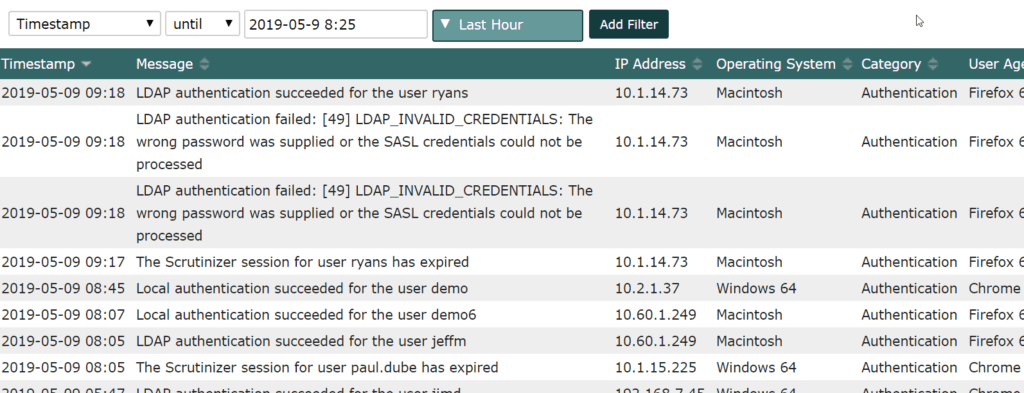
As mentioned in the GDPR post by Bob Noel, being able to report on who has access to Scrutinizer and what they did is one of the requirements. If you click on Admin > Security > Audit Reporting, you can view and filter the audit logs.
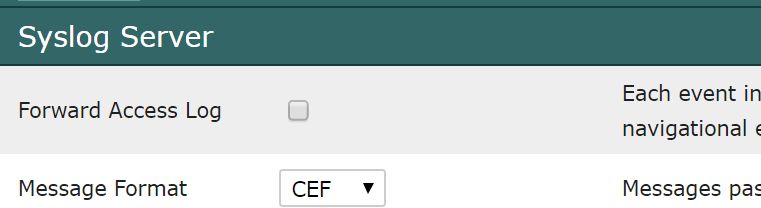
In addition, the syslog server settings (Admin > Settings > Syslog Server) tell Scrutinizer to forward all internal alarms to an external syslog server/SIEM. For GDPR compliance, select the “Forward Access Log” option. That will provide a full account of all user actions, reports run, and filters applied in Scrutinizer.
Right to erasure
GDPR requires that at any time, a user can ask that any information on them be deleted from the database. The administrator of Scrutinizer can delete information from the Scrutinizer database via SQL command line. We are investigating ways to provide a simple way to do this via the GUI or possibly command line.
If your requirements include improving your network monitoring posture, gaining deeper visibility, and meeting GDPR compliance, but you don’t know where to start, why not evaluate Scrutinizer?


