We are very busy this week getting ready for CiscoLive! 2013 in Orlando next week. Since we have a first rate team getting us ready for the show, I had a block of time to put together three primary thoughts I’ve collected regarding mistakes some people make in their cyber threat detection routines.
Everyone needs to understand that no one can completely prevent being hacked by a talented attacker. Even if your firewall is “high and to the right” in the Firewall – Gartner Magic Quadrant, it is impossible to prevent every penetration. Below are suggestions when using NetFlow and IPFIX as part of your cyber threat detection effort.
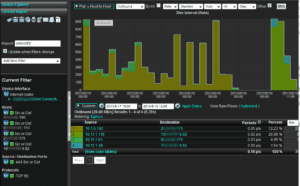
First: Monitor and save all traffic all the time.
When a theft occurs at Walmart, one of the first things the security team does is play back the recorded video. NetFlow and IPFIX are how most companies investigate network threats. A good detective knows where to look for evidence surrounding a crime scene. NetFlow has become the most effective, easy to deploy and most distributed form of surveillance in the network traffic analysis market. Regardless of the solution which initially reports the threat, NetFlow is almost always the turn to solution for investigating the event. Monitor and save all traffic all the time for as long as you can afford. Our solution can save the raw NetFlow and IPFIX data for decades with the only limitation being disk space.
Second: Finding an infection and not continuing to look for more.
When a host is confirmed to be infected with malware, it is important to profile the behavior and understand its traffic patterns.
- What IP addresses is it reaching out to on the internet?
- Are the destination hosts listed on host reputation lists?
- What TCP/UDP ports does it use?
- What time of day does it reach out and how often?
- How much data does it transmit/receive when connections are made?
- Has the infected machine been communicating with internal machines that it has no business connecting to?
- How far back did the behavior start?
Enter the profile into the network traffic analysis solution (I.e. typically a NetFlow analyzer) and search the database for similar behaviors.
Expect to do some leg work here. Comparing traffic patterns, checking logs, looking for RAR files, etc. are just a few examples of the exploratory work necessary to confirm some types of infections.
Third: Don’t turn off the infected machines.
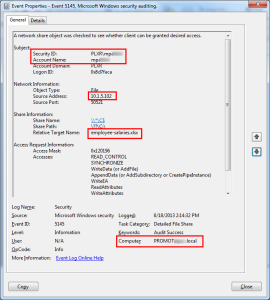
Once you find and confirm infected hosts, don’t remove them from the network as many advanced threats build in mechanisms that help them stay keenly aware of when they are detected. Instead, watch what the infected machine is doing and when it is doing it. In one instance, the customer gave an employee with an infected machine a 2nd laptop for surfing the web and ask that they only use the infected machine for business applications. This helped ensure that the infected machine stayed active on the corporate network but, all internet traffic was closely ‘scrutinized’ by the security team. They setup monitors in their network traffic analysis solution that notified them when the malware woke up and reached out to the internet. They also predetermined the only internal machines the infected PC should be talking to and monitored internal connections as well. When the infected machine reached out to an internal host, they reviewed the logs on the target to determine the reconnaissance strategy behind the malware. What IP address did the access come from? Who’s login and permissions were used? What file(s) were accessed?
Security professionals have come to the realization that there is always an infection somewhere on their network. Living with these infections is reality. Shoplifters steal from department stores everyday and yet these businesses continue on. Information theft is occurring, we need to watch for the repeat offenders, learn their behaviors, collect intelligence on all of the machines involved and then move in to shut the collective effort down.
I hope to see you at booth 747 next week at CiscoLive 2013 in Orlando Florida. Stop by and pickup a NetFlow Sword.